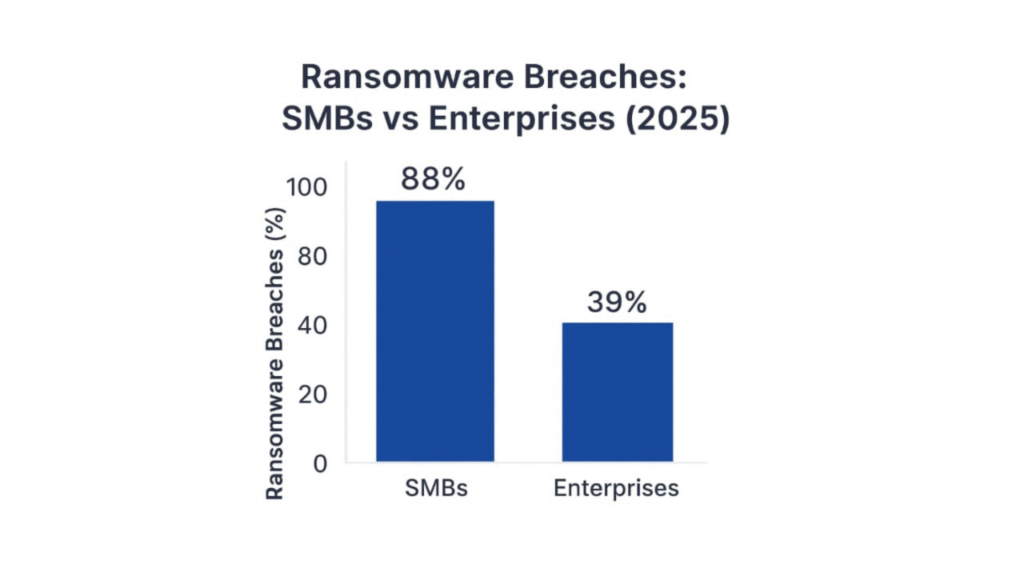
Did you know? SMBs (small and medium-sized businesses) remain especially vulnerable: in 2025, 88% of breaches affecting SMBs involved ransomware, compared with 39% for larger enterprises. Third-party involvement in breaches has also risen dramatically, appearing in nearly a third of all incidents, and serving to illustrate how supply-chain exposure is becoming a top security priority for enterprises entering 2026.
Rapid acceleration of multi-cloud adoption, spreading workloads across hybrid environments, and deep integrations of AI-powered tooling into business operations, the corporate network perimeter has, for all intents and purposes, dissolved. In today’s world, modern network security cannot afford to be reliant on legacy, perimeter-based defenses. Rather, identity-first architectures, continuous detection, stronger vendor controls, and resilience-by-design approaches will be ways to counter sophisticated cyber threats.
Key Takeaways
- The core of network security in 2026 will be based on a zero-trust, identity-centric access control model with continuous monitoring.
- Growing third-party and supply-chain risks are forcing organizations to implement strengthened vendor governance.
- The rapid growth of ransomware campaigns makes segmentation, rapid patching, and endpoint hygiene indispensable.
- Human behavior remains one of the largest vulnerabilities, and employee training is compulsory, not optional.
- Formalized incident response and governance frameworks should be used to minimize the impact of breaches by organizations.
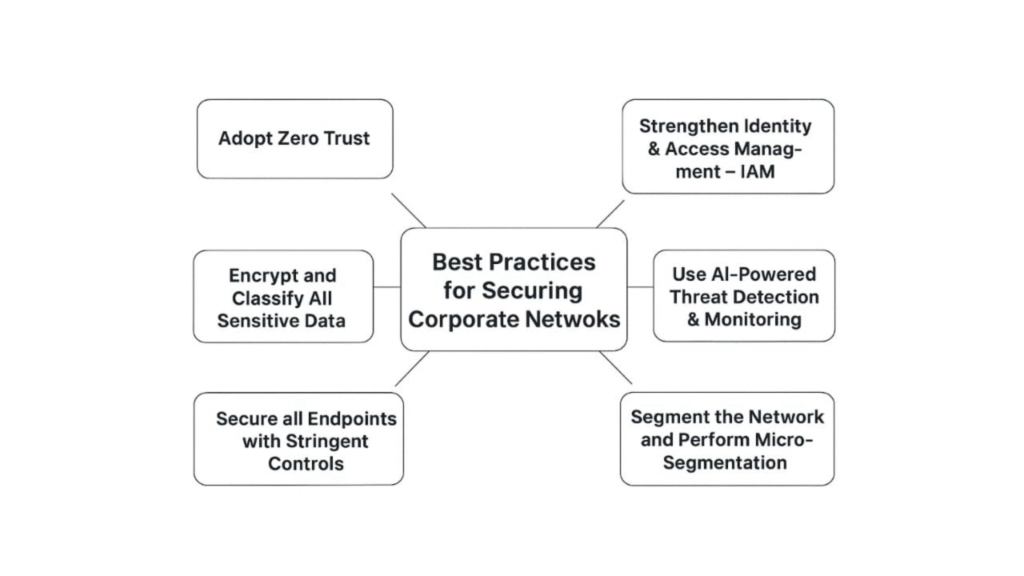
- Best Practices for Securing Corporate Networks in 2026
- Adopt Zero Trust as the core security model
- Strengthen Identity & Access Management – IAM
- Use AI-Powered Threat Detection & Monitoring
- Segment the network and perform micro-segmentation
- Secure all endpoints with stringent controls
- Encrypt and Classify All Sensitive Data
- Establish a Mature Incident Response and Recovery Strategy
- Improve Governance, Risk & Compliance (GRC)
- Invest in Employee Cybersecurity Training
- Final Thoughts
- FAQs
Best Practices for Securing Corporate Networks in 2026
In 2026, protection of a corporate network should be proactive, multilayered, and identity driven. Strong frameworks, modern access control models, advanced analytics, and resilient infrastructure design need to be part of how the organizations conduct their business. What follows are the most important practices that IT teams should take to minimize risk and make sure continuity of operations is maintained.
Adopt Zero Trust as the core security model
In 2026, the adoption of Zero Trust will be compulsory because new threats do not behave according to predictable patterns, and internal networks are just as potentially vulnerable. It dispels all assumptions through extensive verification of each user, device, and session for access. This means stringent enforcement of MFA in all systems; ever-present checking of the health of devices; strict, least-privilege rules; and real-time validation of every access request. Having discarded implicit trust, an organization reduces the possibility of lateral movement, credential abuse, and internal compromise by orders of magnitude; thus, Zero Trust is the best foundation for network security in modern times.
Strengthen Identity & Access Management – IAM
Identity has become the new security boundary, and for this reason, identity and access management strengthening should be a non-negotiable practice for 2026. Whereas attack vectors have previously focused on systems, they are increasingly focused on credentials, making robust identity controls more necessary. IAM will be successfully undertaken when MFA is integrated into SSO, privilege access is tightly managed, inactivated accounts are removed automatically, access levels are periodically reviewed, and adaptive authentication is tied to changes in user behavior and/or risk. When an organization anchors identity to the network, it minimizes attack surface areas and reduces the chances of unauthorized access and/or privilege misuse.
Use AI-Powered Threat Detection & Monitoring
Automation of cyberattacks, powered through AI and polymorphic malware, has raised the bar beyond traditional security monitoring. Organizations now require AI-powered threat detection to rapidly and accurately identify abnormal activity. In modern setups, SIEM ensures centralized logging, XDR allows cross-platform event correlation, UEBA provides unusual user pattern detection, and AI-driven anomaly detection offers real-time insights. These tools drastically cut down investigation time and help respond to threats before they escalate. By 2026, usage of AI will not be an advantage but a necessity to keep up with those attackers who themselves wield AI.
Segment the network and perform micro-segmentation
Segmentation and Micro-segmentation restrict an intruder’s lateral movement once one area of the environment has been compromised. Network segmentation separates an organization into tightly controlled zones to limit exposure, contain ransomware, protect sensitive assets, and meet even the most rigorous compliance requirements. Micro-segmentation provides even deeper isolation around workloads and sensitive applications. This approach reduces the radius of the blast of any attack and ensures that even if one system is compromised, the entire network does not fall with it-which makes segmentation one of the strongest defenses against modern breach techniques.
Secure all endpoints with stringent controls
The endpoints remain the prime target, especially in hybrid work environments where laptops, mobiles, Iot devices, and BYOD systems access the network. Endpoint security in 2026 calls for strong EDR tool deployment, enforcement of continuous patching, checking compliance of devices prior to access, encryption of local data, and monitoring for shadow IT or unauthorized devices. Attackers frequently use unpatched, out-of-date endpoints or neglected IoT devices as their initial foothold into an attack. Expanding visibility and enforcement across each connected device dramatically reduces the most common intrusion paths while enhancing overall network resilience.
Encrypt and Classify All Sensitive Data
Data protection starts with knowing what data exists and how to secure it through encryption and classification. Data should be encrypted both in transit and at rest, using strong standards like TLS and AES-256, while key management is carefully done and rotated on a regular basis. A formal data-classification system-in which data falls into categories like public, internal, confidential, and restricted-ensures that the appropriate protection level is applied to each category. In this way, organizations can effectively concentrate resources on the protection of their most valuable assets while continuing to achieve high levels of compliance against dynamic data protection legislation.
Establish a Mature Incident Response and Recovery Strategy
Even with the most robust security systems, breaches do occur. A mature incident response plan reduces the damage. Essentially, a valid IR strategy has defined roles, communication channels, and playbooks. Threats range from ransomware to insider attacks and vendor compromise. Routine tabletop exercises ensure teams respond quickly under pressure by putting backup-recovery workflows to the test. In 2026, having a well-practiced IR plan cuts down downtime and protects business continuity, keeping any cybersecurity incident from becoming a full-scale crisis.
Improve Governance, Risk & Compliance (GRC)
As regulations continue to expand globally, the betterment of GRC will help organizations turn security practices into enforceable policies. Alignment to the ISO 27001, NIST CSF, and CIS Controls means standards are met throughout the company. In 2026, GRC will have to consider AI governance, third-party risk monitoring, shadow-IT control, and data-privacy laws. A strong GRC foundation ensures that every department plays by the same rules, enhancing security posture and making compliance proactive, not reactive.
Invest in Employee Cybersecurity Training
The employees remain the first line of defense and keeping them well-trained can help block a majority of cyber incidents. Organizations should be performing regular phishing simulations, training in social engineering awareness, reinforcing practices for safe handling of data, role-based training for executives and developers, and enabling simple procedures to report suspicious activities. Employees who understand the facts about cyber risks and are empowered enough to report the threats make the entire organization resilient. A well-trained workforce remains one of the cost-effective and high-impact security investments in the year 2026.
Final Thoughts
Securing corporate networks in 2026 requires more than traditional perimeter defenses. With the use of automation, AI, and advanced exploitation techniques by cyber adversaries, organizations will have to build layered, identity-first, and intelligence-driven security architectures. Embracing Zero Trust, hardening IAM, leveraging AI for real-time threat detection, enforcing segmentation, training employees, and building robust incident response go a long way toward drastically reducing the likelihood of breaches and shoring up resilience in the longer term.
Organizations should audit their current security posture and begin implementing these measures now to stay ahead of 2026 threats.
Related Link:
- 7 Network Security Threats and How to Prevent Them
- Network Security Best Practices for Businesses in 2026
- Network Security Architecture: How to Build a Secure Network
- How to Conduct a Network Security Audit: Step-by-Step Guide
FAQs
What is the best way to secure a corporate network in 2026?
The best way to secure a corporate network in 2026 is to adopt a Zero Trust, identity-first security model combined with strong IAM, AI-powered threat detection, network segmentation, and continuous monitoring. Traditional perimeter-based security alone is no longer effective.
Why is Zero Trust important for corporate network security?
Zero Trust is important because modern attacks often originate from stolen credentials, compromised devices, or third-party vendors. By verifying every user, device, and access request, Zero Trust minimizes lateral movement, insider threats, and ransomware spread across corporate networks.
What are the biggest corporate network security threats organizations face in 2026?
The biggest threats in 2026 include ransomware attacks, third-party supply-chain breaches, credential theft, unpatched endpoints, and human error. The rise of AI-driven cyberattacks makes proactive detection and employee security training essential.