Magento’s vulnerability allowed hackers to implant a backdoor into e-commerce websites, putting online merchants at risk.
Key Takeaways
- Magento vulnerability allowed hackers to exploit e-commerce websites.
- The malicious code in the system hacked the payment data.
- Sansec issued suggestions to avoid attacks in the future.
This vulnerability identified as CVE-2024-20720, attacked several e-commerce websites injecting a backdoor into the Magento server and compromising the payment data of websites.
The backdoor into E-commerce websites discovered that hackers inserted XML code into the layout database table. Threat actors combined the beberlei/assert package to execute the checkout cart command.
The malicious code executes whenever the command /checkout/cart is requested, compromising the payment data of the website’s customers and owners.
The sed command inserted a code execution backdoor meeting a CMS controller that guarantees the malware is injected. It transferred the financial information and provided a stripe payment skimmer to the exploited Magento store.
The Detail of Injected Malicious Code
Payment skimmer malware has occurred many times in the history of cybercrime. The revelation of this vulnerability comes after an increase in digital skimming operations, commonly known as Magecart assaults, which have been on the rise since 2015.
They target online shopping platforms by injecting malicious payload in checkout commands to steal credit card and payment information.
Once the Russian government found skimmer malware in a foreign e-commerce store stealing credit card and payment information, they charged six prospects in this regard.
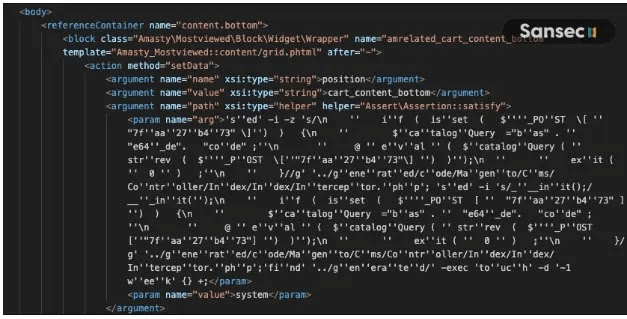
Magento vulnerability exploited backdoor into e-commerce website allowed hackers to access the infected system and inject additional malicious payloads.
Sansec also says that such backdoor code injection is a fake Stripe payment skimmer designed to steal payment information from unsuspecting shoppers compromising the Magento store.
In this campaign, the attackers linked to many IP addresses that exploited the Magneto vulnerability. It demonstrates an integrated attempt to inject a threat to various e-commerce sites.
Did you know recently, Russian hackers got access to Microsoft source code?
Mitigation to Avoid a Malicious Code in the Future
Sansec issued the suggestion for affected online merchants on 4th April to mitigate the threat of a backdoor into e-commerce websites.
- Install or run the eComscan scanner on websites to safeguard Magento store owners. It’s a tool used to find hidden backdoors in their systems or websites.
- Update your Magento versions 2.4.6-p4, 2.4.5-p6, or 2.4.4-p7 and patch the existing vulnerability to protect from future attacks.
The Magento vulnerability is the hallmark of the online industry resulting in an eye-opening incident for merchants to update and maintain the security measures.
Cyberattacks are never-ending as the tech industry is evolving with time. Malware infiltrates E-commerce websites, acting as a backdoor to steal financial data. Security measures in the e-commerce industry are required to safeguard the customer’s privacy and maintain the credibility of online shopping.
Want more updates about what’s happening around us? Visit our website Daily Digital Grind!