In the dynamic world of cybercrime, Ransomware as a Service (RaaS) is one of the most concerning trends. Essentially, RaaS is a model for doing business in which malware authors produce and develop ransomware tools and infrastructure and then lease or resell these tools to other criminals (generally referred to as affiliates) in order to conduct attacks. Affiliates have no need for sophisticated technical expertise, they simply “plug in” and attack. In exchange, the attackers receive a share of ransomware payments or subscription fees.

The model has made ransomware a niche, highly technical threat and a scalable, semi-automated cybercrime ecosystem. Knowing RaaS how it operates, who the actors are, and how to protect against it is essential for organizations of any size.
- Why RaaS Matters Now More Than Ever
- How Ransomware as a Service Work
- Why RaaS Is Spreading So Rapidly
- Leading RaaS Variants & Groups
- The Cybersecurity Challenges Presented by RaaS
- Real-World Impact: Cases & Data
- Protecting Yourself: RaaS Defense Strategies
- 1. Create & Validate Incident Response Plans
- 2. Utilize Anomaly-Based Detection
- 3. Minimize Attack Surface
- 4. Implement Zero Trust / Access Controls
- 5. Preserve Immutable & Offline Backups
- 6. Employee Training & Awareness
- 7. Threat Hunting & Proactive Monitoring
- 8. Cooperate with Law Enforcement & Cyber Threat Intelligence
- 9. Cyber Insurance & Legal Preparedness
- Trends & Outlook for RaaS in 2025 and Beyond
- Conclusion
Why RaaS Matters Now More Than Ever
RaaS has transformed the threat landscape in several ways:
- Lower entry barrier for attackers: Now, non-technical criminals can launch ransomware attacks. (One of RaaS’s most primary threats is this democratization of cybercrime.)
- Higher volume and specialization: As of early 2024, active ransomware groups followed on dark-web forums increased by 56% from the previous year.
- Higher commercialization of crime: RaaS emulates legitimate SaaS or subscription-based software models, but with criminal purposes.
- Speed of evolution and resilience: Operators and affiliates are capable of reforming, rebranding, or converting to different ransomware variants when targeted by law enforcement or security companies.
- Increased extortion requests: In 2024, typical ransomware requests totaled more than USD 5.2 million in most cases.
- Increased attack volume: In 2024, there were approximately 5,414 reported ransomware attacks worldwide, an about 11% increase from 2023.
With these forces in place, it’s safe to say: RaaS is not a fleeting trend. It is a structural change in how ransomware businesses scale and last.
How Ransomware as a Service Work
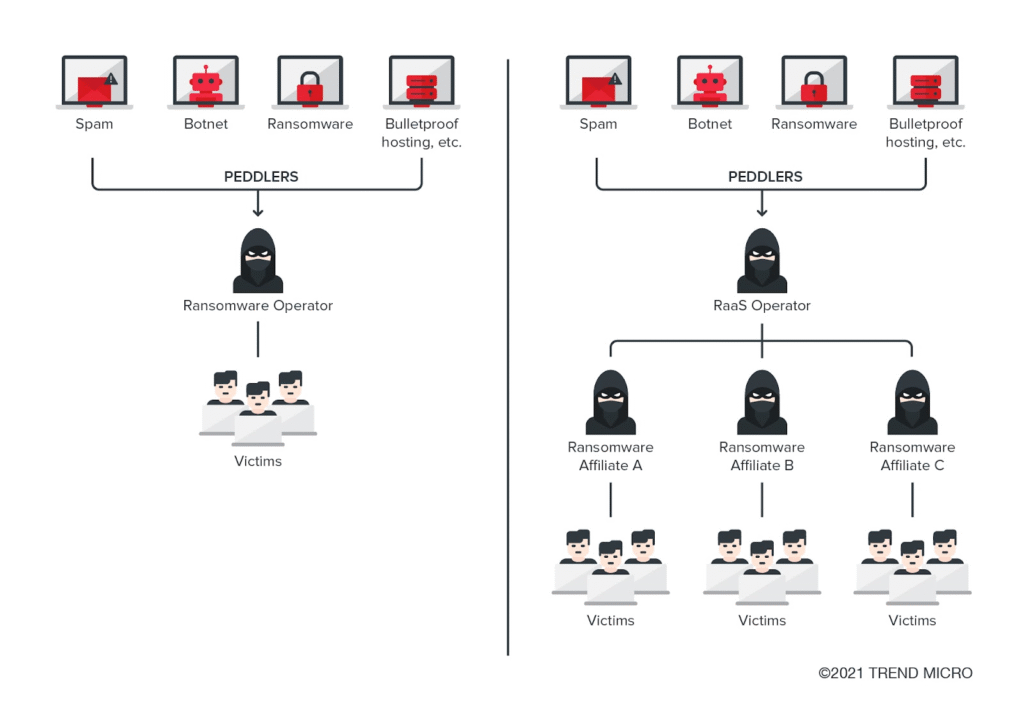
RaaS is similar to many aspects of legitimate software services, but within a criminal economy. This is how it typically works:
Roles and Structure
1. RaaS Operators / Developers
These are the ransomware authors and infrastructure operators. They create ransomware payloads, develop encryption/decryption functionality, operate payment sites, and host back-end infrastructure (e.g., command-and-control sites, leak sites).
2. Affiliates / Attackers
These are attackers or groups that rent or license the ransomware tools from operators. Affiliates normally perform the network breach, perform lateral movement, and drop the ransomware on infected environments.
3. Access Brokers / Initial Access Suppliers
More and more, there is a third tier: professional criminals who breach networks (e.g., through phishing, vulnerability exploitation) and sell access into corporate networks. Affiliates then buy those access credentials or footholds to launch the ransomware.
Monetization / Licensing Models
RaaS operators provide various monetization models. Popular models are:
- Subscription / Leasing: Affiliates give a recurring subscription (monthly or yearly) for use of ransomware tools.
- One-time license: Affiliates pay a one-time fee to exploit a given version of the ransomware.
- Affiliate / share-of-profits model: Operators receive a percentage (usually 20–40%) of any ransom recovered. There may be no initial cost.
- Hybrid models: Operators may employ hybrids (e.g. small initial payment + share of profits).
Affiliates only pay when attacks succeed, so operators do not risk loss and earn revenue from many campaigns, building scale and reach.
Value-Added Services
To lure and retain affiliates, advanced RaaS operations tend to offer “customer service” and assistance:
- Technical support and patches
- Secret forums / chatrooms for affiliates
- Payment processing sites (cryptocurrency-based)
- Tools for creating ransom notes and victim negotiation
- Leak sites for publishing stolen information if ransom is not paid
- Optional modules (data exfiltration, multi-extortion, lateral movement tools)
In fact, some RaaS groups act like illegal SaaS providers in the cybercrime underground.
Related Link: What is a Ransomware Attack? (2025 Guide)
Why RaaS Is Spreading So Rapidly
The success of RaaS is attributed to several reinforcing factors:
1. Lower technical barriers
Attackers do not have to develop or maintain their own ransomware code. They can lease or rent established tools.
2. Division of labor & specialization
Developers specialize in developing, affiliates specialize in selling, and access brokers specialize in providing access. Each does what they do best. Specialization accelerates work and optimizes returns.
3. Scalability and risk mitigation
If a single affiliate or campaign is interrupted, operators can simply proceed with others. The supply chain structure also decreases exposure.
4. Incentives and recruiting
RaaS operators openly recruit affiliates (occasionally providing “bait” deals) on dark web forums.
5. Rise in new groups and rebrands
New RaaS groups are forming in 2025, while some vanish or rebrand. Flashpoint, for instance, saw a 179% year-over-year growth in RaaS attacks mid-2025.
6. Increasing demand & extortion profits
As companies depend more on online infrastructure, pressure to pay ransom has only increased. Companies tend to pay to resume activities or prevent data leakages.
Leading RaaS Variants & Groups
Following are some of the most dangerous and infamous RaaS gangs, along with examples of their modus operandi and past:
LockBit
One of the most active RaaS groups. LockBit was behind a significant majority of worldwide ransomware attacks, at times valued at ~44%.
They have an advanced affiliate program, support modular plugin additions, and openly coerce victims through data leak sites.
BlackCat / ALPHV
BlackCat (also referred to as ALPHV) is a RaaS group that takes Rust-based content, has modular payload support, and utilizes stolen credentials and leak sites for coercion.
Akira
Akira is a RaaS group that attacks both Windows and Linux environments. It employs robust encryption and has been reported to exfiltrate data prior to encryption to facilitate double extortion.
Others & New Threats
- CL0P (particularly through the MOVEit exploit)
- Hive
- DarkSide / BlackMatter / REvil (old players, occasionally re-appearing)
- Eldorado (seen in 2024)
- Qilin, Play, SafePay, Lynx, noticed to be more active during 2025.
RaaS operators rebrand or shut down operations when pressured; they are hard to track.
The Cybersecurity Challenges Presented by RaaS
1. Blurred Attribution
Since affiliates and developers are separate entities, cybersecurity teams might find it challenging to attribute attacks. Affiliates will reuse available ransomware tools, and thus attribution becomes blurred.
2. Faster Attack Deployment
With pre-made toolkits, affiliates can launch attacks in days or even occasionally hours after establishing access.
3. Resilience & Reorganization
Even after law enforcement takes down one variant or operator, allies can shift to another kit or rebrand operations.
4. Advanced Pressure Tactics
RaaS attacks increasingly employ double extortion (encryption of data + threat to leak data), triple extortion (with DDoS or third-party threats added), and data exfiltration-only attacks (no encryption) to compel payment.
5. Attacking Harder to Defend Sectors
RaaS players understand the greatest leverage: health care, critical infrastructure, government agencies, and small/medium enterprises with poor security.
6. Rising Extortion Fees
Ransom request amounts have risen dramatically. During the first half of 2024, the typical request was over USD 5.2 million.
As reported by Arctic Wolf, during 2024 the typical ransom request was USD 600,000, with initial demands in most instances ranging from USD 300,000 to USD 5.5 million.
In Q2 2025, reported average ransom pay-out jumped to USD 1.13 million (over twice the previous quarter).
These figures illustrate that ransomware is no longer a minor annoyance, it is now a high-risk financial tool.
Related Link: CISA & FBI Issues Alert on Play Ransomware’s Growing Threat
Real-World Impact: Cases & Data
Global Attack Statistics
- 5,414 publicly reported ransomware cases were recorded in 2024, an 11% increase from 2023.
- Group-IB saw 5,066 attacks posted to data leak websites in 2024, up 10% year-on-year.
- Offices of the Director of National Intelligence worldwide saw ransomware attacks grow ~15% in 2024, though law enforcement activity moderated growth.
- SonicWall’s 2025 Cyber Threat Report saw an 8% rise in North American ransomware attacks during the year, attributing part of it to the simple entry that RaaS provides.
- Flashpoint noted a 179% year-over-year growth in RaaS-driven attacks in mid-2025.
Notable Incidents
- DarkSide ransomware was employed against the U.S. Colonial Pipeline in 2021.
- The REvil (also known as Sodinokibi) group attacked Kaseya, JBS, and others.
- LockBit is implicated in numerous critical infrastructure and enterprise attacks worldwide.
- In 2025, Albemarle County (Virginia, USA) was affected by a ransomware attack that forced internet services offline and released sensitive employee and public information.
These examples demonstrate that the attacks are not just against small businesses but are also targeting high-value targets where the pressure to pay is the highest.
Protecting Yourself: RaaS Defense Strategies
While RaaS makes the threat larger, many tried and true security methodologies still work. Following are defense layers to implement:
1. Create & Validate Incident Response Plans
As attribution can be uncertain and ransomware campaigns mature, your response plan should be adaptable and regularly tested. Have roles, communication procedures, and forensic capabilities established.
2. Utilize Anomaly-Based Detection
Deploy EDR (Endpoint Detection & Response), NDR (Network Detection & Response), and behavior-based solutions that identify deviations (e.g., mass file encryption, abnormal data transfer). Sophisticated ML/AI analytics can detect new ransomware patterns of behavior.
3. Minimize Attack Surface
- Implement timely patching and vulnerability management
- Disable or limit unused services
- Hardening remote access (VPN, RDP, SSH)
- Network segmentation to limit lateral spread
- Utilize firewalls, IPS/IDS, and web application protection
4. Implement Zero Trust / Access Controls
- Implement least privilege access
- Implement Multi-Factor Authentication (MFA) everywhere
- Segment critical systems so a breach in one area does not provide full access
5. Preserve Immutable & Offline Backups
- Store backups offline or in immutable storage (write-once)
- Regularly test recovery
- Use geographical or “air-gapped” backup strategies
6. Employee Training & Awareness
Human mistakes are still a main attack vector: phishing, social engineering, unsafe click-throughs. Ongoing training and phishing simulation diminish risk.
7. Threat Hunting & Proactive Monitoring
Don’t wait for alerts. Actively hunt for evidence of reconnaissance, lateral motion, privilege escalation, or backdoors.
8. Cooperate with Law Enforcement & Cyber Threat Intelligence
Early intervention with law enforcement can assist in tracking payments or recovering data. Sharing threat intelligence (TTPs, IoCs) among peers and agencies fortifies collective defense.
9. Cyber Insurance & Legal Preparedness
Have insurance coverage include ransom incidents (where permitted) and establish plans for legal, compliance, and communications effects.
Trends & Outlook for RaaS in 2025 and Beyond
1. Emergence of Double & Triple Extortion
Straightforward encryption extortion is evolving into multi-stage coercion: leak threats, DDoS, going after partners or shareholders.
2. Increasing RaaS Groups, Increasing Turnover
Operators will keep rebranding, splitting, or consolidating. New players such as Qilin, Play, SafePay, and Lynx are growing in popularity in 2025.
3. Data Exfiltration-first Playbooks
A few actors now avoid encryption altogether and are instead concerned with data stealing and ransom demands for not releasing it. During Q2 2025, 74% of extortion threats reportedly included data exfiltration as a central tactic.
4. AI/Automation in Attacks
Attackers could place more emphasis on AI when it comes to reconnaissance, vulnerability scanning, credential stuffing, and social engineering.
5. More Regulatory & Collaborative Action
Increased global cooperation, enforced breach reporting, stronger cybercrime legislation, and regulatory regimes (particularly in sensitive sectors) will strain RaaS viability.
6. Target Realignment
Small and medium-sized enterprises (SMBs), which have poor defenses, will continue to be prime targets. But as defenses evolve, hackers might turn towards supply-chain and third-party attacks for broader impact.
7. Saturation or Enfeeblement of Some RaaS Markets
Certain commentators propose the “well-oiled” RaaS machine will encounter problems: risk, saturation, and backlash will cull weaker operators.
Conclusion
Ransomware as a Service is not a trend, it’s a paradigm change in the way cyber extortion works. It reduces attack barriers, scales crime, and speeds financial and operational risk for organizations. The sophistication and speed of RaaS render it a powerful opponent.
Protecting against it requires a multi-faceted approach: strong detection, segmentation, solid backups, employee education, active threat hunting, and effective incident response. Additionally, organizations need to remain vigilant for emerging trends such as double extortion, new affiliate communities, AI-powered attacks and share threat intelligence and law enforcement actions.
If your organization has not yet evaluated its ransomware readiness, the time is now. The RaaS environment is changing and the price of not being prepared may be too high to pay.
To explore more insights like this, visit our Cyber-security Page.
If you’re passionate about tech, networks, and digital infrastructure, Write for Us and share your voice with our audience.