Every organization relies on email to contact customers, internal organization, communication with suppliers, etc. At the same time, email is also the primary vehicle of attack by cybercriminals. Actors in 2025 use AI-powered phishing, impersonation, and malware distribution to overcome legacy defenses. One breach through phishing through an email puts a company back by around $4.88 million on average today.

To protect themselves, businesses must adopt modern email protection software that goes beyond simple spam filters. In this guide, we’ll explore what email protection software is, why it’s essential, how to evaluate it, and best practices to maximize its impact.
Understanding Email Protection Software
At least, email security software is an (usually cloud-based) security gateway that scans and blocks e-mail traffic in and out of your organization. But better ones in 2025 do so much, so much more:
- They scan on heuristics and machine learning-based content, attachment, and URL scanning to identify new or unknown threats.
- They enforce policy (e.g. encryption, DLP) to block sensitive information leakage.
- They ingest threat feeds to stay current with evolving attacks.
- They offer administrative controls, dashboards, and forensics capabilities for visibility and compliance.
In short it’s not merely “email filtering” it’s intelligence-driven email defense, enforcement, and insight.
Why It Matters: The Emerging Threats Via Email
The statistics speak for themselves:
- Phishing continues to be among the top attack vectors. Statistics indicate 36% of cyber-security breaches are due to phishing.
- More than 3.4 billion phishing email are received every day and account for about 1.2% of global email traffic.
- More than 1,003,924 phishing incident were witnessed during Q1 2025, the highest ever recorded since the end of 2023.
- Incidents evolve: attacks through email increasingly now involve AI, impersonation, polymorphic techniques, and infostealers. Infostealer attacks through phishing, for instance, increased by a mean of 84% in 2024 compared to the year before.
- Attackers are also bypassing basic defense: some phishing attacks now bypass DMARC validation, and most pretend to be internal staff or brands.
If risk this significant is involved, relying on legacy email filters isn’t sufficient.
What Makes an Email Protection Solution “Best-In-Class”?
When choosing a powerful email protection software, look for these essential features:
- Advanced Threat Detection: Utilize sandboxing, AI/ML, behavioral monitoring, and heuristics to detect zero-day or polymorphic threats.
- Phishing & Spoof Protection: URL rewriting, click-time scanning, domain reputation, and SPF, DKIM, DMARC enforcement to prevent impersonation.
- Malware and Attachment Inspection: Scan embedded files, macros, archives, and embedded payloads.
- Data Loss Prevention (DLP): Automatically block or quarantine emails with sensitive information (financial information, personal identities, trade secrets).
- Encryption & Secure Messaging: Automatically encrypt messages by content or enable users to send secure messages on demand.
- Threat Intelligence & Real-Time Updates: Ongoing updates to signatures, blacklists, and behavior in order to counter new campaigns.
- Centralized Management & Reporting: Single pane of glass, audit trails, alarms, root cause analysis of incidents.
- Scalability & Flexibility: Cloud, hybrid, or on-prem deployment support; integration with Microsoft 365, Google Workspace, and legacy email systems support.
- High Availability & Reliability: Redundancy, SLA commitments, smooth operation.
A mature response will combine prevention, detection, enforcement, and insight not in isolation.
Benefits to Organizations
Having the latest email security software applied has phenomenal paybacks:
- Less Risk & Exposure of Breach: Preventing phishing, malware, and data breaches lowers your exposure right away to costly breaches.
- Cost Savings in Response to Incidents: Fewer security incidents translate to fewer remediation hours, forensics, system rebuilds, and regulatory fines.
- Increased Productivity: Less spam, less false positives, and less noise allow workers and IT to focus on work.
- Visibility & Control Centralized: Central control belongs to admins, threat inspection is performed, and responding is simpler with one pane of glass.
- Scalable Security: As your organization increases, you don’t need to rebirth your email security architecture every year.
- Stronger Compliance & Reputation: Encrypted communications, audit trails, and policy enforcement facilitate regulatory compliance and contribute to trust building.
Email Protection Software Platforms
1. Microsoft Defender for Office 365

Microsoft defender for office 365, formerly known as Office 365 Advanced Threat Protection, is a cloud security solution that protects against advanced email threats such as phishing, malware, and business email compromise (BEC). It features Safe Attachments, which detonates malicious attachments in a sandbox environment prior to delivery, and Safe Links, which rewrites URLs and dynamically blocks malicious links. It also extends collaboration software (Teams, SharePoint, OneDrive) to further protect beyond email. There are other features for organizations with Defender Plan 2 capabilities, such as threat hunting, attack simulation, and automated response and investigation. Its multi-layered anti-malware and zero-day protection offers signature, heuristic, and behavior-based detection. Since it comes packaged in the Microsoft 365 bundle, it offers seamless deployment for organizations already leveraging Microsoft products.
2. Proofpoint Email Protection

Proofpoint is a world-famous name in email security, hugely acclaimed for its richness in features and impressive third-party test performance. In the 2025 Gartner Critical Capabilities for Email Security Platforms report, Proofpoint was a top-ranking vendor across four of five use cases (e.g., core email protection and outbound security) for rival vendors. Its answer leverages machine learning to scan sender reputation, content, intent, and email metadata to identify phishing, malware, and impersonation attacks. Proofpoint also provides email fraud defense (to defend domains and identify lookalike domains), DLP and encryption for send-only email, and integration with enhanced security and compliance controls. Due to the combination of preventive, detective, and enforcement characteristics, Proofpoint is chosen in environments calling for robust data security and threat intelligence.
3. Mimecast Email Security
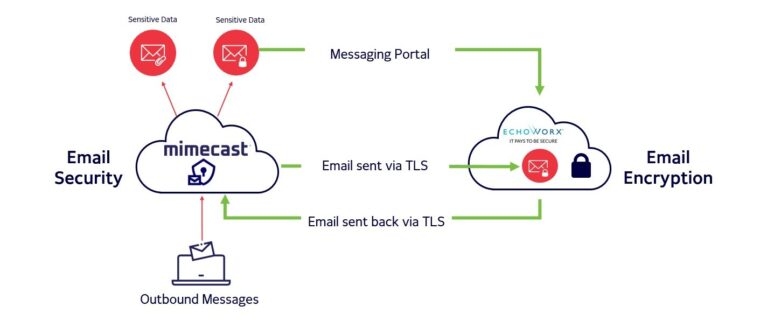
Mimecast offers end-to-end, cloud-based email security software with a focus on threat prevention, continuity, and compliance.
Mimecast continues to use adaptive threat intelligence, behavioral analysis, and real-time indicators in 2025 to block phishing, malware, and spear-phishing attacks from being delivered to users. Its Targeted Threat Protection examines changes to content, attachments, and URLs, and has the ability to quarantine suspicious emails. Mimecast also includes email continuity (so business doesn’t stop in the case of outages), archiving (for storage and e-discovery purposes), and data leak prevention (for blocking or encrypting sensitive outbound emails). Because it includes a single cloud console, administrators can apply policy, track threats, and manage encryption from one location, simplifying complexity in distributed or large environments.
4. Barracuda Email Security Gateway
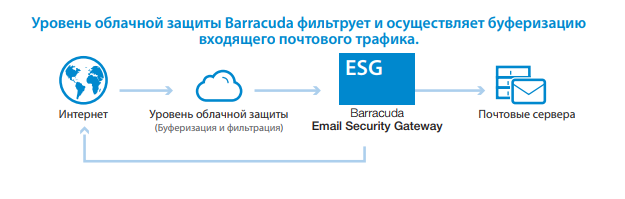
Barracuda’s Email Security Gateway is a proven solution that is being utilized by numerous small to mid-sized organizations due to the balance it offers between manageability and effectiveness.
It uses multi-layered filtering such as reputation, content scanning, heuristics, and anomaly detection to fend off spams, phishing, ransomware, and zero-day attacks. Never so much in the spotlight with each new feature, Barracuda continues to improve with Microsoft 365 integration support, impersonation detection, outbound filtering, and encryption of secure mail streams. Its attachment sandboxing and scanning of unknown file types identify threats on the horizon safely. The reporting and dashboard feature function seamlessly, and thus it is appropriate for IT staff who require top-shelf security with minimal overhead.
5. Cisco Secure Email (IronPort)
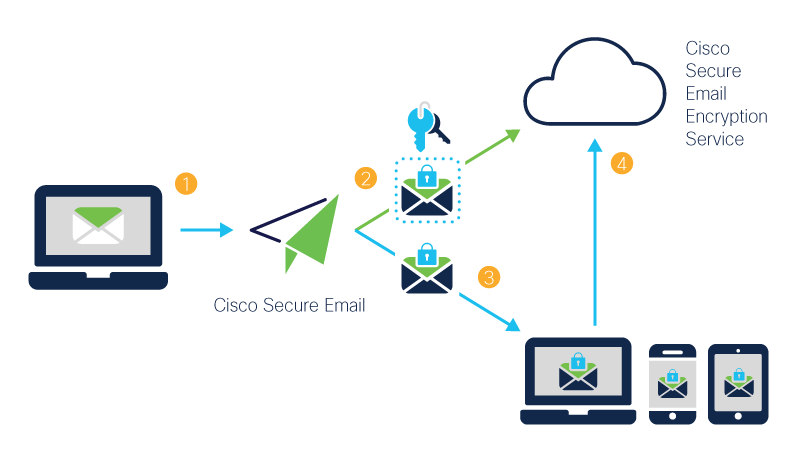
Cisco Secure Email is enterprise-level email security software used extensively by big business, governments, and regulated industries.
It utilizes the Cisco Talos threat intelligence community to get world-class visibility into new threats and malware campaigns. It employs this intelligence to conduct real-time analysis, machine learning, and reputation scoring to identify or block malicious emails before they’re delivered to users. The solution provides encryption support, DLP, content filtering, and policy enforcement to satisfy regulatory and compliance demands (e.g., GDPR, HIPAA). Extended across the Cisco SecureX platform (or in combination with Cisco’s network and endpoint security controls), organizations get a single pane of threat visibility into email, identity, and network, allowing for more unified defense.
How to Choose the Best Solution
The following are some determinants (in narrative form):
- Detection Effectiveness: Request third-party test reports or histories of zero-day attack detection, including total false positives.
- Technology Depth: Seek out solutions to integrate AI, sandboxing, heuristics, URL/link analysis, and content scanning.
- Platform Compatibility: Seamless integration into your email platforms (Office 365, Gmail, hybrid deployments).
- Policy & Automation: Let the system automatically take rule-based actions (block, quarantine, encrypt) on auto-pilot.
- Threat Intelligence Integration: Ongoing feeds from global threat feeds and user-to-user collaborative threat intelligence.
- Monitoring & Forensics: Dashboards, historical logs, threat timelines, investigation tools, alerting.
- User Experience: Low friction, end-user transparent security, good false positive management.
- Support & SLA: Responsive support, high availability promises, redundancy.
- Scalability & Pricing Model: Clear, upfront pricing by user or mailbox; up or down scaling.
- Compliance & Certifications: ISO, SOC, GDPR, HIPAA, etc., as appropriate depending on your industry.
You should do a proof-of-concept with your priority emails prior to full deployment.
Best Practices Beyond Software
Technology for technology’s sake won’t heal all wounds. Augment software with:
- User Awareness & Phishing Simulations: Training does work although research indicates training by itself is not highly effective. For instance, one research demonstration revealed that phishing training didn’t necessarily reduce click-throughs on challenging lures.
- Multi-Factor Authentication (MFA): Even if credentials are compromised, MFA stops the majority of account takeovers.
- Strict Password Hygiene & Rotation: Use separate, distinct passwords; no reuse.
- Limit exposure in case a profile gets breached.
- Log Monitoring & Anomaly Detection: Search for suspicious logons, unauthorized level of outbound mail, or outbreaks of rejected mail.
- Incident Response Planning: Predefine actions to quarantine the breached accounts, destroy credentials, verify impact, and restore service online.
- Periodic Policy Review: Threats are constantly changing; review your rules and thresholds periodically.
With quality-quality email defense software, these steps offer layering protection.
Conclusion
As cyber attacks increasingly involve AI, behavioral impersonation, and supply chain vulnerabilities, email security in the future will be no exception when it comes to intelligence and resilience required. AI will also be the attack and defense platform and will fuel next-generation detection engines that can detect contextual anomalies. Impersonation attacks like deepfakes and style-cloning will reach their peak. Next, companies must go beyond point solutions and embrace converged, adaptive email security platforms that consolidate identity, endpoint, and network intelligence to stay resilient in 2025 and beyond.
To explore more insights like this, visit our Cyber-security Page.
If you’re passionate about tech, networks, and digital infrastructure, Write for Us and share your voice with our audience.
FAQs
Can small or medium-sized businesses gain from email protection software?
Yes, Smaller companies are mostly targeted by hackers because their defenses aren’t so strong. Although email remains the number one point of vulnerability, small and medium businesses also receive great protection through using strong email security software.
Does email security software guarantee 100% email safety?
No, no solution will ever be flawless. Advanced phishing or social engineering attacks may sometimes compromise filters. But a contemporary, multi-layer email defense solution reduces risk significantly. In combination with sound policy, MFA, and end-user training, it offers one of the best practical defenses possible.