Over the past decade, ransomware has emerged as one of the most lethal cyber-attacks on people, businesses, and even nation-states. Of its numerous variants, crypto ransomware (or crypto-malware) is perhaps the most destructive. In contrast to other malware that hijacks or destroys information, crypto ransomware encrypts a victim’s information and demands payment of a ransom for its recovery, typically in cryptocurrency. Victims lose access to their data, and in the majority of cases, organizations are brought to a halt. This is what makes crypto ransomware so dangerous.

Cyber attackers no longer employ simple encryption techniques. They use extremely advanced methods, exploit human vulnerability via phishing, and exploit poor cybersecurity measures to initiate their attacks around the world. From hospital services that must be shut down to businesses losing millions of dollars, the devastation wrought by crypto ransomware has been catastrophic.
In this blog, we will dive into what crypto ransomware is, how it works, why it’s so successful, examples in the real world, and more importantly, how you and your company can be protected. When you know the tricks behind these kinds of attacks, you will be even better informed with which to build up strength and not become a victim.
What is Crypto Ransomware?
Crypto Ransomware Crypto ransomware is a type of malware that encrypts a victim’s files and demands payment, usually in cryptocurrency, for decryption, most often cryptocurrency, to decrypt. Their personal or business data is irrelevant to victims without the decrypt key in the possession of attackers.
Key features:
- Encrypts pictures, documents, backups, and databases.
- Presents a ransom notice that requests cash.
- Payment is most commonly made in cryptocurrency to be anonymous.
- Recovery is very impractical without the decrypt key of the attacker.
This is distinct from “locker ransomware,” which will encrypt the whole system. Crypto ransomware attacks file encryption in order to cause as much disruption as possible with the operating system running well enough to display ransom messages to the victim.
How Does Crypto Ransomware Work?
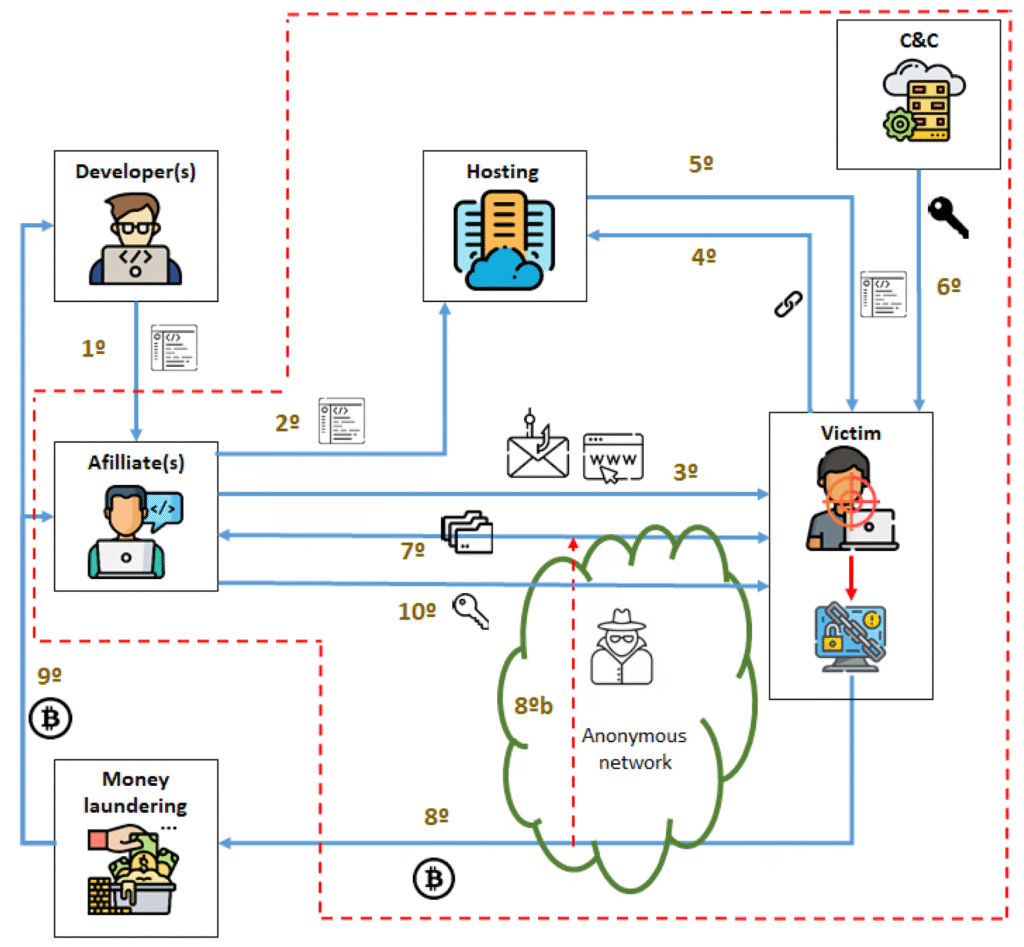
Crypto ransomware attacks are usually executed in a few steps:
1. Means of Infection
Attackers must access a system prior to encryption. The most common ways of infection are:
- Phishing Emails: Unsolicited attachments or links trick users into running malware.
- Malicious Websites & Drive-By Downloads: Bogus programs or concealed downloads infect unsuspecting users.
- Compromised Accounts: Hackers gain entry through weak or hijacked passwords (RDP, VPN, or email accounts).
- Exploiting Software Vulnerabilities: Unpatched or old software offers easy entry points.
2. Execution and Encryption Process
- The ransomware is highly contagious through folders and files once installed.
- Uses symmetric encryption (quick) to encrypt files.
- Encrypts encryption keys with asymmetric encryption (public-private key).
- Encrypts partially in certain versions to enable it to execute quickly while making data inaccessible.
3. Ransom Demand
- A ransom notice is displayed on the victim’s device.
- Instructions typically contain how much to pay, what cryptocurrency, and when the deadline is.
- Threateners typically threaten to erase files or leak sensitive information if the payment isn’t made.
Related Link: What Is Ransomware as a Service (RaaS)?
Examples of Major Crypto Ransomware Strains
Some ransomware groups rule the world of cybercrime. Among the most popular are:
- LockBit: One of the world’s most successful and profitable ransomware groups.
- Alphv/BlackCat: Renowned for attacking large companies with sophisticated attack techniques.
- Cl0p: Renowned for extensive data theft and extortion campaigns.
- Black Basta & Royal: Highly aggressive groups with significant ransom money demands.
- Medusa & NoEscape: New ransomware groups with emphasis on encryption and data leaks.
They work like organizations, and frequently they distribute ransomware as a service (RaaS) to partners.
Why Do Attackers Use Cryptocurrency for Payments
- Anonymity: Everything is pseudonymous and hence hard to track.
- Global Acceptance: Global acceptance without banking controls across international borders.
- Fast Transactions: It becomes even harder for law enforcement agencies to intervene.
- No Central Control: Cryptocurrencies are decentralized and not like traditional banking systems.
This makes cryptocurrency the ideal weapon for cybercriminals, although regulators and blockchain analysis companies are enhancing monitoring techniques.
Impact of Crypto Ransomware Attacks
Crypto ransomware causes more than technical issues; it can bring entire organizations to a standstill.
- Financial Losses: Payments can be in millions of dollars.
- Operational Disruption: Hospitals, airports, and factories have had to stop services.
- Damage to Reputation: Customers feel betrayed when businesses fail to secure their data.
- Legal Consequences: Businesses may be fined for not securing sensitive data.
How to Prevent Crypto Ransomware Attacks
Prevention is always (and less expensive) better than ransom payment. Best practices are:
- User Awareness & Training: Educate staff on how to identify phishing attacks.
- Regular Data Backups: Back up offline or in an encrypted cloud.
- Patch Management: Update operating systems and programs.
- Multi-Factor Authentication (MFA): Stops unauthorized access through stolen credentials.
- Endpoint Protection Solutions: Incorporate powerful anti-ransomware technology.
- Network Segmentation: Restrict ransomware propagation across the system.
- Incident Response Plan: Plan for quick response in case of an attack.
Related Link: What is a Ransomware Attack? (2025 Guide)
What To Do If You’re Infected
If you happen to get infected:
- Do Not Pay Immediately: Payment does not guarantee data recovery.
- Isolate Infected Systems: Keep spreading within the network.
- Report the Attack: Inform law enforcement and cyber security officials.
- Search for Decryptors: Occasionally, there are free available decryption utilities.
- Recover from Backups: Safest way to restore access without paying the ransom.
Final Thoughts
Crypto ransomware has developed into one of the most sinister 21st-century cyberthreats. Its power to encrypt confidential data, ask for payment in cryptocurrency, and distribute with lightning speed on networks makes it a terror for both individuals and entities. While older viruses may be uninstalled with little commotion, crypto ransomware offers victims few alternatives; pay the ransom (no promise of return), or lose forever access to their files.
But the tale does not conclude in terror. With the application of effective cybersecurity controls like frequent backups, multi-factor authentication, employee awareness education, and software patches, organizations and individuals can significantly minimize the likelihood of being successfully attacked. Governments, organizations, and security professionals are also collaborating across borders to combat ransomware gangs, disassemble them, and build stronger online defenses.
Lastly, the best defense is a good one. The more we know about crypto ransomware, the better off we will be. Uncertainty and lack of preparedness are what cybercrooks live for; knowledge, awareness, and security ahead of time are our best countermeasures.
If your organization has not yet evaluated its ransomware readiness, the time is now. The RaaS environment is changing and the price of not being prepared may be too high to pay.
To explore more insights like this, visit our Cyber-security Page.
If you’re passionate about tech, networks, and digital infrastructure, Write for Us and share your voice with our audience.
FAQs
Should victims pay the ransom?
No, paying funds for cybercrime doesn’t guarantee recovery. Backups and law enforcement are safer solutions.
Can personal devices be infected?
Yes, although business is primarily targeted, individuals’ devices are also vulnerable through phishing and bad downloads.