Subdomain takeovers pose a significant cyber security threat, allowing attackers to gain control over subdomains linked to main domains. This vulnerability facilitates various malicious activities such as traffic redirection, phishing attacks, data breaches, and more. It can cause reputational damage, especially for businesses heavily dependent on their online presence.
The risk escalates due to inadequate security measures and DNS misconfigurations. This potentially leads to the hijacking of subdomains from external services like cloud services, e-commerce, or content distribution networks.
Consequently, this creates several high-severity risks. With its trackless and relatively straightforward exploitation, subdomain hijacking has emerged as an attractive attack vector for hackers.
In this comprehensive guide, we explore the concept of subdomain takeovers and provide practical tips to safeguard your website effectively.
The Concept of Subdomain Takeovers
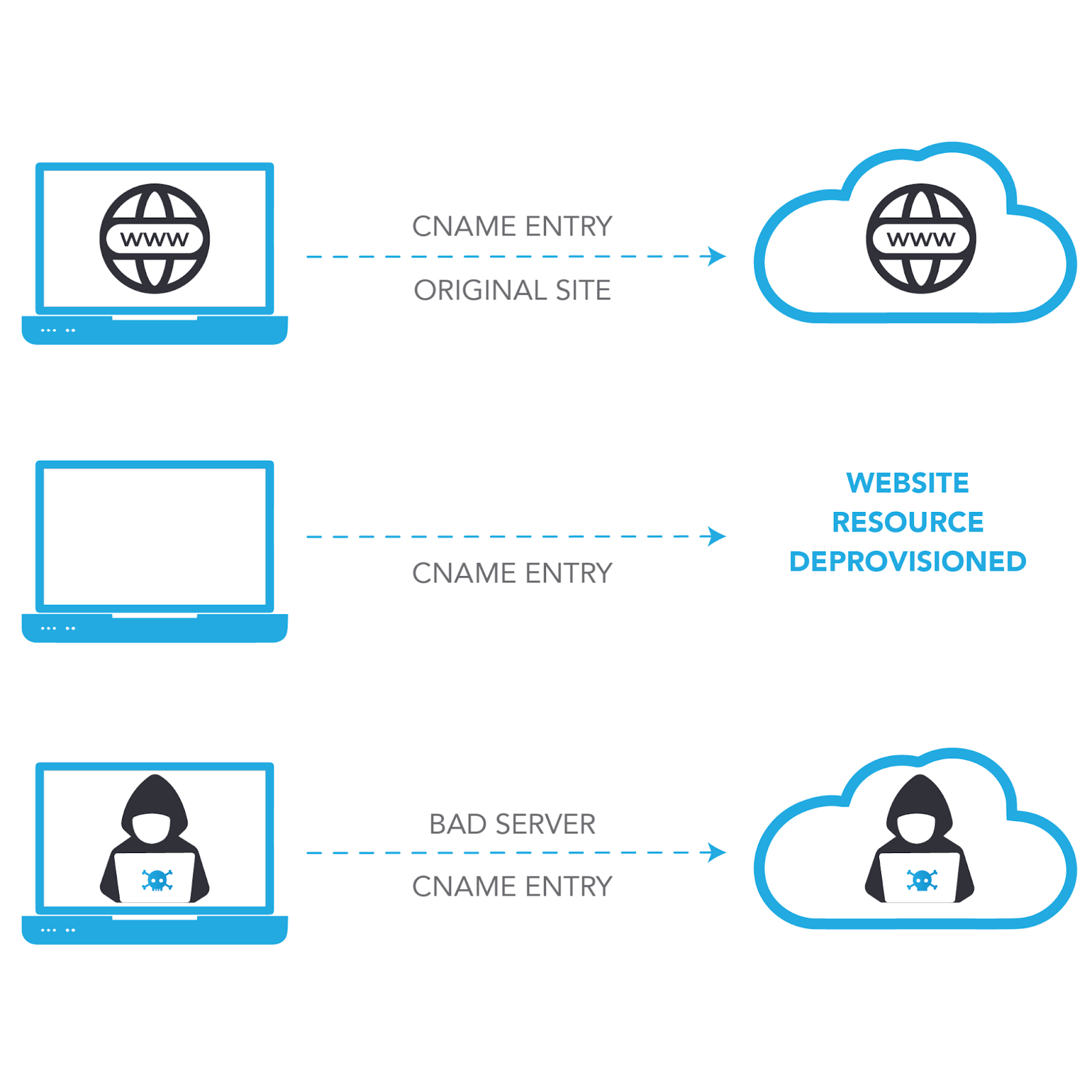
Source: Process behind subdomain takeovers
Subdomain takeover occurs when an intruder gains authority over a subdomain belonging to a targeted domain. Typically, this scenario grows when the subdomain is listed in the Domain Name System (DNS) as a canonical name (CNAME) but lacks content from a hosting source.
For instance, the ‘subdomain.example.com’ originally pointed to a GitHub page. If the page owner removed it, an attacker could create a GitHub page, include a CNAME file directing to ‘subdomain.example.com’, and seize control of it.
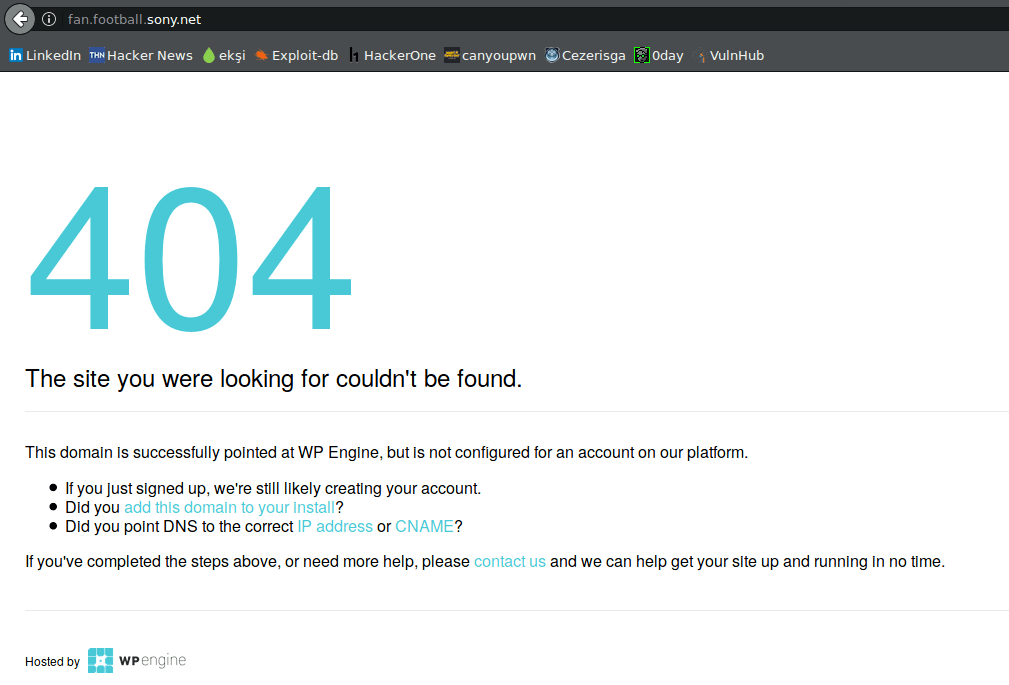
Source: A “404 page not found error” shows a subdomain takeover vulnerability.
This gap arises because a virtual host hasn’t been established or disassembled. By providing their own virtual host and hosting content for the subdomain, an attacker can wrest control over it. This maneuver grants them the potential to intercept cookies from the main domain, execute cross-site scripting attacks, or evade content security policies.
Read also: 5 Ways to Keep Kids Safe Online in 2024
Understanding the Causes of Subdomain Takeovers
Subdomain takeovers materialize when attackers identify and exploit weaknesses in your subdomain setup, commonly through:
- Improperly Configured DNS Entries: Outdated or idle CNAME or A records directing to defunct third-party services.
- Expired or Neglected Subdomains: Subdomains that have fallen into disuse and lack adequate security protocols.
- Typographical Errors: Attackers capitalize on slight misspellings of their subdomains to reroute traffic.
Actionable Steps to Protect Your Website from Subdomain Takeovers
Securing your subdomains is important for keeping your website safe. Here are some easy ways to prevent subdomain takeovers, protect your site, and make sure your digital assets stay secure.
1. Routine Audit and Cleanup of DNS Records
Regularly examine your DNS records, particularly CNAME entries, to verify the integrity and security of your domain configurations. Conducting periodic reviews of DNS configurations, including CNAME and TXT records, is imperative.
2. Monitoring Third-Party Services
Vigilantly monitor the status and configuration of third-party services. It includes various cloud platforms and Content Delivery Networks (CDNs), used for your subdomains to ensure continuous functionality and proper setup.
3. Utilize Domain Registrar Locking
Employ domain-locking features provided by domain registrars to prevent unauthorized alterations to your DNS settings. It maintains protection against potential subdomain takeover attempts. Moreover, enabling multi-factor authentication adds an extra layer of security.
4. Implement Certificate Transparency Monitoring
Monitor Certificate Transparency (CT) logs to promptly detect any unauthorized SSL/TLS (Secure Sockets Layer/Transport Layer Security) certificate issuances for your domain and subdomains. It enables swift intervention in case of potential takeover attempts.
5. Employ External Attack Surface Management
Deploy External Attack Surface Management (EASM) solutions to comprehensively assess and monitor your organization’s digital footprint. These solutions identify and mitigate vulnerabilities in subdomains that could be exploited for takeovers. EASM tools proactively detect and address misconfigured or abandoned subdomains.
If you properly implement these measures, you can effectively safeguard your website against subdomain takeovers and strengthen your digital assets.
The Dangers of Subdomain Takeovers
Subdomain takeover introduces various hazards for your website and its content. Understanding them better can protect your domain. Below, we have discussed a few;
- Content Control Compromise: If hackers gain control of your subdomain, they can manipulate its content freely. They may inject malicious scripts, damage the site, or substitute content with harmful material. For online businesses, this threatens reputation.
- Cookie Theft from Unwary Visitors: Attackers can exploit subdomain takeovers to steal cookies from visitors to the compromised subdomain. These cookies often contain sensitive visitor information like session tokens, log in details, and personal data ripe for exploitation.
- Phishing Opportunities: Subdomain takeovers offer an ideal platform for launching phishing campaigns. Attackers leverage your domain to craft convincing replicas of legitimate websites on compromised subdomains. Which deceives users into divulging sensitive information.
- DDoS Vulnerabilities: The compromised subdomain becomes a potential launchpad for distributed denial-of-service (DDoS) attacks, disrupting services and causing downtime.
Examples of Subdomain Takeovers
Several subdomain takeovers highlight the significance of vigilance and proper setup in protecting your website from such exploits.
- GitHub Pages: Developers frequently utilize personalized domains in conjunction with GitHub Pages. If a GitHub repository is erased while the DNS record persists, an intruder could establish a new repository with an identical title and serve malevolent content.
- Amazon S3 Buckets: In situations where a DNS record indicates an S3 bucket that has been removed, a malicious actor could lay claim to the bucket name and commandeer the subdomain.
Conclusion
It’s essential to remain aware of your subdomains and their DNS entries to maintain the security of your online presence. Neglecting to do so can leave your website vulnerable to subdomain takeovers. It may lead to potential damage to your business, reputation, and customer trust.
By regularly auditing and updating your DNS records, monitoring third-party services, and utilizing security features like domain locking and certificate transparency monitoring, you can effectively mitigate the risks associated with subdomain takeovers. Ultimately, prioritizing the protection of your subdomains is crucial for safeguarding your business and preserving the integrity of your digital assets.
Is this article interesting? Read more like these on our website’s cyber security page.
Faqs
Is a subdomain takeover illegal?
The legality of a subdomain takeover depends on whether it involves unauthorized access or exploitation of vulnerabilities, which may be illegal under cybercrime laws. Responsible disclosure, where vulnerabilities are reported without exploitation, is typically not illegal.
How does a subdomain takeover happen?
A subdomain takeover occurs when an attacker exploits misconfigured DNS records or abandoned subdomains, enabling them to gain control over the subdomain. By providing their content, attackers can redirect traffic, steal sensitive data, or launch further attacks from the compromised subdomain.
How does a subdomain takeover happen?
The top open-source free tool for detecting subdomain takeovers is Subdominator, a reliable and efficient command-line interface tool designed specifically for this purpose.