Did you know that? Ransomware accounted for 44% of all confirmed breaches in Verizon’s 2025 Data Breach Investigations Report, a 37% year-over-year increase. Meanwhile, third-party involvement has doubled to 30%, showing why businesses will have to shore up network protection and plug growing supply-chain vulnerabilities in 2026.

As companies continue adopting multi-cloud infrastructures, distributed workforces, and AI-powered tools, the traditional network perimeter is disappearing. Business network security can no longer rely on defenses from another age; it requires an advanced cybersecurity strategy founded on identity-first security, continuous monitoring, and resilience by design. These revised approaches will enable enterprise businesses to secure their networks in a world where the threat landscape changes at an unprecedented pace.
Key Takeaways
- Network security in 2026 must center on zero trust, identity-first architecture, and real-time detection.
- Growing third-party and supply-chain risk requires the strengthening of vendor security controls.
- The growth of ransomware drives the need for strong segmentation, patching, and endpoint hygiene.
- Employee behavior remains a critical factor, and awareness and training are not negotiable.
- Incident response and governance frameworks should be implemented in order to reduce the potential impact of this breach.
- 9 Best Practices for Network Security in 2026
- Adopt Zero Trust as the Fundamental Security Model
- Elevate Identity & Access Management
- Leverage AI-powered Threat Detection and Monitoring
- Implement Network Segmentation and Micro‑Segmentation
- Secure All Endpoints Vigilantly
- Encryption and Classification of Sensitive Data
- Build a Robust Incident Response and Recovery Strategy
- Empower Governance, Risk & Compliance
- Robust Employee Training to Create a Strong Security Culture
- Final Thoughts
9 Best Practices for Network Security in 2026
In 2026, securing business networks requires a proactive, layered, and identity-centric approach as cyber threats grow more advanced. Organizations must combine modern security frameworks with AI-driven monitoring, strict access governance, and resilient architecture to defend against increasingly sophisticated attacks. These best practices form the foundation of strong network security and help businesses reduce risk, prevent breaches, and maintain operational continuity.
1. Adopt Zero Trust as the Fundamental Security Model
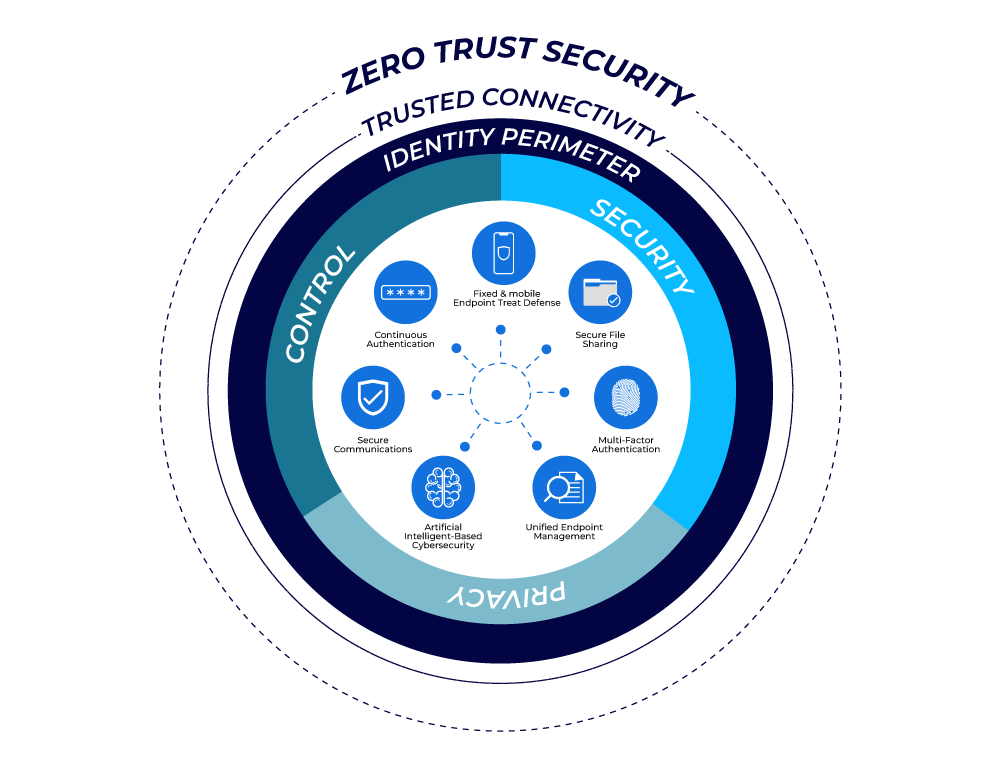
Zero trust will no longer be optional; it will be mandatory. This model transfers the reliance from static network perimeters to one where every user, device, and session is considered untrusted until verified. Zero trust translates to MFA enforcement, continuous device posture assessment, and least-privilege access. Validating each step of a workflow minimizes the potential for lateral movement, credential misuse, and internal compromise.
2. Elevate Identity & Access Management
Identity is the new perimeter of defense. The attackers continue to exploit weak or reused credentials; therefore, strong IAM controls are warranted in business. This would include not just MFA and SSO but tight management of privileged accounts, automated de-provisioning of users who are inactive, and reviews of access on a regular basis. Treating identity as the security perimeter reduces the probability of compromise significantly.
3. Leverage AI-powered Threat Detection and Monitoring
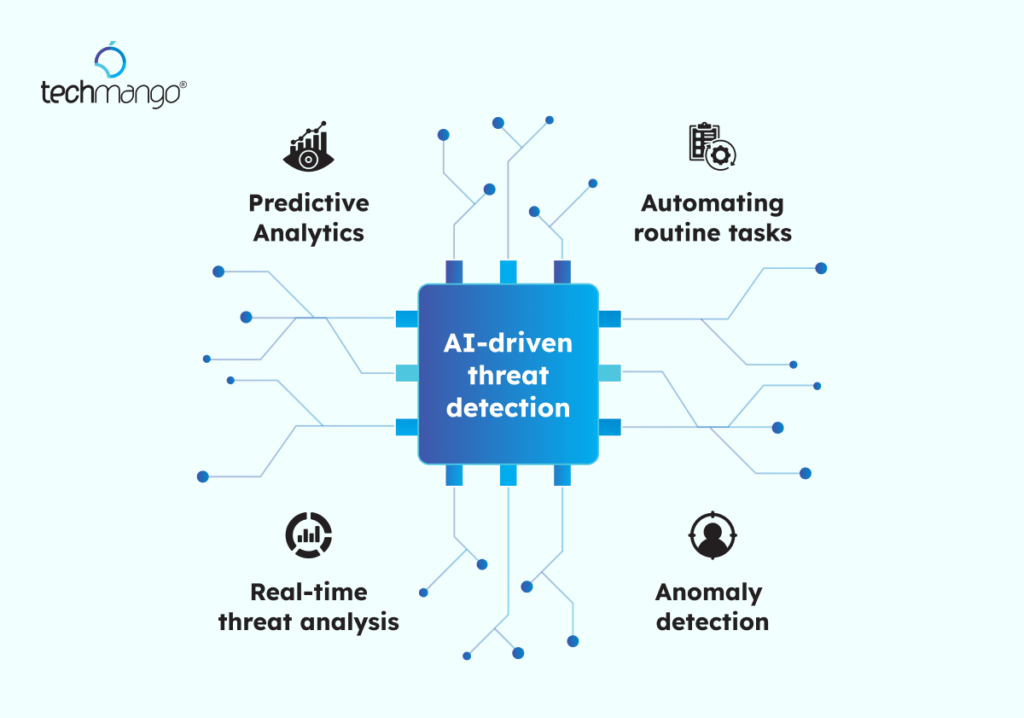
Automation, AI, and malware are used more in today’s world by cyber adversaries; its detection cannot be effective manually. Advanced tools, such as SIEM, XDR, and User and Entity Behavior Analytics, help security teams detect anomalies, track insider threats, and give event correlations from the cloud and on-prem environments. Security Intelligence by leading vendors shows that with AI-assisted detection, time to investigate and respond was reduced considerably, hence enhancing the overall security posture.
4. Implement Network Segmentation and Micro‑Segmentation
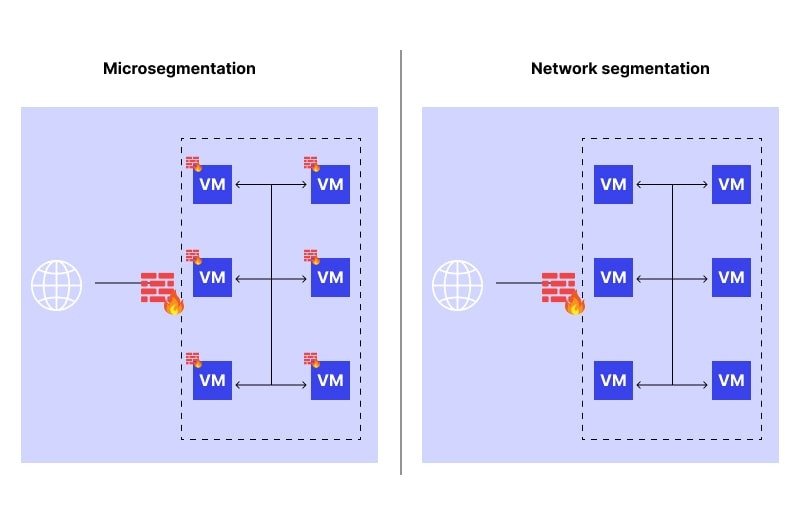
Segmentation of the network into zones can contain breaches. Micro-segmentation helps organizations segregate applications, workloads, and user groups in a way that, even if the attackers manage to break into one zone, they cannot laterally move around. This strategy has especially been helpful in containing ransomware and protecting high-value systems and data.
5. Secure All Endpoints Vigilantly
An endpoint has traditionally been highly vulnerable and continues to be so in today’s remote and hybrid workspace model. It can be made more secure through the use of EDR, periodic patching, permission for access only after device health checks are performed, and encryption of data stored on devices. This is why including Iot, BYOD, and legacy within your endpoint approach is so important, as attackers often look to those less monitored and/or unpatched endpoints as an avenue of attack.
6. Encryption and Classification of Sensitive Data
Data Security depends on encryption. It is highly recommended to encrypt all sensitive data both in transit with TLS and at rest with AES or stronger encryption, assure key management is done securely, and perform rotation regularly. Classification is necessary because it allows one to understand what data is critical so as to focus security activities and ensure that the most important information is always covered under the most stringent controls.
7. Build a Robust Incident Response and Recovery Strategy
No defense is perfect, and companies must be prepared for the worst. A mature IR plan should include defined roles, communication paths, and playbooks for the different attack scenarios like ransomware, insider threat, and third-party compromise. The plan has to be tested through tabletop exercises or simulations that validate its efficacy. In this way, companies will be able to minimize the probable time of their downtime, limit damage, and get into operation faster in case of a breach.
8. Empower Governance, Risk & Compliance
Security demands have similarly increased with the rise in regulatory demands around data protection, artificial intelligence, and third-party risk. For this reason, a security strategy should be a response to compliance obligations. Some frameworks that provide a structured approach to assess risk, define policy, and measure performance include but are not limited to ISO 27001, the NIST cybersecurity Framework, and CIS Controls. In 2026, GRC will also cover emerging areas like AI governance, shadow IT, and third-party vendor security.
9. Robust Employee Training to Create a Strong Security Culture
Even with all the best tools in place, human error remains one of the leading causes of breaches. Run continuous cybersecurity awareness programs; simulate phishing/social engineering attacks and provide role-based training for executives, developers, support, etc. Building a culture where employees understand risks and feel responsible for security will greatly help companies reduce the probability and impact of cyber incidents.
Final Thoughts
Network security in 2026 demands far more than the implementation of traditional perimeter-based solutions. It requires a strategic, multilayered, and intelligence-driven approach. As adversaries become more sophisticated, leveraging advanced tools, automation, and AI organizations must adopt zero trust architectures, enforce strong identity governance, deploy AI-powered threat detection, and maintain thoroughly tested incident response plans. By aligning security initiatives with business risks and fostering a culture of continuous vigilance, companies can reduce the impact of potential breaches while strengthening long-term trust and operational resilience.
Related Link:
- Network Security Architecture: How to Build a Secure Network
- Types of Network Security and How Each One Protects Your Data
- What is Network Security?
- What is Cloud Network Security?
To explore more insights like this, visit our Cybersecurity Page.
If you’re passionate about tech, networks, and digital infrastructure, Write for Us and share your voice with our audience.