In the current digital age, cyber threats are no longer theoretical threats far from it, they are real, immediate threats to all users and businesses. Among them, ransomware is probably one of the most disastrous and troublesome. Ransomware attack is a criminal offense in which cybercriminals encrypt, steal, or lock precious information and seek a ransom payment, most commonly in cryptocurrency, in order to regain access or avoid its public disclosure.

The magnitude of this issue only grows. Cybersecurity studies indicate that worldwide ransomware expenses will be $57 billion in 2025. Simultaneously, the average per-data-breach cost was $4.88 million in 2024. Such giant numbers estimate the horrific financial and reputational damages ransomware can cause.
But ransomware is more than statistics. It brings entire hospitals to a standstill where patients depend on unfettered access to records, schools where student information hangs in the balance, and businesses whose operations are brought to a frozen halt. Learning how they work, how they’ve grown in new disguises, and how they can be held in check is now a part of being digitally literate today.
- What is a Ransomware Attack?
- How Does a Ransomware Attack Work
- Types of Ransomware Attacks
- Major Ransomware Variants and Groups
- Real-World Examples of Ransomware Incidents
- Impact of Ransomware on Businesses
- Industries Most Impacted by Ransomware
- How to Protect Against Ransomware
- What to Do if You Are Hit by Ransomware
- Future Outlook of Ransomware
- Final Thoughts
- FAQs
What is a Ransomware Attack?
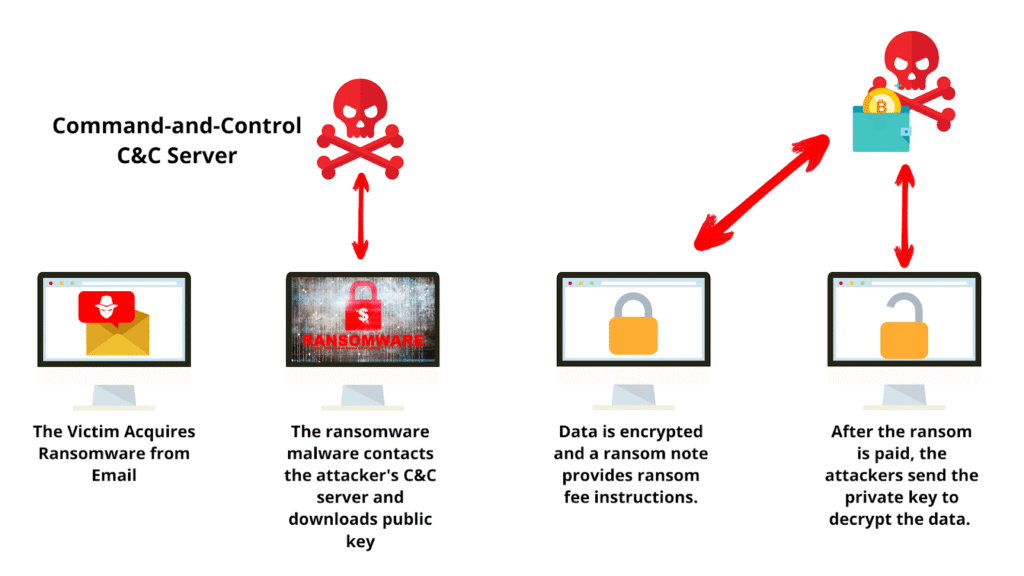
At its core, ransomware is a form of malware that denies system or data access for money in exchange for a ransom. In the past, it was done through encryption, where files were encrypted using powerful cryptographic software. Over time, attackers found encryption insufficient and so they added data exfiltration and extortion. Nowadays, the majority of ransomware attacks involve combining encryption with threatening the publicizing of sensitive information on the internet in case the victim does not pay.
This development from plain “lock and pay” to elaborate double or triple extortion rackets indicates how much, far and away, cybercriminals have progressed. So much so that some gangs do not even encrypt files anymore; they simply steal sensitive information and blackmail victims into sharing it.
How Does a Ransomware Attack Work
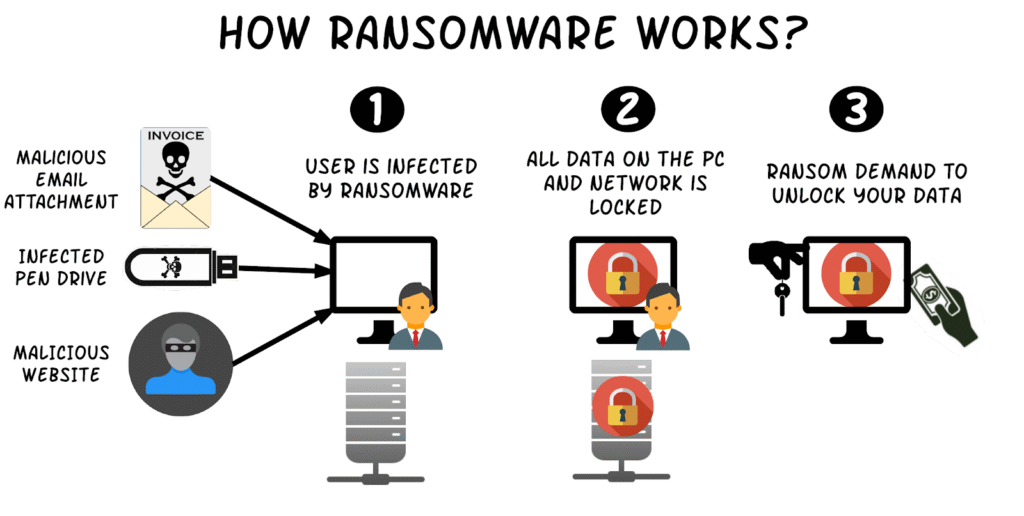
While every ransomware attack is different, all but a few follow essentially the same process. It usually starts with an in through an entry point, typically by way of phishing, unpatched exploits, or poor remote access credentials. In, attackers move stealthily laterally through systems, privilege-escalating and turning off security tools.
The following step is delivering the payload of the ransomware. The files are encrypted, backups are erased, and data occasionally gets exfiltrated to remote servers. Once harm is done, the victim receives a ransom notice, often with instructions on how to pay in cryptocurrency.
Observe that ransom payment does not automatically lead to recovery. Some of the attackers may not give an operational decryption key, and other attackers may continue holding onto or selling the stolen information even after money has been paid. This doubt is one of the greatest challenges on what to do in the event of a ransomware attack.
Types of Ransomware Attacks
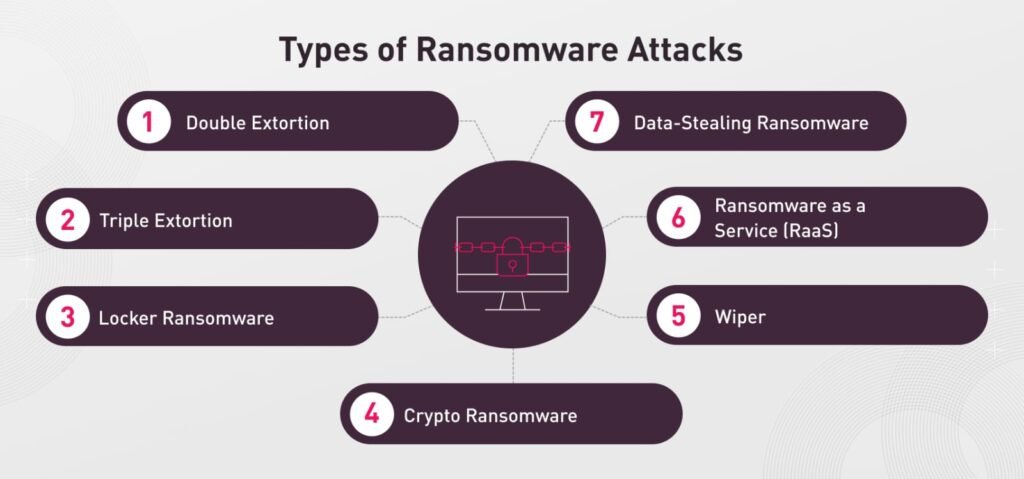
Throughout the years, there are various kinds of ransomware. Some attack individuals, while others attack massive corporations or governments. Some common ones include:
- Crypto Ransomware: Encrypts information and asks for payment in exchange for decryption keys.
- Locker Ransomware: Locks down the whole system, preventing devices from being used but not necessarily encrypting information.
- Double Extortion: Steals data and encrypts files and blackmails to put it online.
- Triple or Multi-Extortion: Applies extra pressure, including initiating Distributed Denial of Service (DDoS) attacks or extorting the victim’s partners and customers directly.
- Ransomware-as-a-Service (RaaS): Business model where ransomware creators sell, rent out their tools to affiliates in exchange for a percentage of proceeds.
- Wipers: Malware masquerading as ransomware with the hidden agenda of erasing data and failing to recover it.
That diversity of strategy complicates ransomware to defend against. Organisations must be ready for both crypto-based and strictly extortion-based models.
Major Ransomware Variants and Groups
Ransomware is not a program but an ecosystem of numerous disparate groups, all with their own variant and infrastructure. In 2025, some old names dominate the landscape:
- Qilin picked up steam following the abrupt vanishing of RansomHub in April 2025. All its players had switched to Qilin, doubling its victims in the subsequent quarter.
- Akira, first noticed in 2023, gained popularity due to the fact that it could infect both Windows and Linux systems and is a favorite among worldwide criminal players.
- LockBit is still one of the busiest and most nefarious ransomware crews. They stay in business through speed and very advanced leak site naming and shaming victims publicly.
- Ryuk, while old-fashioned, still persists in having a role in contemporary ransomware operations by targeting large corporations and asking astronomically huge ransoms.
These attacks involve professionalization of ransomware operations. They operate as genuine businesses with victim support in the technical sense, marketing campaigns, and rigorous affiliate protocols.
Real-World Examples of Ransomware Incidents
The actual effect of ransomware becomes apparent when looking at more recent instances. RansomHub abruptly closed in April 2025, with most of its affiliates consolidating with other groups like Qilin. This exodus showed just how resilient and long-lasting the market for ransomware is, even when one group disbanded.
Later in the same year, medical giant DaVita became a victim of a ransomware attack by a group that called itself InterLock. It attacked millions of patient records, raising critical questions over patient safety and patient trust in medical networks.
In hindsight, the notorious 2017 WannaCry attack is among the most prevalent attacks. It was a Windows vulnerability attack that propagated quickly to infect hundreds of thousands of computers globally, including transport networks and medical centers. Although older, the incident is commonly referred to as a period during which global awareness of ransomware shifted.
Impact of Ransomware on Businesses
The cost of ransomware is catastrophic. In addition to the ransom payment, businesses also incur time in downtime, data recovery, fines from regulators, and long-lasting reputational damage. IBM’s 2025 study had estimated the mean cost of a data breach at almost $4.9 million, and many ransomware incidents are above this due to the high level of disruption.
Down time is another monumental impact. Industry research shows 58% of the companies who were attacked by ransomware had to shut down operations for an average of 12 hours. To hospitals, utilities, and other vital services, even a few hours of down time can be fatal.
The harm to one’s reputation cannot be overstated either. Clients, customers, and business partners lose confidence if sensitive information are exposed, and their trust is eroded in the long term. In regulated sectors such as healthcare and finance, firms can also receive huge fines for not protecting personal data.
Industries Most Impacted by Ransomware
No industry is exempt, but others are attacked more frequently because their information is sensitive and they require constant uptime. Health systems, for example, are highly susceptible because delays to patients will force prompt payment of ransom. Universities are also under threat because they have laxer cybersecurity budgets and hold useful personal data.
Government agencies and public institutions are similarly a prime target, in the majority of instances with ancient infrastructure having no contemporary defenses. Industries such as energy grids, water supplies, and transportation networks are also top targets due to the devastation caused by disruptions.
How to Protect Against Ransomware
Ransomware mitigation needs to be a multi-layered process. A single policy or tool might eradicate the risk, but sets of preventatives and responses all minimize attack success considerably.
Staff must be trained to be the first action in organizations, since phishing remains one of the most prevalent attack vectors. Routine awareness workshops and mock phishing train employees to pay attention to potential threats prior to clicking.
Regular backups are another pillar of defense. The backups must be secured, ideally kept offline or in immutable formats that are hard for ransomware to modify. Firms with clean backups are usually able to recover quickly without paying the attackers.
Software patches and updates are also important since most of the ransomware attacks rely on known vulnerabilities. With good access controls, network segmentation, and multi-factor authentication, these controls restrict the ability of ransomware to propagate once it has entered a system.
Finally, the companies must invest in detection and response technologies. Endpoint detection, real-time monitoring, and incident response planning help ensure that even when the attackers get through, their work can be detected and isolated before the harm becomes permanent.
What to Do if You Are Hit by Ransomware
When ransomware does hit, the initial response is to stay calm and have a defined response process. Infected systems should be isolated from the network to stop further loss as soon as possible. Cybersecurity professionals should be contacted at the earliest to take an estimate of the extent of the attack and initiate recovery.
Specifically, the victims are emphatically cautioned against paying the ransom hastily. Payment is not guaranteed to lead to recovery but only to initiate further attacks. Organizations would rather seek other avenues of recovery, including recovery from backups, reporting to law enforcement, and procurement of decryption tools if applicable.
When restored, there needs to be a complete post-incident analysis. Knowing what was utilized by intruders to break through, how they managed to gain entry, and why defenses were breached is the sole way an incident can be avoided in the future.
Related: CISA & FBI Issues Alert on Play Ransomware’s Growing Threat
Future Outlook of Ransomware (2025 and Beyond)
The ransomware threat does not seem to be running out of steam. Specialists forecast ongoing innovation in Ransomware-as-a-Service platforms, which will provide sophisticated attack solutions for less sophisticated crooks to employ. Data exfiltration and extortion-only platforms will probably grow larger, as the focus moves away from encryption.
As companies move more operations to the cloud, ransomware will specifically target cloud platforms and SaaS applications more so. Artificial intelligence will also serve a two-way purpose amplifying attacker methods as well as defense.
It is not entirely bad news in the future, however. International cooperation among governments, technology firms, and security agencies is getting better, with an increased number of ransomware gangs dismantled and more intelligence being shared. However, organizational preparedness is still the best defense.
Final Thoughts
Ransomware is no longer a problem of information technology, it’s a business, operations, and even public safety problem. It is able to disable hospitals, immobilize governments, and leave private information in the wrong hands. If the economic cost is astronomical, the so-called indirect impact on safety and confidence is possibly even bigger.
The silver lining is that organizations are not helplessly at the mercy of ransomware. By investing in resiliency, training employees, securing networks, and developing incident response plans, businesses can weather ransomware attacks without succumbing to the ransom demand. The battle against ransomware continues unabated, but with engaged security, sharing, and maintenance of vigilance, companies and individuals can significantly minimize their risk.
Ransomware may evolve, but so can defenses. Staying prepared, informed, and proactive is the best shield in 2025 and beyond.
To explore more insights like this, visit our Cyber-security Page.
If you’re passionate about tech, networks, and digital infrastructure, Write for Us and share your voice with our audience.
FAQs
What is a ransomware attack in Simple terms?
It is when hackers steal or encrypt your files and pay them ransom money to release them or not post them online.
How do ransomware attacks usually spread?
Most spread through phishing emails, unpatched software exploits, or poor remote access credentials.
Can ransomware be entirely preventable?
No, but employee education, sound backups, software patching, and security monitoring strongly mitigate the risk.