Cyberattack is growing faster than ever driven by cloud adoption, remote work, IoT devices, and shadow IT. Every new application, device, or third-party service adds another entry point for hackers. This collection of potential entry points is called your attack surface, and the larger it gets, the harder it is to protect.

Traditional security tools cannot handle the always evolving digital environment. This is where Attack Surface Management (ASM) comes in. ASM lets companies see all of their known, unknown, or forgotten assets in real time and helps them to be proactive in resolving vulnerabilities before attackers take advantage of them.
This guide will help you understand what ASM is, why it’s so important, how it operates, and how it helps lower cybersecurity risks in modern, dynamic IT systems.
- What is Attack Surface?
- What is Attack Surface Management?
- Why Organizations Are Turning to Attack Surface Management
- How Attack Surface Management Works
- Core Components of Attack Surface Management
- Best Practices for Effective ASM
- Future of Attack Surface Management
- Final Thoughts: Stay Ahead of Cyber Threats with ASM
- FAQs
What is Attack Surface?
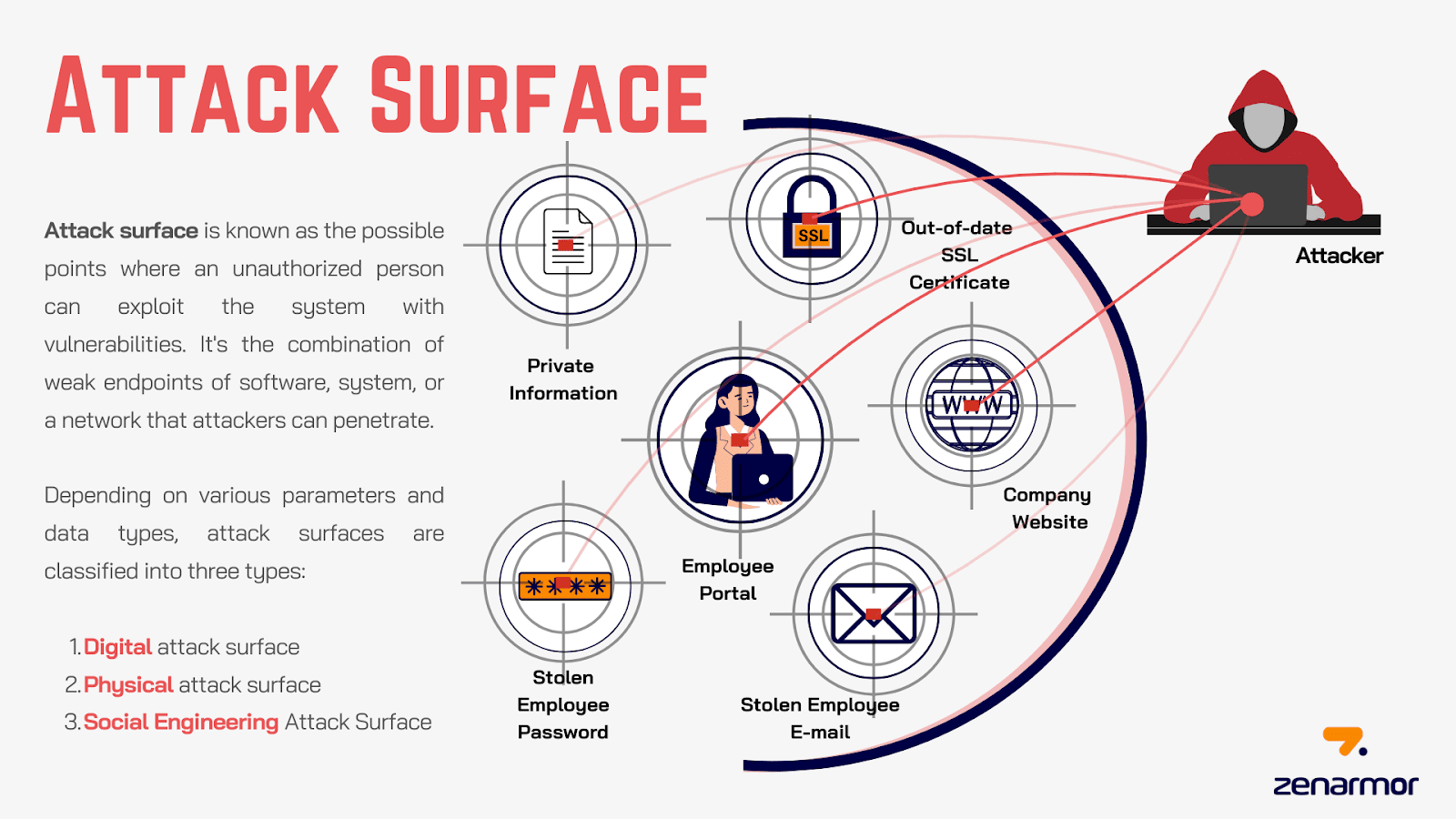
The attack surface is the total number of points where an unauthorized user can try to access or extract information from your system. It includes:
- Web applications, APIs, cloud services, IoT devices, and other digital assets.
- Human elements, including staff members susceptible to phishing attacks.
- Physical access points include offices or unsecured hardware.
Hackers have more possibilities to use the bigger and more intricate your attack surface.
For instance, many times when businesses quickly embrace cloud services or permit remote work, they generate shadow IT, undetected or unregulated assets that security teams cannot oversee, opening doors for cybercriminals.
That’s why organizations need Attack Surface Management (ASM) to constantly find, track, and protect all of these possible hazards.
What is Attack Surface Management?
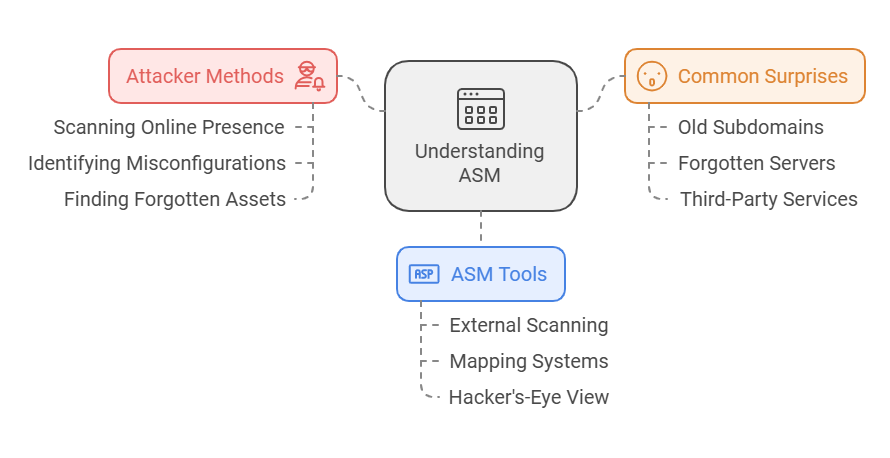
Attack Surface Management (ASM) is the continuous process of discovering, analyzing, prioritizing, and monitoring all the digital, physical, and human entry points that could be exploited by cybercriminals.
ASM adopts a hacker’s view, finding and evaluating all potential flaws as an attacker would, unlike conventional security techniques targeting just known assets.
ASM covers:
- Known assets: servers, applications, cloud services.
- Unmanaged devices or unknown or shadow IT including unauthorised SaaS products.
- Third party or vendor assets linked with your network.
- Assets of acquired or subsidiary firm.
- Rogue or malicious assets include fraudulent phishing sites simulating your brand.
ASM enables businesses to remain one step ahead of cyberattacks even as their IT infrastructure changes by allowing them to think like an attacker.
Why Organizations Are Turning to Attack Surface Management
Modern companies are quickly embracing cloud services, remote work, IoT devices, and third-party integrations. Therefore increasing their digital footprint, complexity, and security difficulty. Conventional security techniques fall behind this moving attack surface.
Here’s the reason companies today use ASM:
- Cloud and Remote Work Increase: Remote access and the move to cloud systems bring new, ever-changing assets that need monitoring.
- Danger from Shadow IT: Many employees utilize unauthorized apps or services, therefore generating invisible weaknesses outside of the purview of the IT team.
- Third-Party Relationships: APIs, SaaS platforms, and vendors broaden exposure to outside hazards.
- Faster Emerging Threats: New attack vectors are always found by hackers; ASM aids security teams in spotting them beforehand.
- Restrictions of traditional security: Static vulnerability scans or penetration testing only evaluate recognized systems. They miss new, unexplored, or neglected assets that hackers first assault.
ASM helps companies to keep ahead of cyberattacks by constantly finding and watching threats, much like an always ethical hacker.
Recommended Read: What is SOC as a Service (SOCaaS)?
How Attack Surface Management Works
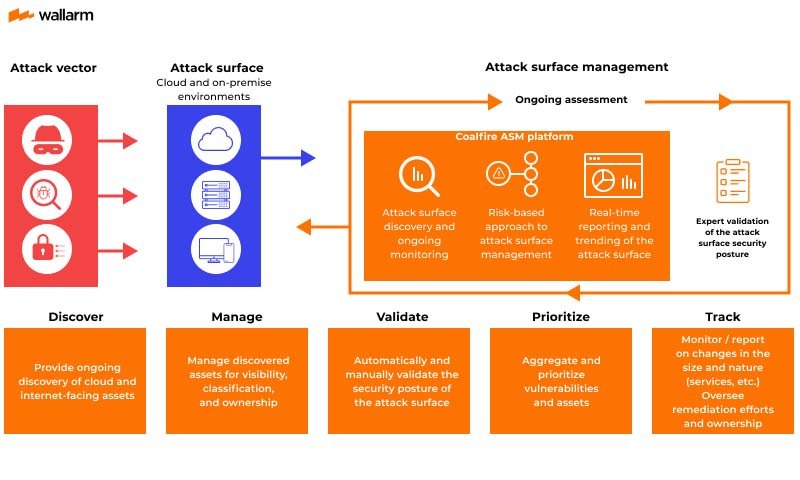
Attack Surface Management (ASM) follows a continuous cycle to discover, analyze, and secure all potential entry points attackers might exploit. Unlike one-time scans, it runs non-stop to keep up with constantly changing IT environments.
How Management of Attack Surface Operates.
Here’s how it works:
1. Assets’ Discovery
- Regularly seeks for all internet-facing assets known, unknown, or forgotten.
- Identifies orphaned systems, shadow IT, and even dangerous assets built by attackers like fraudulent phishing sites.
- Comprises third-party and secondary assets connected to your network.
2. Classification and Risk Assessment
- Sort group assets by ownership, kind, and relationship to the network.
- Finds weaknesses including broken settings, obsolete software, or poor security.
- Uses threat intelligence to evaluate how appealing hackers find every asset.
3. Prioritization
- Organizing vulnerabilities according to their business impact and exploitability.
- First, prioritize the most vulnerable and high-risk assets in your remediation efforts.
4. Remediation
- Strengthens access controls, retires unwanted assets, repairs misconfigurations, and implements security patches.
- Covers unmanaged or third-party assets within security guidelines.
5. Continuous Monitoring
- Constantly looking in real time for fresh assets, flaws, and risks.
- Works with XDR, SIEM, and EDR tools to improve detection and response.
As your attack surface expands and alters, ASM serves like a real-time security radar and adjusts continually.
Core Components of Attack Surface Management
An organization’s attack surface isn’t just about exposed servers or apps. it includes everything that could be exploited by attackers. ASM looks at four major components:
1. External Attack Surface
- Internet-facing assets include exposed servers, APIs, cloud services, SaaS applications, and websites.
- Because they are freely available, hackers find these to be the simplest targets.
2. Internal Attack Surface
- Includes assets inside your corporate network such on prem servers, employee devices, and internal applications.
- Compromised credentials, internal attacks, or lateral movement following an external breach provide much of the threats.
3. Attack Surface Social Engineering
- Human-related vulnerabilities such as phishing, insufficient employee training, or social media exposure.
- Psychological control enables attackers to circumvent technical security mechanisms.
4. Physical Attack Surface
- Hardware, IoT devices, and physical access points like badly secured business premises or open USB ports.
- Physical breaches or insider threats can result in lost devices or stolen data.
To give a full picture of where threats lie, something conventional security systems cannot fully achieve ASM constantly maps and observes all these layers.
Best Practices for Effective ASM
- Automate asset discovery & monitoring: Continuously scan your entire digital footprint (on-premises, cloud, IoT) to identify new and forgotten assets in real time.
- Integrate ASM with SIEM, EDR, and XDR: Connect ASM with Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR) to improve threat visibility and faster incident response.
- Cover third-party and subsidiary assets: Don’t ignore vendor systems, SaaS applications, shadow IT, or subsidiary networks, as they often introduce hidden vulnerabilities.
- Combine ASM with a Zero Trust approach: Never assume internal traffic is safe, verify every access request and minimize permissions to reduce risk.
- Prioritize vulnerabilities based on real risk: Focus on the most “attackable” assets by using threat intelligence and hacker-like analysis for better remediation.
- Regularly validate with ethical hacking or red teaming: Simulate real-world attacks to see if ASM is identifying and mitigating the right threats.
Ensure proper remediation workflows; Automate patching, secure orphaned IT, and enforce consistent security policies across all assets.
Future of Attack Surface Management
- AI & machine learning predictive security ASM will mature with AI models that anticipate and block threats before they’re attacked.
- Increased emphasis on IoT & 5G threats With trillions of IoT devices and blazingly fast 5G networks, ASM will emphasize these challenging and dynamic landscapes.
- More involvement with threat intelligence Future ASM will integrate with real-time threat feeds, dark web monitoring, and vulnerability databases to prioritize risks more quickly.
- Cloud-native ASM features ASM solutions will automatically scale in hybrid and multi-cloud environments for improved adaptability.
- Improved automation & self-healing capabilities Automated remediation and self-healing settings will decrease human mistakes and response time.
Read More: What is Prisma Cloud? (Complete Guide)
Final Thoughts: Stay Ahead of Cyber Threats with ASM
Your attack surface grows with every new cloud service, IoT device, or third party integration in today’s rapid digital world. Dependence on reactive, conventional security systems is no more adequate. Attack Surface Management (ASM) offers companies a hacker’s eye perspective of their whole digital footprint so guaranteeing no secret asset or flaw goes unnoticed.
ASM assists you develop a proactive security attitude that stops threats before they may cause damage by constantly identifying, evaluating, and prioritizing hazards. ASM becomes an essential layer of contemporary cybersecurity when used together with Zero Trust ideas, automated monitoring, and integration with other security technologies.
Early organizational adoption of ASM enables better protection of sensitive data, upkeep of trust, and stay ahead of changing cyberattacks.
For more expert insights, explore our cyber-security page; we have the best guides and tips for you. If you’re interested in contributing, submit your guest post and Write for Us.
FAQs
Why is ASM important for modern organizations?
With cloud adoption, remote work, IoT devices, and third-party services expanding the digital footprint, ASM helps identify hidden assets and vulnerabilities before hackers can target them.
What are examples of an attack surface?
It includes web apps, APIs, cloud services, IoT devices, employee devices, third-party SaaS platforms, physical access points, and even human factors like phishing risks.