Supply chain attacks have increased by over 300% + in the past five years, which makes vendor-level security more critical than ever. A recent threat intelligence report showed software supply chain attacks set new records, with October 2025 incidents more than 30% above previous peaks and more than double the monthly attacks seen earlier in 2024–2025.
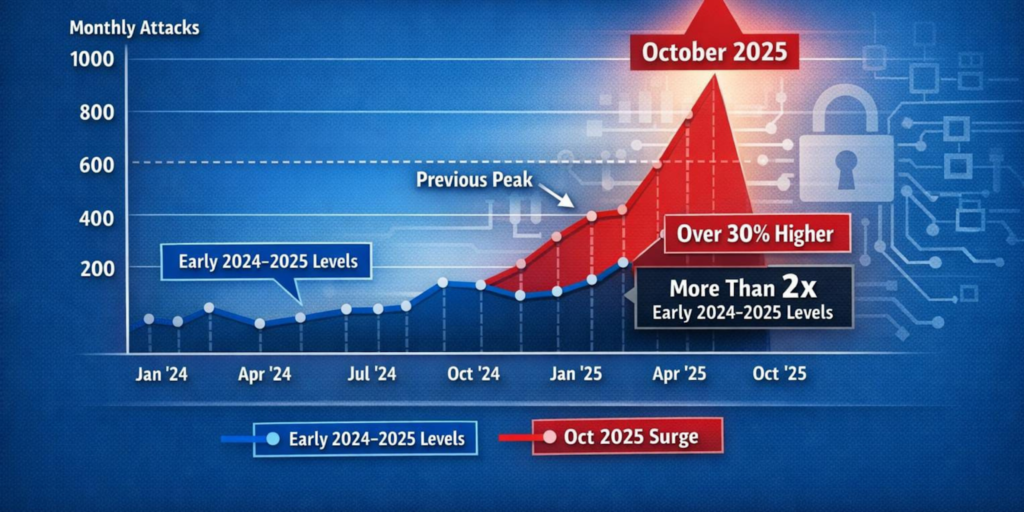
Image by: Author
A supply chain attack is the most dangerous threat facing businesses today. Rather than attacking a company directly, cybercriminals attack its trusted third-party vendors, software providers, or service partners. Once inside, they silently exploit these indirect pathways to get the organization’s systems and data.
These attacks are serious because they’re difficult to detect and often extend rapidly with the help of interconnected networks. Incidents like SolarWinds and Kaseya expose that even well-protected companies can face huge disaster if just one supplier is compromised. This article explores how supply chain attacks occur and offers practical strategies to prevent them.
What is a Supply Chain Attack?

A supply chain attack occurs when a cybercriminal targets a third-party vendor, partner, or service provider as a way to compromise a wide organization. Instead of going after the company directly, attackers take advantage of the trust and access that suppliers often have.
These attacks can occur through compromised software updates, infected hardware, or unauthorized access to shared systems. Once the attacker gets in through the supplier, they can steal data, install malware, or break operations-often without being observed right away.
Because businesses depend highly on external tools, services, and cloud platforms, even one weak link in the chain can open the door to extreme damage.
How Do Supply Chain Attacks Work?
Supply chain attacks work by taking advantage of the trusted connections between a company and its external partners. These partners might be software developers, IT experts, hardware suppliers, or cloud vendors. Because they often have access to a company’s internal systems or networks, compromising one of them can create a hidden entry point for an attacker.
A common method is injecting malware into a software update that gets distributed to all users. Another is gaining access to a vendor’s system and using it to silently move into the networks of their clients. There are some attacks that even start at the hardware level, where malicious code is pre-installed on physical devices before they reach the end user.
What makes these attacks so dangerous is that they often bypass traditional security defenses. Since the threat comes through a trusted source, it can take weeks or even months before it’s detected-by then, the damage may already be done.
Quick Link: 500 Internal Server Error
Why Are Supply Chain Attacks So Dangerous?
Supply chain attacks target the very systems and vendors organizations rely on, making them particularly insidious. Because they exploit trusted relationships, even a single breach can cascade across multiple organizations.
- They exploit trusted relationships, making them hard to detect.
- A single compromised vendor can impact hundreds or even thousands of companies.
- Malware often spreads silently through software updates or system integrations.
- Traditional security tools may not flag the threat because it appears to come from a verified source.
- The attacks can remain hidden for weeks or months before detection.
- Recovery can be slow and costly, involving multiple systems and partners.
Past Real Examples of Supply Chain Attacks
To understand the real-world incidents, helps to highlight how damage and widespread supply chain attacks can be. Here are some well-known examples that amazed the cybersecurity world:
SolarWinds (2020)
Attackers place malicious code into a software update from SolarWinds, which was then unknowingly installed by over 18,000 organizations, covering U.S. government departments and Fortune 500 companies. This attack remained undetected for months.
Kaseya (2021)
Cybercriminals exploited a vulnerability in Kaseya’s IT management software to spread ransomware through managed service providers (MSPs) affecting hundreds of businesses in one coordinated hit.
Target (2013)
Hackers accessed Target’s internal systems through a third-party HVAC vendor. The result was a breach of payment information from more than 40 million customers.
CCleaner (2017)
Hackers compromised the installer of CCleaner, a popular software tool, and distributed infected versions to millions of users worldwide before it was discovered.
These all examples show how attackers can infiltrate even the most secure organizations by slipping through third-party relationships or broadly used software updates.
How to Prevent Supply Chain Attacks

Image by: Author
Supply chain attacks can be decreased with the right preventive steps. Here’s the core checklist every business should follow:
Evaluate Third-Party Risk
Check the security practices, certifications, and history of all vendors before working with them.
Limit Vendor Access
Give third parties only the access they need-nothing more. Use powerful contracts with clear cybersecurity clauses.
Verify Software and Hardware
Always ensure updates and devices come from trusted, verified sources. Be vigilant for tampering or unauthorized changes.
Use Continuous Monitoring Tools
Install systems that can detect unusual activity or unauthorized behavior in real time.
Train Employees
Educate staff on phishing, social engineering, and third-party risks. Awareness is key to defense.
Supply chain attacks are no longer rare or limited to large organizations. As more businesses depend on third-party software, services, and cloud providers, the risk grows silently in the background.
However, the best thing is that these attacks can be prevented. By carefully assessing your vendors, applying strict access controls, and using real-time monitoring tools, your business can stay protected against even the most complex supply chain threats.
That’s what makes smart businesses invest in supply chain security.
Visit our cyber-security page, for more proficient guides and resources. If you’re passionate about cybersecurity and would like to contribute, write for us and share your insights with our growing tech community.
FAQs
What is the biggest risk in a supply chain attack?
The major risk is that attackers can bypass your internal security by attacking a trusted third-party vendor. Once inside, they may steal sensitive data, install malware, or spread across your network undetected.
Can small businesses be targeted in supply chain attacks?
Yes, Small businesses are often targeted because they have fewer defenses and can be entry points to larger companies they work with. Attackers often go after the weakest link in the chain.
How often should vendors be reviewed or audited?
Vendors should be examined at least once a year, or instantly after any security incident. Regular audits help guarantee that third-party partners continue to follow proper cyber-security practices.