“Fortinet reported that 95% of companies are concerned about cloud security.”
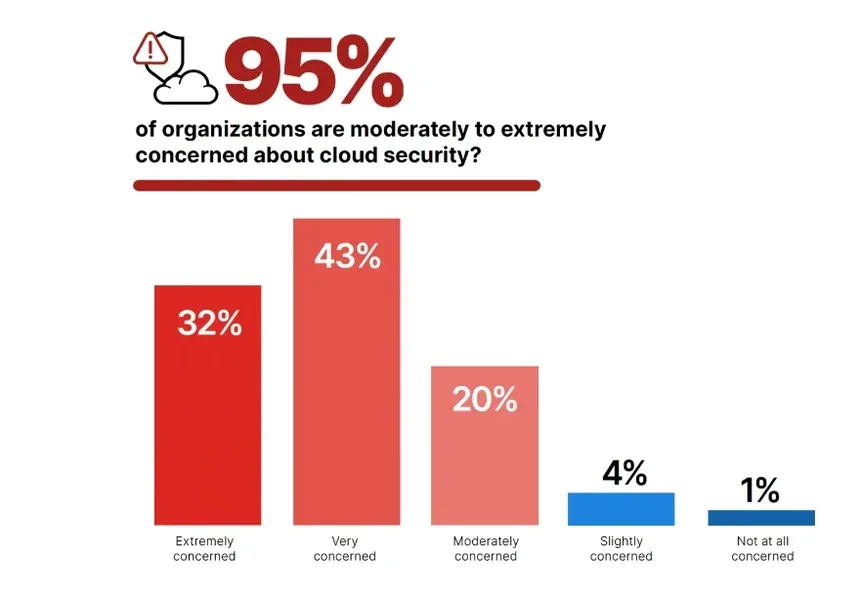
Source: Cloud Zero
It’s alarming evidence that says risks in cloud network security are increasing. Organizations are concerned about their reputation and the potential losses that they face from such vulnerabilities.
A huge number of organizations are looking up to cloud security to enhance their cloud computing services. Cloud Network Security (CNS) protects the virtual territory of cloud-based companies. It is a complete package that consists of tools, guidelines, and procedures to defend cloud-based networks against intrusions, data breaches, and other cyber risks. On one hand, it provides robust security, but when we flip the coin, the risks of cloud network security also become visible.
When risks come into life, we also look for solutions to lighten the weight of potential vulnerabilities. Considering we are going on a ride of threatening risk but will also explore the solutions.
Top 9 Cyber Network Security Risks and Their Solutions.
Before delving into specific cloud network security risks, let us first look at the overall picture of cloud security vulnerabilities, as depicted in the chart below.
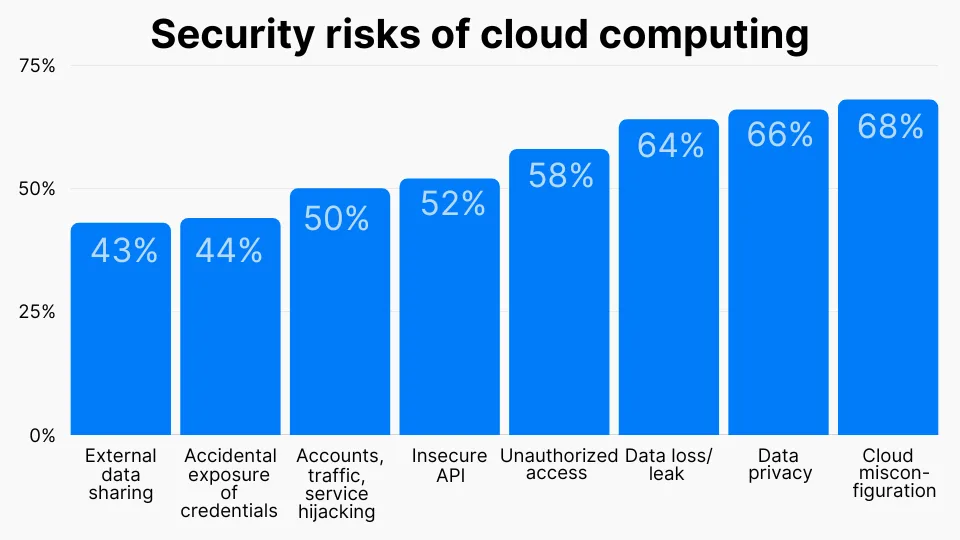
Source: Headphones Addict
It represents that data privacy and misconfiguration are the leading risks in the cloud security world. Let’s understand the top risks of cloud network security with their solutions.
Risk 1: Data Breaches
Data breaches occur when your sensitive data in the cloud gets exposed to unauthorized individuals. They typically acquire access when you leave vulnerabilities such as weak passwords, poorly configured cloud settings, or application bugs.
How to Address:
- Use encryption for both data at rest and in transit.
- Enable Multi-Factor Authentication (MFA), which adds extra protection by requiring multiple verification steps from all users.
- Implement the concept of least privilege, which entails restricting access to personnel. It guarantees that users only have access to essential resources.
Risk 2: Misconfigured Cloud Settings
Misconfiguration includes leaving storage buckets available to the public and utilizing default passwords. They often provide users with excessive permissions and are the primary cause of cloud vulnerabilities.
How to Address:
- Educate and train employees on secure configuration procedures.
- Establish stringent protocols for configuring and maintaining cloud resources.
- Identify and fix misconfiguration using automated tools such as AWS Config, Azure Security CCenter, and CSPM.
Risk 3: Account Hijacking
Hackers use social engineering, weak passwords, and phishing attacks to get access to user cloud accounts. They engage in illegal or malicious behavior, harming the company’s data and the trust it has created over the years.
How to Address:
- Encrypt sensitive data both in transit and at rest in the cloud.
- Establish robust authentication procedures for cloud service data access.
- Restrict IP addresses for cloud applications so that users only access corporate networks.
Risk 4: Malware and Ransomware Attacks
Attackers leverage weaknesses in cloud infrastructure, user accounts, or applications to inject malicious code. Encrypting data on cloud servers, disrupting services, or demanding ransoms renders it inaccessible to legitimate users.
How to Address:
- Divide a network into smaller subnets to increase security and performance.
- Install effective antivirus and anti-malware software on all cloud-connected devices.
- Maintain regular backups to enable speedy recovery in the event of a ransomware attack.
Risk 5: Denial of Service (DoS) Attacks
DoS assaults are the most damaging type of attack because they overwhelm the cloud network with excessive traffic, causing services to become unavailable. This disrupts the business system, perhaps resulting in financial loss.
How to Address:
- Use solutions like AWS Shield or Cloudflare to guard against such assaults.
- Use load balancers to distribute traffic, maintain a flow, and prevent overload.
- Continuously monitor network traffic for irregularities by establishing firewalls and intrusion detection systems.
Risk 6: Lack of Visibility and Control
A lack of visibility and control has an impact on the organization’s operations and planning in terms of data, services, users, and security measures. They must have knee knowledge to carry out the incident response strategy. It also creates business risks in terms of governance, compliance, and security.
How to Address:
- Splunk or Datadog can help you acquire real-time insights into cloud activity.
- Consolidate logs and events into a single monitoring dashboard, and audit them on a regular basis.
- Understand and carry out the responsibilities shared by you and your cloud provider.
Risk 7: Weak API Security
An application programming interface (API) provides users with direct or indirect access to cloud services and infrastructure. Cloud services commonly provide APIs, allowing customers to interface with their cloud environments. On the other hand, poorly secured APIs damage cloud network security by granting hackers unauthorized access to cloud resources.
How to Address:
- Secure your OAuth2 authentication tokens and API keys.
- Follow a security-by-design strategy across the development process.
- Implement API rate limiting (limiting the number of API calls per user) to prevent abuse.
Risk 8: Compliance Violations
Compliance violations in cloud network security constitute a substantial risk because failing to conform to data protection rules such as GDPR, HIPAA, or CCPA can result in serious legal and financial penalties, reputational harm, and potential data breaches.
How to Address:
- Educate employees about data privacy regulations for handling sensitive information.
- Perform frequent tests of your cloud environment to identify and address potential compliance gaps.
- Implement strong identity and access management (IAM) practices, including MFA and least privilege access.
Risk 9: Shadow IT
Shadow IT occurs when employees use IT system devices, software, applications, and services without explicit organizational approval. They bypass the security protocols of IT departments, potentially exposing the organization to security risks, data breaches, and compliance violations.
How to Address:
- Provide secure, sanctioned alternatives to meet user requirements.
- Encourage a transparent environment where employees feel comfortable sharing their tech needs.
- Implementing cloud access security brokers (CASBs) or similar tools to detect and manage unauthorized services.
Conclusion
Cloud network security requires a proactive approach against emerging cyber threats. Regularly reviewing security policy and implementing the appropriate technologies are critical steps in staying ahead of evolving threats. Begin safeguarding your cloud network today.
In the digital age, a strong defense is your most valuable asset!
Visit our cybersecurity page; we have the best guides for you.
If you’re interested in contributing, submit your guest post and Write for Us.