All discussions around cyber-security really center on hackers outside the organization, but quite likely the greatest danger to organizations now is from within. Insider threats are those with already existing legitimate access to sensitive data, networks, or systems. These events may be deliberate (malicious) or non-deliberate (accidental), but they can be highly destructive.

Insider threats, according to the Ponemon Institute, have cost billions of dollars every year around the world. They are especially dangerous because they have already traversed the perimeter boundary defenses, such as firewalls or passwords, as they are familiar users.
Insider threats are possible to experience in any organization ranging from small startups to government agencies. It is for this reason that learning what they are, how they occur, and how to mitigate them is essential to contemporary cybersecurity.
What is an Insider Threat?
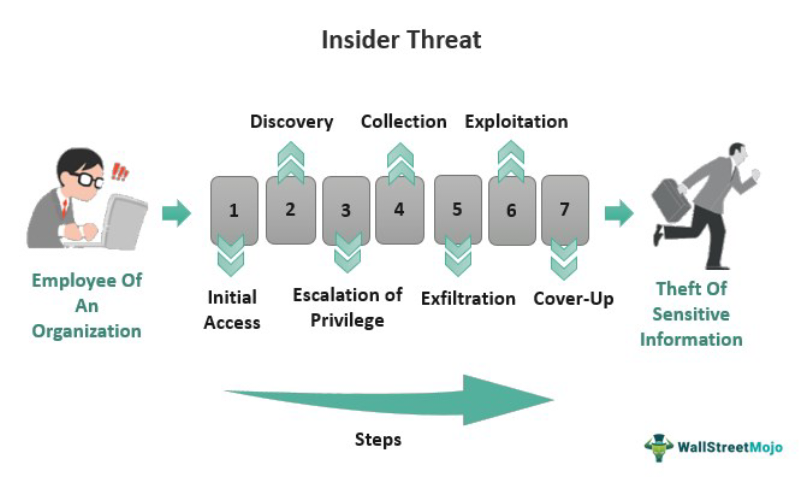
An insider threat is any possible danger by those who have permitted access to an organization’s assets and abuse it to the possible detriment of the organization. They may be current or former employees, contractors, vendors, or business partners.
Examples of insider threat actions included:
- Theft or disclosure of confidential data.
- Hacking or altering security settings.
- Spying or disclosure of company information to others.
- Unintentional disclosure of confidential data due to negligence.
As Cybersecurity and Infrastructure Security Agency describes, the insider threats can be unintentional. A simple error, such as a click on a phishing email or the generation of poor passwords, can result in catastrophic breaches.
This intersection of trust and access is part of the reason why insider threats are less apparent than outside attacks.
Related Link: Cyber-Security in 2025: Types, Threats & How to Stay Safe
Types of Insider Threats
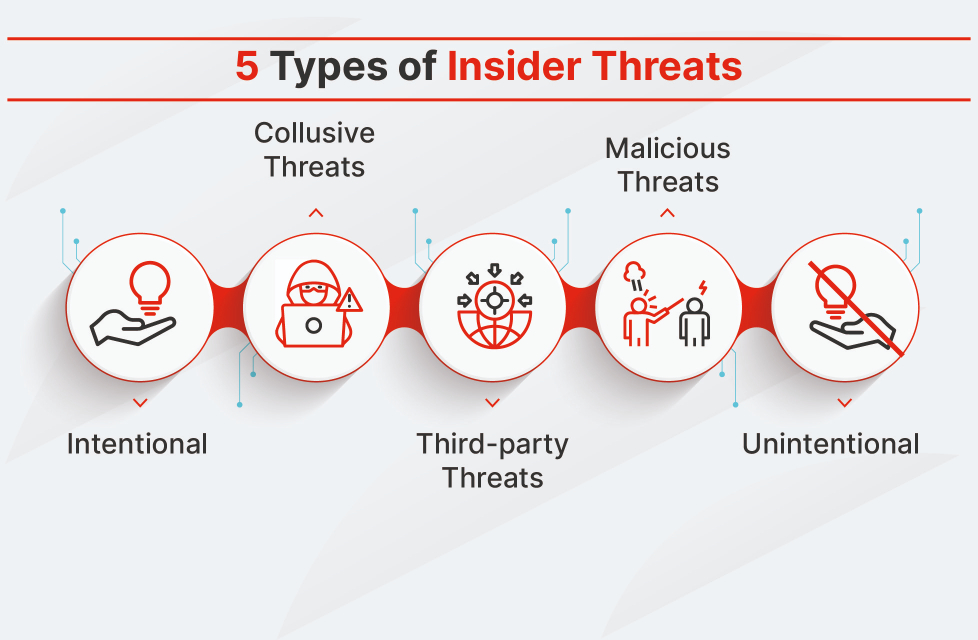
Various kinds of insider threats carry varied risks. These kinds are what organizations utilize to develop effective defense measures.
a. Intentional Insider Threats
- These are individuals who cause harm intentionally.
- Driven by revenge, profit, or ideology.
- Can steal information, spread malware, create system disruption, or sell corporation secrets to a competitor.
- Usually involve dissatisfied employees or profit-motivated individuals.
b. Unintentional Insider Threats
These are mistakes that are caused by negligence or insensitivity to security.
- Opening a phishing link, or opening attachments that are malicious.
- Logging in with poor passwords, or sharing accounts.
- Sending confidential documents to the wrong recipients.
- Loss of devices containing confidential data.
The majority of insider incidents belong to this category.
c. Third-Party Insider Threats
Third-party partners, contractors, or vendors can be given access to internal networks.
- Lack of proper security on their side can be taken advantage of by cybercriminals.
- Attackers will attack the smaller partners to infiltrate larger networks.
- It is a new supply chain cybersecurity threat.
d. Malicious Insider Threats
Insiders deliberately damage the company.
- Examples are deleting critical files, revealing trade secrets, or seeding ransomware.
- These kinds of attacks will mostly consist of upset employees or those enticed by money.
e. Collusive Insider Threats
When an insider partners with an outside attacker:
- An insider may leak credentials or create a backdoor onto the network.
- These incidents are risky because they consist of insider access and outsider attack methods.
Common Insider Threat Profiles
The Federal Bureau of Investigation and the National Institute of Standards and Technology outline typical behavioral patterns observed during insider incidents. They assist with early detection in the following ways:
- Pawns: Workers who are phished or scammed to unknowingly assist hackers.
- Turncloaks: Workers who intentionally cause harm to the company for revenge or personal benefit.
- Collaborators: Insiders who actively collaborate with outsiders to steal or expose information.
- Goofs: Careless workers who do not follow security procedures, leaving systems open to attack.
- Lone Wolves: Experienced insiders who work alone to exploit vulnerabilities or steal information.
They are not profiles of employee judgments but are profiles of behavioral tendencies likely to lead to an incident.
Early Warning Signs of Insider Threat
Insider threats always display warning signs before inflicting major harm. Detection early on avoids expensive breaches.
Common indicators include:
- Unusual login attempts during off hours.
- Oversized data transfer or downloads without apparent purpose.
- Use of remote access tools or applications without authorization.
- Repeated failed login attempts followed by successful login.
- Disabling or circumventing security controls.
- Accessibility to job-nonspecific information.
- Efforts to duplicate or move sensitive files into personal accounts or exterior drives.
Security staff can utilize behavior analysis and real-time monitoring to capture these indicators early on.
Real-World Examples of Insider Threat
Insider threats have brought about widespread real-life damage:
Former Employee Deletes Critical Data
A former U.S. credit union employee still had access for 40 minutes after her employment was terminated. Within the brief period, she downloaded 21GB of sensitive data, including primary security documents. The organization incurred enormous financial and operational expenses.
Accidental Exposure Leads in Breach
One of the employees in a tech firm kept millions of driver files in a vulnerable place. The unintentional action led to a huge data breach and legal repercussions, even though there was no malevolence involved.
Vendor Weakness Exploited:
Hackers broke into a contractor’s system, which gave the intruders access to the parent company’s network. This reveals how third-party insider threats are equally damaging as insider threats.
These events illustrate why processes, people, and partners need to be the target of insider threat management.
Related Link: What Is a Denial of Service Attack? Complete Guide
Risks Caused by Insider Threats
The impact of insider threats extends well past temporary disruptions.
Major risks include:
- Theft and Espionage of Data: Confidential business or client data can be pilfered or peddled.
- Financial Loss: Recovery, attorney fees, compensation, and fines can be extremely costly.
- Reputation Harm: Customers’ and clients’ trust can be forever lost.
- Operational Downtime: Key systems can be taken offline, halting services.
- Legal and Compliance Issues: Failure to meet data protection standards will result in lawsuits and fines.
The Ponemon Institute reports indicate that the average cost of an insider threat incident is over $11 million, money that keeps accumulating each year.
How to Detect and Stop Insider Threats
No company can eradicate insider threats completely, but they can be detected and halted early through a systematic approach.
a. Detect
- Install continuous monitoring tools to detect suspicious activity.
- Utilize behavior analytics to notify abnormal behavior such as large downloads or new location logins.
- Implement automated notifications to shorten response time.
b. Investigate
- When suspicious behavior is detected, investigate in real-time.
- Maintain detailed security logs to know what happened and who was involved.
- Engage security teams early to reduce damage.
c. Prevent
- Employ the principle of least privilege to restrict access to sensitive information.
- Employ multi-factor authentication (MFA) to protect accounts.
- Terminate access immediately when an employee departs.
- Track third-party vendors and record their access.
- Update systems regularly and close holes.
d. Protect
- Establish robust security policies and ensure employees are aware of them.
- Implement regular training to inform employees of phishing, scams, and data protection.
- Incorporate reporting of suspicious activity without fear of retribution.
- Implement encryption, backups, and endpoint protection.
Culture and technology equal prevention. A trustworthy organization is founded on trust but underpinned by intelligent security controls.
Best Practices to Reduce Insider Threat Risks
Defending well is all about realistic day-to-day practice. Best practice agencies such as Cybersecurity and Infrastructure Security Agency suggest:
- Conduct regular security training: Educate employees in phishing detection, sensitive information handling, and reporting threats.
- Implement Zero Trust security: Never trust any account completely, even internal ones.
- Limit privileged access: Provide access only to what is absolutely essential.
- Monitor high-risk accounts: Admin and privileged accounts need to be placed under additional security.
- Establish strong offboarding procedures: Remove access when staff leave immediately.
- Secure third-party vendors: Make contractors adhere to your organization’s security protocols.
- Use data loss prevention (DLP) tools: Prevent and catch unauthorized file transfers.
- Regular audit: Inspect access logs, system settings, and user permissions.
By adopting these best practices, organizations can minimize insider threat risk effectively.
Conclusion
Insider threats are likely the most perilous and underappreciated cyber threat of today. Insiders enjoy the privilege of already being within an organization and basking in trust and access, so their moves are more difficult to catch and possibly more devastating.
Insider threats, as it turns out, are not invincible. With the right mix of security technologies, astute policies, employee monitoring, and robust access controls, organizations can effectively reduce their threat.
As the Cybersecurity and Infrastructure Security Agency perennially reminds us: “Security starts with people.” By creating a culture of responsibility and awareness, firms can shield themselves not just from the outside but also from the inside.
To explore more insights like this, visit our Cyber-security Page.
If you’re passionate about tech, networks, and digital infrastructure, Write for Us and share your voice with our audience.
FAQs
What is an insider threat in cybersecurity?
An insider threat is a security risk that originates from people who are approved to have access to an organization’s data or systems. Insider threats can be either deliberate or inadvertent, and both of them can cause tremendous harm.
How can insider threats be prevented?
Prevention involves the implementation of Zero Trust principles, access control, continuous monitoring, robust security awareness training, and rigorous offboarding protocols for employees and vendors.
What are common signs of insider threats?
Warning indicators include unusual access patterns, heavy and fast file transfers, unauthorized program downloads, logins at odd times, and accidental security setting modifications.