Cloud computing has been the lifeblood of modern business operations. Business monoliths to start-ups, almost all enterprises use the cloud for storing data, hosting applications, and serving services quicker and at lower cost. Cloud is great in terms of scalability, elasticity, and cost-effectiveness. But the instant companies upload heavier and heavier loads and sensitive data into the cloud, so do the chances of security breaches.

Cloud environments are prime targets for cyber-attacks because they possess a large attack surface and sensitive data that they host. Misconfigurations, inadequate access controls, and sophisticated threats like ransomware make the cloud environments vulnerable to attack.
This is where cloud security comes into play. Cloud security allows organizations to harness the potential of the cloud without compromising themselves. By 2025, when the majority of organizations are likely to be running hybrid and multi-cloud setups, cloud asset protection is no longer a choice-survival depends on it.
What is Cloud Security?
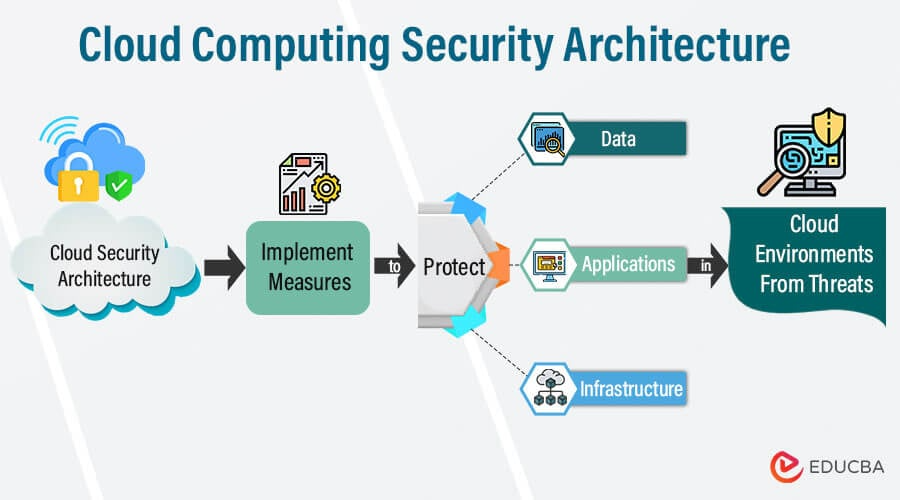
Cloud Security is the set of services, processes, technologies, policies, and services used to safeguard cloud-based applications, data, and systems. Its primary purpose is to avoid downtime, unauthorized use, data loss, and regulatory violations.
While on-premises security must fight existing threats, cloud security must fight emerging threats. The cloud infrastructure is distributed, shared, and dynamic. Data can travel from private clouds, on-premises servers, to public clouds in seconds.
In short, cloud security allows businesses to drive digital transformation without sacrificing confidentiality, integrity, or availability.
Shared Responsibility Model in Cloud Security
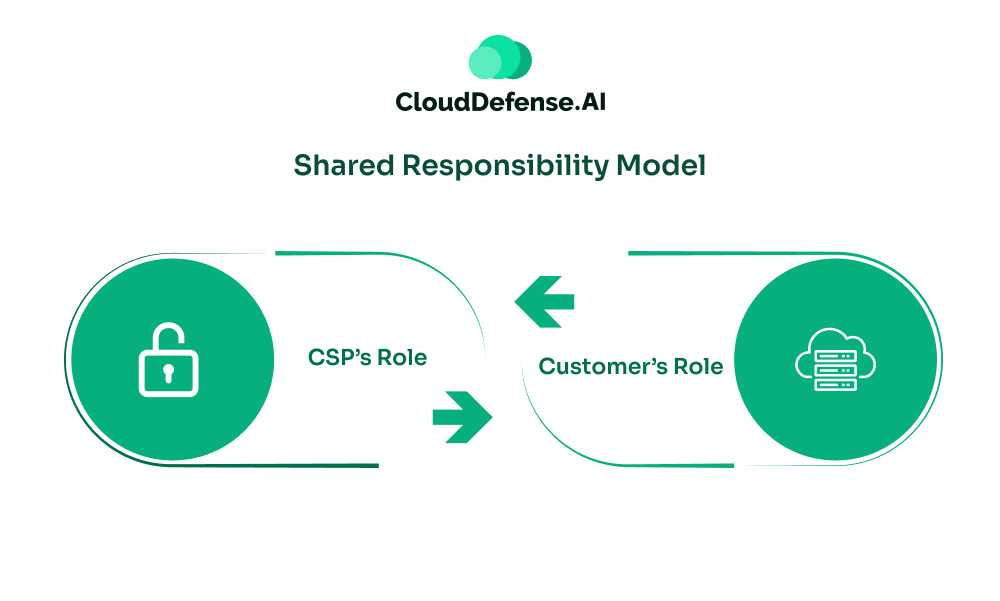
Shared Responsibility Model is one of the most significant topics of cloud security. Cloud security is neither in provider or customer space alone instead, it’s something they do jointly and with shared responsibility.
Cloud Provider Responsibilities
- Protection of physical infrastructure; data centers, hardware, and networks.
- Provisioning service availability via patching, updates, and redundancy.
- Protecting cloud-hosted infrastructure from external attack.
Customer Responsibilities
- User account, access level, and authentication management.
- Protecting sensitive information in storage or in transit in the cloud.
- Securely deploying cloud services to prevent misconfigurations.
- Enabling regulatory compliance.
Service Models and Responsibility Split
- Infrastructure as a Service (IaaS): Infrastructure owned by the provider, OS, applications, and data owned by the customer.
- Platform as a Service (PaaS): Platform and infrastructure owned by the provider, applications and data owned by the customer.
- Software as a Service (SaaS): The vendor owns all but customer identity, access, and use of data.
There is a requirement to deploy and understand the shared responsibility model as a means of keeping expensive breaches at bay.
Cloud Security Top Challenges in 2025
Cloud, although never quite as useful, has new threats. Organisations have to combat the below threats:
1. Increased Attack Surface
The cloud integrates devices, services, and users globally, and it has an enormous attack surface due to that. Attackers target bad access points, non-patched application software, and exposed APIs.
2. Visibility and Monitoring
Companies are unaware in multi-clouds where their data resides and with whom they are trading it. Visibility hinders one’s capacity to identify something unusual.
3. Misconfigurations and Human Errors
One poorly configured security group or storage bucket leaks sensitive information to the public internet. Misconfigurations are the number one cause of cloud breaches, research has found.
4. Dynamically Changing Workloads
Clouds scale vertically and horizontally dynamically, which introduces transient workloads (i.e., serverless, containers). Traditional security products get left behind.
5. Mismanagement of Identity and Access
Inadequate user role management and poor authentication expose organizations to account takeovers. Overprivileged accounts accelerate insider threat risk.
6. Governance and Compliance Challenges
It is hard to meet GDPR, HIPAA, or PCI DSS in the cloud due to constantly changing workloads and poor visibility for audits.
7. Next-Generation Cyber Threats
Cloud native next-generation threats like ransomware, Phishing, zero-day attacks, and AI-powered attacks hit cloud infrastructure. They need advanced detection and response.
Pillars of Cloud Security
The best cloud security solution is based on a handful of large pillars. They collectively form a robust defense mechanism.
1. Identity and Access Management (IAM)
- Enforce strong authentication, for example, Multi-Factor Authentication (MFA).
- Enforce the principle of least privilege, users receive only the access they actually need.
- Inactive accounts and permissions must be revoked on a regular basis.
2. Data Protection and Encryption
- Encrypt employee data at rest, transit, and usage.
- Enforce advanced key management systems.
- Regular backup of data to counter the impact of ransomware.
3. Cloud Network Security of Zero Trust and Segmentation
- Implement Zero Trust Architecture: never trust, always verify.
- Implement micro-segmentation to workload segmentation.
- APIs, firewalls, and VPN gateways being secured.
4. Cloud Workload Protection
- Implement Cloud Workload Protection Platforms (CWPPs).
- Real-time monitoring of suspicious workload activity.
- Implement strict policy across hybrid and multi-cloud.
5. Threat Detection and Response
- Use AI and ML for detection of unknown threats.
- Leverage Security Information and Event Management (SIEM) tools for centralized monitoring.
- Provide automated incident response to remediating in a timely manner.
6. Continuous Compliance and Governance
- Implement compliance checking automation through Cloud Security Posture Management (CSPM).
- Enforce cloud policies based on standards such as ISO, NIST, and GDPR.
- Enforce real-time misconfiguration and non-compliance notifications.
Read More: What is Cloud Security Posture Management (CSPM)?
New Cloud Security Approaches
The following approaches should be implemented by organizations in order to effectively respond to changing threats:
1. Implement Zero Trust Security
Zero Trust requires strong authentication for everyone and everything, anywhere. Zero Trust decreases insider risk and lateral attacker mobility.
2. DevOps Security (DevSecOps) Integrate
Bake security in every phase of the development lifecycle. Application code scanning with automation, secure CI/CD pipelines, and vulnerability scanning lower risk early.
3. Use Cloud Security Posture Management (CSPM)
CSPM tools scan cloud configurations continually, enforce compliance, and remediating automatically misconfigurations.
4. Strengthen Identity and Authentication
Implement MFA, adaptive auth, and biometrics. Protect identity for multi-cloud environments through identity automation.
5. Automate Threat Detection and Response
Implement AI-driven anomaly detection with automatic remediation or containment.
6. Build an Incident Response Plan
Incident plan with written procedures, roles, and recovery plans. Practice and update the plan on a regular basis.
Recommended Read: Top Risks in Cloud Network Security and How to Address Them
The Future of Cloud Security
Cloud security will continue to improve as threats change and technology advances. Some of the most important future trends are:
- AI and Predictive Analytics: Detection of threats before execution.
- Confidential Computing: Protection of data-in-use in a secure manner.
- Homomorphic Encryption: Allowing computations on ciphertext without decrypting it.
- Secure Access Service Edge (SASE): Intersection of networking and security for cloud-native applications.
- Cloud-Native Security: Preparing tools for Kubernetes, containers, and serverless environments for the future.
These businesses will keep pace at the forefront of defending their assets.
Conclusion: Creating a Resilient Cloud Security Framework
The cloud revolutionized business, but along the way it did present some added threats. Cloud security is not a product. It’s an iterative, multi-layered process.
Through leveraging knowledge of the shared responsibility model, problem-solving, and embracing new paradigms such as Zero Trust, CSPM, and DevSecOps, organizations can be assured in the cloud.
In 2025 and the years to come, cloud security is not just about defense, it is about facilitating growth, trust, and innovation.
To explore more insights like this, visit our Cyber-security Page.
If you’re passionate about tech, networks, and digital infrastructure, Write for Us and share your voice with our audience.
FAQs
What is cloud security?
Cloud security protects data, applications, and cloud infrastructure from cyber attacks and misuse.
Why is cloud security important?
It offers business resiliency, protects sensitive data, enforces compliance, and builds customer trust.
Which tools improve cloud security?
CSPM (Cloud Security Posture Management), CWPP (Cloud Workload Protection Platforms), IAM solutions, SIEM tools, and AI-based threat detection.