The global average cost of a data breach has fallen to USD 4.44 million, which is a drop of 9% compared to last year, according to the IBM/Ponemon Institute Cost of a Data Breach Report 2025. This figure underlines the importance of strong network defense.
Network security architecture is how an organization designs and deploys a plan to install, maintain, and upgrade its digital-defense infrastructure. It specifies how policies, controls, and technologies can be put together to ensure the safety of critical data and prevent unauthorized access, while responding to real-time cyber threats. Strong architectures lock down every layer, from endpoints to cloud services, in support of operational efficiency, regulatory compliance, and adaptability to evolving risks.
Key Takeaways
- Network security protects hardware, software, and users from cyber threats.
- It covers three layers of protection: technical, physical, and administrative.
- The common defenses include firewalls, VPNs, antivirus, access control, cloud security, and segmentation.
- The security of a network is only as strong as its weakest link.
Core Components of the Network Security Architecture
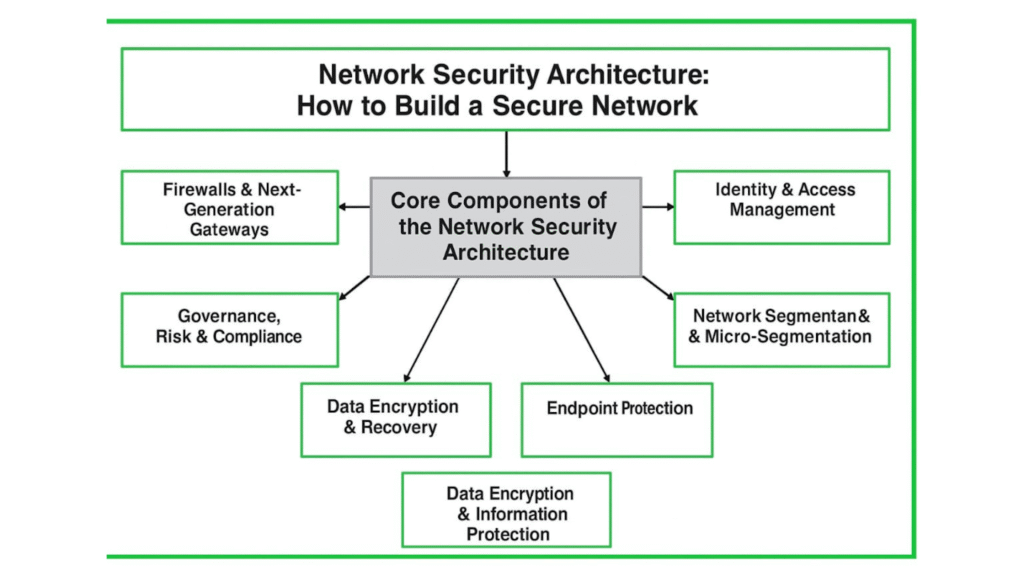
1. Firewalls & Next-Generation Gateways
Firewalls are gatekeepers between trusted and untrusted networks. Traditional firewalls inspect based on ports and packets, while next-generation firewalls add application visibility, intrusion prevention, and threat intelligence integration. These provide granular policy controls with no disruption to legitimate traffic.
2. Identity & Access Management
IAM systems allow for authentication and permit resources based on the role a user plays. Modern IAM uses multi-factor authentication, single-sign-on, and even biometric verification. This is further enhanced by regular access reviews and the elimination of accounts that are inactive, thus assuring that only authenticated users retain access.
3. Threat Detection & Continuous Monitoring
It’s all about visibility. SIEM systems and intrusion-detection monitoring tools analyze real-time data for anomalies and strange behavior. Several of these platforms now apply AI and machine learning to predict the threats and trigger alerts ahead of any damage.
4. Network Segmentation & Micro-Segmentation
Segmentation zones isolate parts of a network from others with defined access rules, reducing the “blast radius” of an attack. Microsegmentation takes it one step further to segment workloads or applications even inside a segment. If one component is compromised, lateral movement will be constrained.
5. Endpoint Protection
Entry points include devices like laptops, smart phones, and servers. These are protected by EDR tools, compliance management, and automatic patching of these nodes. Regularly, vulnerability scanning makes sure devices stay compliant and secure.
6. Data Encryption & Information Protection
Encryption locks data; even if intercepted, it’s unreadable. Most organizations rely on AES for encryption of data at rest and TLS/SSL for encryption in transit. Similarly, one would want effective key-management practices with secure backup practices. Compliance with frameworks like GDPR or HIPAA strengthens protection.
7. Incident Response & Recovery
Even the best systems can be breached. An incident response plan describes how to detect, contain, and restore operations. It spells out roles, communications, and steps toward recovery. Periodic tabletop exercises and simulations reveal gaps, solidify coordination, and minimize lost time.
8. Governance, Risk & Compliance
It ensures that security actions are aligned with business goals through governance. It defines responsibility by documenting policies and tracking performance. Complying with frameworks such as ISO 27001 or the NIST cybersecurity Framework promotes transparency and readiness for changes in regulation.
Challenges in Building a Secure Network Architecture
- Hybrid & Multi-Cloud Environments: Security across on-premises, cloud, and Saas platforms is complex. A unified model of visibility and automation is needed in configuration management to reduce mis-configurations.
- Legacy systems: These are older systems that do not support modern encryption or authentication. Protect them by using segmentation and compensating controls to avoid harming operations.
- BYOD: Unmonitored employee-owned devices can introduce vulnerabilities. Monitoring device compliance and endpoint visibility can provide flexibility without adding risk.
- Balance Security and Productivity: Controls that are too restrictive hinder business. An adaptive least-privilege model enables usability while protecting data.
- Ever-evolving threats: Attack surfaces grow with cloud, AI, IoT; cyber defenses need to outpace emerging vulnerabilities through continuous monitoring, patching, and analytics.
Recommendations to Improve Network Security Architecture
Building a resilient network security architecture requires proactive planning and adaptive strategies. As cyber threats evolve, organizations must integrate modern security principles, automation, and intelligent monitoring to stay ahead of attackers. Below are key recommendations to strengthen your network defense.
Adopt zero-trust principles
Zero trust refers to the idea that no user or device should inherently be trusted. Zero trust is based on continuous authentication, micro-segmentation, and least-privilege access.
Leverage Automation
Automate patching, policy enforcement, and threat analysis. Automation reduces human error and increases consistency in workflows.
Use Behavioural Analytics
Network behavior analytics establish the baseline of activities considered normal and flag deviations to indicate insider threats or hidden malware.
Deploy Deception Technologies
Honeypots or decoy assets are employed to deceive attackers, enable early detection of intrusion attempts, and provide intelligence on methods employed by the attackers.
Design for Scalability
Architecture needs to evolve with your business. Make sure your network architecture can support new technologies and scale without compromising on security posture.
Govern AI Adoption
According to the 2025 report from IBM, 97% of organizations that suffered AI-related breaches were those not having any proper access controls around AI systems. Governance policies for AI-oftentimes called “shadow AI” when unmanaged-must be a part of your security architecture.
Prioritize Data & Identity
According to the IBM report, identity security of both human and machine, and protection of data are the two important cost drivers of a breach. Organizations using AI and automation extensively saved on an average USD 1.9 million per breach.
Final Thoughts
A strong network security architecture is pivotal to digital safety. It provides a shield for sensitive data, supports business continuity, and fosters stakeholder trust. Layers of defence embedded in the design would be crucial, continuous monitoring, good governance principles, and incident preparedness minimize risk and allow rapid responses if security breaches take place. With threats continuing to multiply and attack surfaces expanding in an increasingly digital world, proactive architecture design is no longer optional, it’s essential.
Related Link:
- Types of Network Security and How Each One Protects Your Data
- What is Network Security?
- What is 5G Network Security?
- What is Zero Trust Security?
- What is EDR? Endpoint Detection and Response
- 7 Types of Firewalls to Secure Your Network
FAQs
What does network security architecture include?
It includes policies, frameworks, and technologies such as firewalls, encryption, access controls, and monitoring systems that work together to protect the network infrastructure of an organization.
How does network security architecture differ from cybersecurity?
Cybersecurity is the broad area that encompasses all digital protection efforts. Network security architecture is narrower; it concerns how security controls are organized and implemented throughout the network.
What makes a strong network security architecture?
It is layered, adaptive, and aligned to business goals. It integrates advanced detection, automation, and compliance frameworks that assure security and performance.