Cloud Security Posture Management (CSPM) is a risk identifier that monitors cloud infrastructure. It also detects data breach threats, misconfigurations, compliance violations, and other potential vulnerabilities in cloud services, web applications, and resources. Nowadays, CSPM is essential, indicating the importance and benefits it provides to businesses.
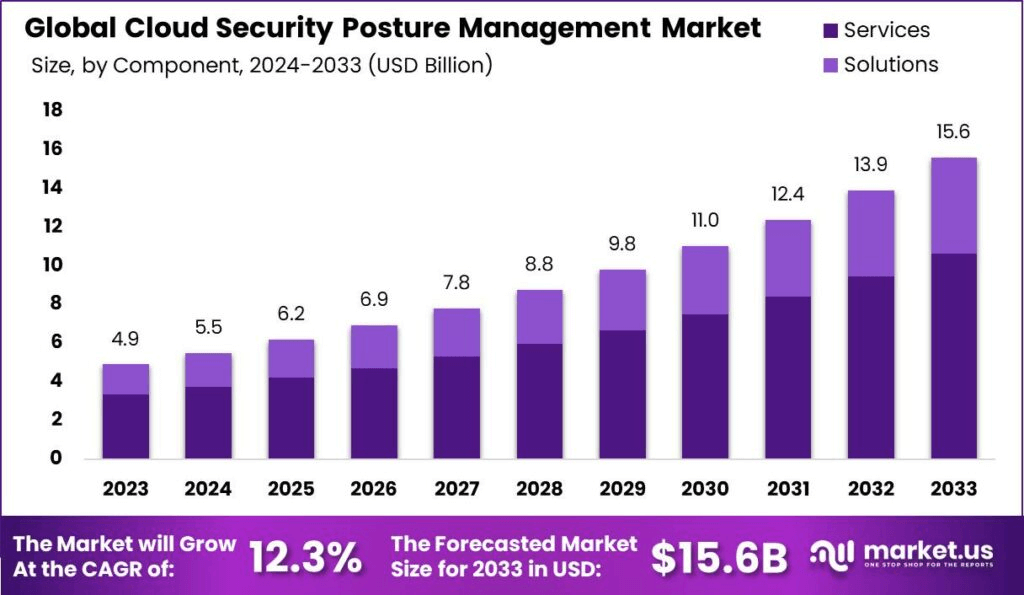
According to the report, the global Cloud Security Posture Management (CSPM) market is expected to reach USD 15.6 billion by 2033. Prediction says it will maintain a consistent CAGR of 12.3% from 2023 to 2033.
CSPM systems handle assessment of risk visualization, incident response, remedial recommendations, compliance monitoring, and DevOps integration. They offer services across multi-cloud and hybrid systems and infrastructures.
The cloud infrastructure that CSPM inspects may include:
- Infrastructure-as-a-service (IaaS)
- Platform-as-a-service (PaaS)
- Software-as-a-service (SaaS)
- Containers and Serverless code
Cloud Security Posture Management (CSPM) is an automated tool that guarantees cheaper costs, strengthens security, and reduces exposure to risk in cloud environments instead of using manual security teams. On the other hand, SaaS Security Posture Management (SSPM) is used to ensure the security and compliance of Software-as-a-Service (SaaS) applications.
Let’s explore why CSPM is needed, how it works, its capabilities, and its benefits.
Why is CSPM Needed?
Cloud systems are growing increasingly popular among businesses because they offer flexibility and efficiency; yet, the risk of cyber threats is increasing over time. Data breaches are the primary cause of damage. Misconfigurations and internet apps are the top three leading causes of data breaches. According to Verizon’s 2023 Data Breach Investigations Report, data breaches account for more than 20% of the total.

A Cloud Security Posture Management system protects you from:
- Misconfiguration: Misconfiguration is the leading cause of data breaches. It can occur unintentionally or due to poor management of several networked resources such as containers, serverless operations, and Kubernetes. CSPM automatically patches issues by monitoring for misconfigurations and spotting anomalous traffic.
- Lack of visibility: Lack of visibility leads to security difficulties because businesses are usually unaware of their attack surface. The problem becomes more complex when a company has shadow IT, or cloud services that employees utilize without permission. CSPM scans cloud deployments and alerts security staff to observe any asset misconfigurations.
- Compliance and regulation issues: An organization’s lack of compliance and regulation leads to a weak infrastructure. Considering this, CSPM solutions provide visibility into cloud architecture, including data encryption, network configurations, access controls, and other security measures. They also automatically detect potential violations, such as an excessive number of users accessing a database.
How does CSPM work?
Cloud Security Posture Management (CSPM) solves security issues, vulnerabilities, and regulatory non-compliance in cloud services. The CSPM tool regularly checks cloud service, and alerts security personnel to detect potential gaps.
CSPM technologies help organizations to:
- Identify misconfigurations and fix them in auto mode.
- Visibility in policy enforcement.
- Reduce the probability of false positive notifications.
- Ensure adherence to all organizational security policies.
- In multi-cloud systems, make regulations public and ensure uniformity
- Enable the automatic and one-click rectification of detected.
- Conduct risk assessments using recognized frameworks, such as ISO and NIST.
- Audit to guarantee compliance with legal obligations including GDPR, PCI DSS, and HIPAA.
Security standards are a priority of any organization, and hazards that cause the failure of security due to workload. CSPM helps to protect from such attacks.
Key Capabilities of CSPM
Cloud Security Posture Management’s key capabilities allow you to understand possible solutions to protect an organization from risk.
- Check regularly for security misconfigurations, compliance violations, and vulnerabilities.
- Map cloud infrastructure detects hazards.
- Alert security teams to possible dangers.
- Identify software weaknesses that attackers could exploit.
- Analyze and standardize data sources to provide centralized insight across cloud and multi-cloud systems.
- To minimize human error, compare cloud setups with industry standards and other pre-built rules.
- Monitor cloud environments in real time for anomalies that may signal malicious activities.
Benefits of Cloud Security Posture Management CSPM

CSPM tool benefits organizations by reducing costs, risk protection, continuous monitoring, and updating with time.
Here, we have essential benefits that an organization enjoys under CSPM:
- Threat detection: CSPM helps detect threats regularly, including real-time visibility and automatic discovery of misconfigurations, vulnerabilities, and security gaps before an attack. The CSPM tool detects risk by connecting links based on a detailed examination of the cloud infrastructure. It allows security teams to identify dangers actively, reducing the attack surface.
- Ensure effective compliance regulations: CSPM enables organizations to comply with regulations such as PCI DSS, HIPAA, and GDPR. It monitors compliance implementation constantly to guard against misconfiguration or vulnerabilities which could lead to noncompliance concerns and a penalty. It ensures the best possible detection and repair actions following industry standards.
- Policy enforcement and automated remediation: Cloud Security Posture Management (CSPM) enables automated remediation to address any identified security threat. It controls your cloud security policies and ensures your virtual machines and PaaS services stay compliant despite regulation alterations.
- Cost optimization: Through CSPM’s analysis of cloud resources and configurations, organizations can identify unused or underutilized assets, optimize resource allocation, and reduce cloud spending. By eliminating unnecessary expenses and optimizing performance, CSPM contributes to overall cost efficiency.
Conclusion
Cloud Security posture management (CSPM) is a significant tool for organizations to protect against security risks and threats. It automates danger identification and monitors cloud infrastructure, resulting in updated systems. It protects organizations from security risks and penalties by adhering to regulations and executing compliance measures.
If you want to stay up to date on the latest cyber security trends, updates, and news, visit Daily Digital Grind and expand your knowledge now!
FAQs
What is Cloud Security Posture Management (CSPM)?
Cloud Security Posture Management (CSPM) is a tool that analyzes cloud infrastructure for data breaches, misconfigurations, compliance violations, and other potential flaws in cloud services, web applications, and resources.
What are the benefits of CSPM?
CSPM enhances visibility into cloud infrastructure, reducing the risk of breaches. It ensures compliance with regulations and standards, streamlines security operations through automation, and provides real-time threat detection.
What is the difference between CSPM and SSPM?
CSPM is for analyzing cloud infrastructure, and SSPM is for ensuring the security and compliance of SaaS applications.