In this digital-first age, the old fortress ideology of network security just isn’t enough. With cloud services, remote work, BYOD and advanced threat actors, organizations need to adopt a security model that doesn’t trust anyone and anything within the network by default. That model is Zero Trust Security.
Zero Trust is not a buzzword, it’s a strategic design and approach predicated on the notion that each access request (user, device, or app) needs to be authenticated, approved, and constantly validated before, during, and after accessing resources.
- What Is Zero Trust Security?
- Core Principles of Zero Trust (NIST SP 800-207)
- How Zero Trust Works
- Zero Trust vs Traditional Network Security
- Benefits of Implementing Zero Trust Security
- Steps to Implement Zero Trust in Your Organization
- Real-World Use Cases for Zero Trust
- Challenges & Best Practices
- The Future of Zero Trust Security
- Conclusion
- FAQs
What Is Zero Trust Security?
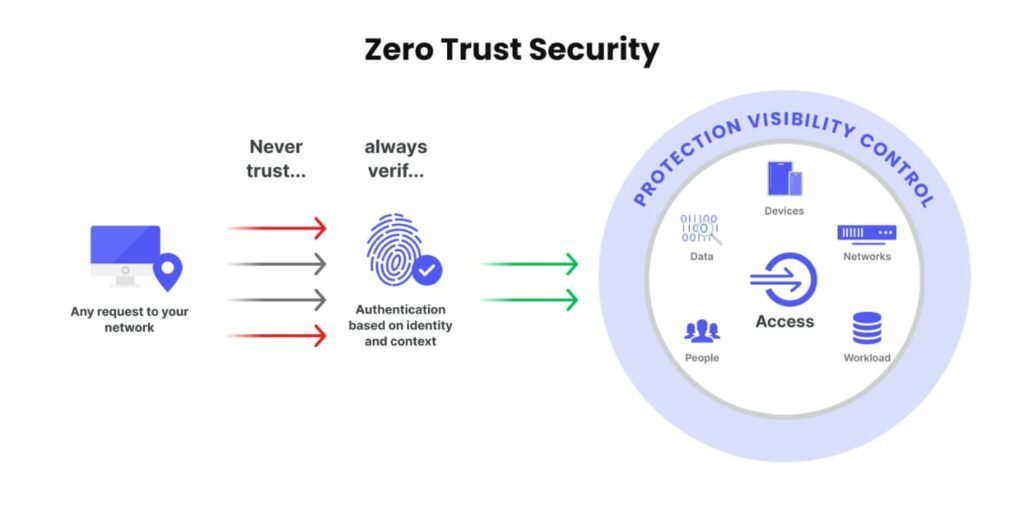
Zero Trust Security is:
- Treating each user, each device, each application and each access request as potentially hostile.
- Confirms identity and health of the device prior to access always.
- Granting only the least privilege to accomplish the task, and always watching for risk or out-of-behaviour.
In practice, Zero Trust abandons the concept of a trusted “interior” network edge and instead concentrates on protecting the resources themselves, wherever they are located on-premises, in the cloud, in remote offices or in hybrid environments. This is outlined clearly by NIST in its SP 800-207 document “Zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location.”
Core Principles of Zero Trust (NIST SP 800-207)
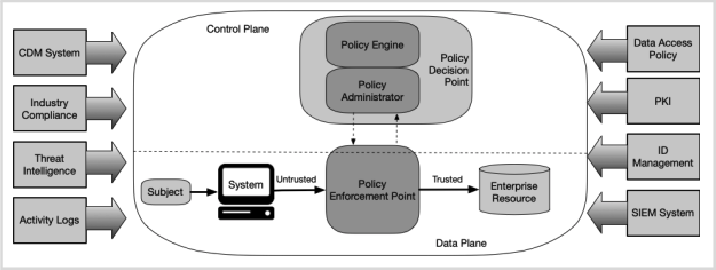
The definitive NIST SP 800-207 (Zero Trust Architecture) gives the basis for a Zero Trust framework. Based on NIST and complementary sources, the main principles are:
- Continuous verification: Don’t trust by default, authenticate every request. This implies identity, device posture, access context and so on must be checked at each session.
- Least privilege access: Users and devices must only be granted the privileges needed to accomplish their work, nothing more, nothing less. This lessens the likelihood that a breached account can move sideways and wreak havoc.
- Assume breach: Instead of thinking you are secure within a perimeter, assume an adversary is already inside. This mindset encourages tighter segmentation, monitoring and response.
NIST also lists seven axioms in SP 800-207 which detail how businesses should conceptualize Zero Trust. For instance, treat all computing services and data sources as resources, secure communications everywhere, provide access based on dynamic policy, measure and monitor asset posture, etc.
How Zero Trust Works
For an organization to use Zero Trust, a variety of interrelated elements and processes converge. Here’s a simplified way it usually works:
- Identity & authentication: Each user (and service) needs to verify who they are, by utilizing robust identity controls (password + multi-factor authentication, or passwordless via biometrics, etc.).
- Device and application authentication: The requesting device or application needs to be validated: is it known, up to date, in compliance with policy, malware-free?
- Access decision / policy enforcement: After considering the user identity, state of device, requested resource, location and context, a decision is reached: grant, deny or grant with limitations.
- Micro-segmentation & least-privilege access: Even when access is permitted, the user is given no more than what they require, for only the session or task, and hopefully cannot travel sideways to other systems unrestrained.
- Monitoring, analytics & response on a continuous basis: The session is tracked, activity is checked in real-time (or near real-time) for suspiciousness, and automated response or re-verification can be initiated if risk emerges.
This cycle highlights the fact that Zero Trust isn’t a single authentication but a continuous series of verification, enforcement and monitoring.
Zero Trust vs Traditional Network Security
Under the old perimeter-based security model, once you were “inside” the network you tended to be trusted blindly (or at least more trusted). The perimeter (firewall, VPN gateway, etc.) was the primary line of defense. However, this model has inherent weaknesses today, remote work, cloud applications outside the traditional network, mobile users, unmanaged machines and advanced lateral movement by attackers.
By way of contrast, Zero Trust flips that perspective, whether you’re on the inside or the outside of the physical network is irrelevant. All access is equal. The trust is never granted. And what you end up with is a much better fit for modern hybrid, distributed reality.
Benefits of Implementing Zero Trust Security
Implementing a Zero Trust approach has real advantages for organizations:
- Smaller attack surface: Verifying all access and only providing what is required reduces the number of exploitable entry points.
- Enhanced protection for cloud, hybrid and remote environments: Zero Trust is built for “borderless” environments where resources can reside in various locations.
- Improved resistance to identity-based attacks: Because identity verification is at the core, and least-privilege enforced, attacks that target credentials or devices are more difficult to leverage.
- Improved compliance and audit preparedness: With detailed access control, auditing of all sessions, and insights into access behavior, organizations can easily satisfy regulatory and governance needs.
- Improved detection and response: Continuous monitoring and analytics allow security teams to identify anomalies and respond promptly, reducing damage in the event of breach.
- Enables business agility: Since the model moves away from the conventional “inside/outside” divide, businesses are able to implement cloud, mobile and third-party access models with greater certainty.
Steps to Implement Zero Trust in Your Organization
While the precise route will vary depending on the enterprise’s size, architecture and maturity, the following phased approach conforms to best practice and sources like the cybersecurity and Infrastructure Security Agency (CISA) Zero Trust Maturity Model.
Preparation & asset-mapping
- Enumerate and classify your users, devices, applications and data.
- Create maps of existing access flows and security controls.
- Identify where implicit trust is present (e.g VPN access with little or no strong authentication).
Identity & access hardening
- Implement strong authentication (MFA or stronger) for everyone.
- Enforce identity management and governance for human and non-human identities (services/apps).
- Establish roles, privileges and access policies in accordance with least privilege.
Micro-segmentation & controls of resources
- Segment the network, applications and workloads to thwart lateral movement.
- Apply all computing services, devices and data as resources to be protected, not merely network zones. That follows NIST principles.
- Encrypt and authenticate all communications (internal, external).
Continuous monitoring & analytics
- Deploy tools that offer visibility into device posture, user behavior and network traffic.
- Analyze anomalies, apply adaptive controls and dynamically re-evaluate privileges.
- Respond using automation against elevated risk (e.g., requesting re-authentication, session blocking or isolating devices).
Optimization & cultural change
- Modify policies and workflows from feedback, lessons and changing threats.
- Train employees and operations teams; Zero Trust is both a technology and a cultural transformation.
- Implement metrics, maturity assessments (e.g., CISA’s maturity model) to track progress.
Real-World Use Cases for Zero Trust
- Remote and hybrid workforce environments: With workers outside office networks, resources are consumed from diverse locations/devices. Zero Trust provides equal security.
- Cloud-first/multi-cloud environments: As applications are spread out across various cloud vendors and on-premises, the network boundary gets compromised Zero Trust secures resources directly.
- Third-party/supply chain access: Outside vendors or partners usually introduce risk. With Zero Trust, you authenticate them each time and limit privileges to the absolute minimum.
- Existing legacy systems: Even if the older systems need to be kept, you can encapsulate them in identity-based controls and micro-segmentation instead of “trust” them since they are within a network.
- Ransomware and lateral movement defense: In case an attacker compromises initial credentials, the least-privilege and segmentation inherent in Zero Trust inhibit their move to spread in the network.
Challenges & Best Practices
Though the advantages are genuine, Zero Trust is not an easy thing to implement. Some standard challenges and best practices:
- Challenge: Shift in thinking Organizations have to leave behind old presumptions (“inside = safe”) to adopt the new culture of “never trust, always verify.” Best practice: executive sponsorship, well-defined roadmap, begin small with high-value assets.
- Challenge: Integration and complexity Merging identity systems, device posture tools, segmentation and monitoring across hybrid environments might be challenging. Best practice: employ vendor-neutral frameworks (such as NIST SP 800-207) and develop phased implementation.
- Challenge: User experience & business impact Too aggressive controls can irritate users. Best practice: balance usability and security, employ adaptive controls (e.g., higher checks only when risk is on the rise).
- Challenge: Legacy systems Older applications might not have strong authentication or segmentation capabilities. Best practice: implement compensating controls (gateway/API wrappers, isolation) when planning modernisation.
- Best practice: Continuous review and adaptation Threats change over time, so do your controls. Monitoring, analytics and policy changes should be continuous.
- Best practice: Measure maturity & progress Utilise models (e.g. CISA Zero Trust Maturity Model) to check where you are and where you’re headed.
The Future of Zero Trust Security
Ahead, Zero Trust will become a standard requirement for organizations instead of an optional high-end security model. Key trends:
- AI/ML-powered verification and behavior analytics: Machinery will more and more use machine learning to dynamically assess trust scores in real time, rather than static checks.
- Adaptive authentication and context-aware access: Access decisions will include several contextual considerations (device health, location, network risk, user behavior) dynamically.
- Quantum-safe and next-generation encryption: With quantum computing on the horizon, Zero Trust systems will require encryption and identity systems capable of handling future threats.
- Government and regulatory requirements: Public sector organizations and large businesses are experiencing more mandates to deploy Zero Trust (such as federal agencies adopting NIST SP 800-207).
- Wider deployment within small and medium organizations: As services and tools mature, even smaller businesses will be able to deploy Zero Trust without enterprise-level complexity.
In brief: the Zero Trust model will most probably become the default for cybersecurity plans in the future.
Conclusion
In a time when virtual perimeters are fading and threats are becoming more cunning, the classic “fortress” approach to cybersecurity is no longer sufficient. Zero Trust Security provides a contemporary, agile method based on the never trust, always verify guidelines. By considering every user, device and access request untrusted by default, applying least-privilege, presuming breach and monitoring behaviour constantly, organizations can drastically improve their cyber stance.
Implementing Zero Trust is not a matter of purchasing tools, but of changing mindset, architecture and operations. With guiding frameworks like NIST SP 800-207, the path may be complicated, but the reward is a future-proof defence strategy in alignment with the realities of hybrid-cloud, remote working and changing cyber threats.
Start your Zero Trust journey today, assess your organization’s readiness and protect what matters most. This gives a professional finishing touch.
Related Link:
- What Is Network Security? Complete Guide
- Cloud Security: Protecting Data, Apps, and Infrastructure
- Multi-Cloud Security: Best Practices and Strategies
- Cyber-Security: Types, Threats & How to Stay Safe
FAQs
What is the fundamental aim of Zero Trust Security?
The fundamental objective is to eliminate the presumption of implicit trust within a network. Instead, each access request, whether from a device, application or user, is authenticated, authorized and relentlessly verified. This way, Zero Trust prevents an attacker from taking advantage of a trusted insider environment, lateral movement or unbridled access merely because they happen to be physically within a network perimeter.
Can an organization purchase Zero Trust as one product?
No, Zero Trust is not a one-product or checkbox solution. It is a strategic model and architecture integrating identity authentication, device posture control, access controls (least privilege), micro-segmentation, continuous monitoring and analytics. Organizations need to plan, deploy and iterate the model incrementally, tailoring it to their specific environment and risk profile.