In recent years, DDoS attacks have grown dramatically in both scale and sophistication. Compared to 2024, there was a 358% increase in DDoS attacks, some reaching over 1 terabit per second (Tbps) or 1 billion packets per second (Bpps), according to Cloudflare Radar in 2025.
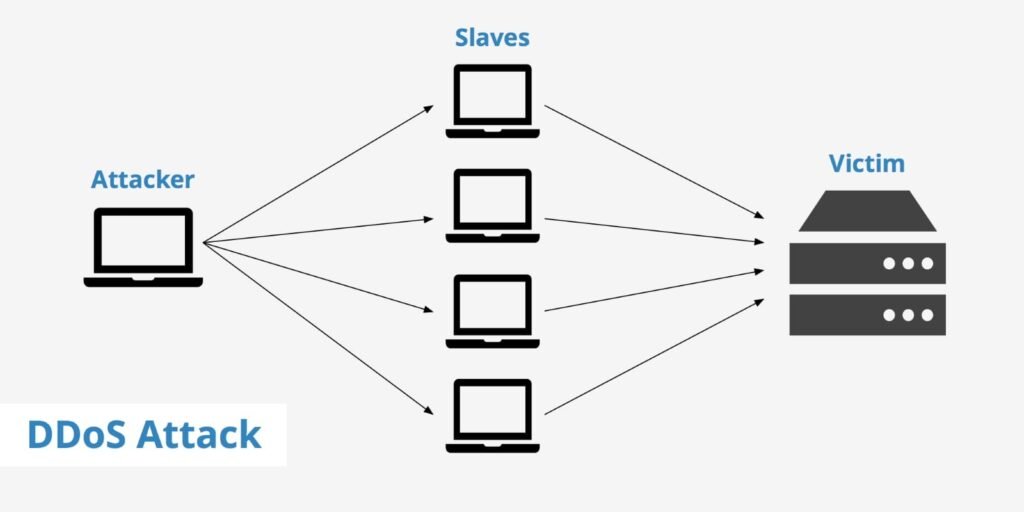
These attacks often exploit vulnerabilities in networks, cloud workload, IoT devices, and edge services. As the organization moves into hybrid and multi-cloud architectures, traditional perimeter-based security models have become obsolete. Only proactive, intelligent, multilayered defenses can effectively contain these threats.
Key Takeaways
- Real-time traffic monitoring and behavioral analytics have become essential for early detection, as DDoS attacks continue to scale and grow in complexity.
- Cloud-based mitigation, combined with AI-powered detection, can filter malicious traffic and respond to threats before they are able to disrupt services.
- Principles of Zero trust and network segmentation reduce the attack surface and limit potential damage.
- DNS and edge service security and employing WAFs protect against amplification and application-layer attacks.
- A strong Incident Response plan, integrated with a comprehensive security strategy, ensures business resiliency and continuity in the long term.
- 8 Network Security Measures to detect and prevent DDoS attacks
- 1. Real-time traffic monitoring and behavioral analytics
- 2. Cloud-Based DDoS Mitigation
- 3. Zero Trust Principles in DDoS Defense
- 4. Network Segmentation and Micro-Segmentation
- 5. DNS and Edge Protection
- 6. AI-Powered Detection and Response
- 7. Incident Response and Mitigation Strategy
- 8. Integrating DDoS Protection into Overall Security Posture
- Final Thoughts
- FAQs
8 Network Security Measures to detect and prevent DDoS attacks
Detecting and preventing DDoS attacks requires a proactive, multi-layered approach that combines technology, strategy, and continuous monitoring. Organizations must implement security measures that not only identify attacks in real time but also minimize their impact on critical systems and services.
1. Real-time traffic monitoring and behavioral analytics
Real-time DDoS attack detection is important because most attacks disguise themselves as real traffic, especially at the application layer. Modern security operations rely on monitoring traffic flow and behavioral analytics for pattern recognition that may involve sudden spikes in requests, multiple connections from certain IPs, or malformed packets. The conventional treatment to threshold-based methods mostly becomes insufficient, and analytics-driven monitoring becomes quite indispensable with a view to achieving rapid identification of potential attacks before they cause service disruption. Many cloud providers offer integrated monitoring solutions with automated mitigation, including Cloudflare, AWS Shield, and Google Cloud Armor.
2. Cloud-Based DDoS Mitigation
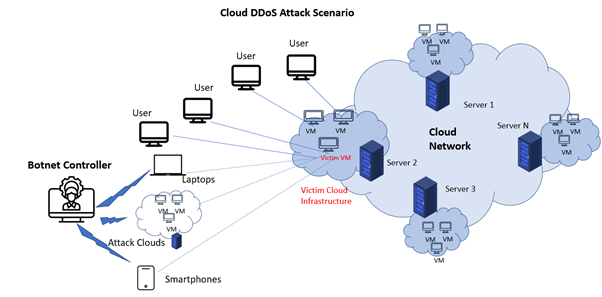
On-premises infrastructure cannot absorb multi-gigabit attacks. Cloud-based DDoS mitigation-also colloquially referred to as “scrubbing services”-redirects suspicious traffic through global scrubbing centers where malicious packets are filtered. This approach leverages BGP redirection, Layer 3/4 filtering, and AI-based anomaly detection in maintaining service availability during high-volume attacks. These services can handle attacks at a scale that would overwhelm traditional networks and are thus indispensable in the protection of web services, APIs, and cloud-hosted applications.
3. Zero Trust Principles in DDoS Defense
One effective mitigation strategy against the risks of DDoS is the adoption of ZTNA. No traffic is implicitly trusted in the zero-trust model from internal sources. Every session, device, and request is continuously validated and verified. Integration of zero trust in DDoS defense makes sure that malicious and anomalous traffic is challenged well before reaching the critical systems. It reduces attack surface areas, making it difficult for attackers to compromise internal resources.
4. Network Segmentation and Micro-Segmentation
Segmentation of the network into zones isolates the effects of DDoS attacks. It goes further to segment public-facing servers from internal databases and third-party APIs and IoT devices, ensuring that any disruption of traffic would be confined to the affected segments. This principle further extends to Micro-segmentation down to individual workloads or applications, especially those relating to hybrid clouds. Even in the event of one segment being compromised, the rest of the critical resources remain online.
5. DNS and Edge Protection
DNS infrastructures are among common targets for amplification and reflection attacks. Anycast DNS, DNSSEC, and managed DNS services with integrated auto-failover build resiliency. Web Application Firewalls screen inward-bound requests and filter out malicious traffic so that application-layer attacks do not impact a service’s uptime. The WAFs can be used for rate limitations, bot management, and geo-blocking to cut down attack surfaces.
6. AI-Powered Detection and Response
Modern DDoS attacks heavily use botnets or AI-driven traffic generation, which renders the older methods of detection futile. AI and machine learning systems can spot subtle anomalies; unusual timing of requests, distributed bursts coming from numerous different IPs, or even slow “low-and-slow” attacks that whittle down resources over time. Integration of AI-powered detection into security operations centers lets an organization act quicker against threats and often to do so before those threats escalate into service disruptions.
7. Incident Response and Mitigation Strategy
Despite robust defenses, attacks may still happen. A well-prepared incident response plan ensures minimal disruption. Organizations should define failover procedures, backup DNS and CDN configurations, traffic rerouting through scrubbing services, and communication protocols with upstream ISPs. Forensic analysis of the attack after it has occurred provides insight into the attack vectors, thus helping in strengthening future defenses. With these strategies, continuity for businesses would remain unaffected, even under sustained attack.
8. Integrating DDoS Protection into Overall Security Posture
DDoS defense needs to be part of a greater strategy of security and risk management. Given the increasing dependency on third-party services, cloud workloads, and APIs, organizations should make sure of good vendor governance, periodic audits, appropriate access controls, and continuous validation of device posture. Coupling proactive network defenses with comprehensive risk management ensures that DDoS protection does not just react but becomes an integral part of organizational resilience.
Final Thoughts
The scale and sophistication of DDoS attacks in 2025 and 2026 have underlined the requirement for modern, multilayered defenses. It is no longer enough to just lean on traditional, perimeter-based security. Real-time monitoring, cloud-based scrubbing, Zero Trust principles, network segmentation, DNS and WAF protection, AI-driven detection, and mature incident response strategies must be put into operation by an organization.
Such measures will guarantee continuity of service, minimize financial and reputational damage, and cement overall network resilience against evolving DDoS threats.
Related Link:
- What Is a Denial of Service Attack? Complete Guide
- How Botnet Armies Work & How to Stay Safe from Cyber-Attacks
- 7 Network Security Threats and How to Prevent Them
- What is a Firewall?
- How AI Is Shaping Cybersecurity 2026: Threats and Defense
FAQs
What are the early signs of a DDoS attack?
Early signs include sudden traffic spikes, slow website performance, unusual IP patterns, repeated requests to the same endpoint, and services becoming unavailable. Real-time monitoring helps detect these signs instantly.
Can cloud-based services fully protect against DDoS attacks?
Yes, cloud-based mitigation services like Cloudflare, AWS Shield, and Google Cloud Armor can absorb large-scale attacks that on-premises networks cannot handle. They filter malicious traffic before it reaches your systems.
How does Zero Trust help in preventing DDoS attacks?
Zero Trust verifies every user, device, and request. No traffic is trusted automatically, which reduces the attack surface and blocks malicious traffic before it reaches critical internal systems.