11 million Google Play app users got infected by a Necro Trojan, detected in two Android apps.
Key Takeaways
- Kaspersky reported that the Necro Trojan infected 11 million Google Play users.
- According to Google Play telemetry, this malware was embedded in two apps
- Google Play Store removed both apps, ensuring no more suspicious downloads.
- It spreads beyond the Play Store through unofficial websites.
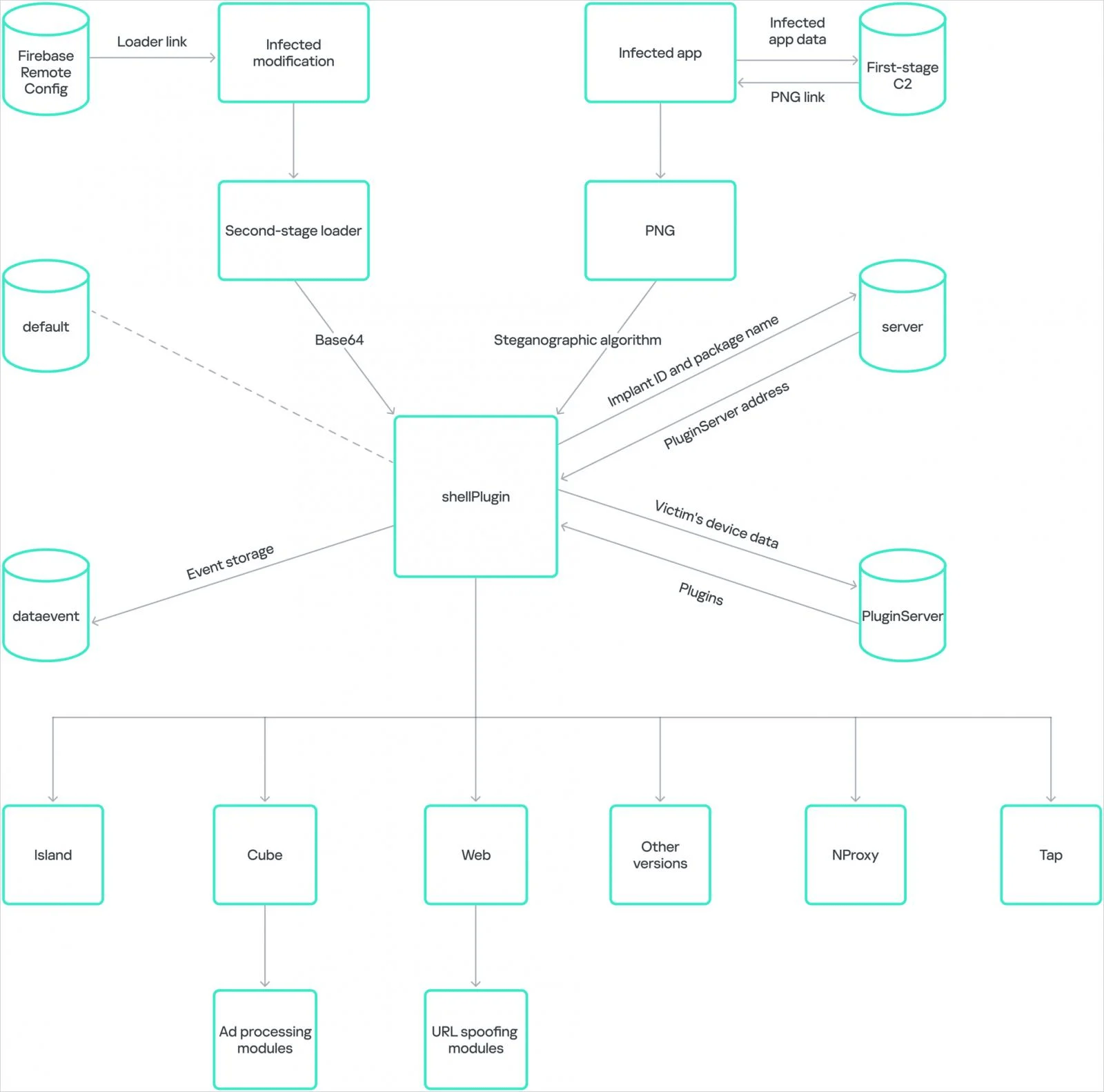
Kaspersky reported a new wave of the Necro Trojan virus that infected over 11 million Android devices through Google Play apps on September 23, 2024. According to Google Play telemetry, this malware was embedded in two apps: Wuta Camera, a popular photo editing program with over ten million downloads, and Max Browser, which has one million downloads.
Kaspersky, an anti-malware company, further said that Google Play Store removed both apps, ensuring no more threats. However, malware may still be lingering on the devices that installed them earlier.
Source: Kaspersky
Back in 2019, Necro Trojan also affected Cam Scanner, an Android PDF creator app, injecting malware into 100 million installations in Google Play. Today, necromancers have breathed fresh life into the old Trojan. A new variant infected the users via popular Google Play apps injecting rich features.
A threatening aspect of this malware is that it spreads beyond the Play Store. According to Kaspersky, modified versions of popular apps like Spotify, WhatsApp, and games like Stumble Guys, Melon Sandbox, Minecraft, and Car Parking are distributed through unofficial websites, further increasing its reach. Victims may unknowingly install these mods, which often promise enhanced functionality, but secretly install the trojan.
Once you install Necro, you give access to harmful operations such as displaying adverts to earn cash and installing programs without user authorization. It also employs infected devices as proxies for illicit communications.
The Necro Trojan embeds itself in advertising software development kits (SDKs) used by developers to integrate advertisements, frequently seen in modified versions of popular apps. These SDKs also use picture steganography to conceal dangerous payloads in seemingly harmless PNG graphics.
An SDK that integrates multiple advertising modules discovered transmitting device and application data to a command-and-control (C&C) server and receiving a payload concealed in a picture was included in the Spotify-infected mod.
On the other hand, Google’s Firebase Remote Config cloud service for command-and-control was used to inject malware into WhatsApp mod. Although it executed an identical payload.
Such threats warn us to remain secure and cautious while using popular apps like Telegram, WhatsApp, and Spotify. The rate of cybercrime is also increasing with modern security updates. Learn from the recent Telegram ban due to Russian threats that it’s not always a matter of malicious viruses but a concern for citizens’ security.
For more tech, AI, cyber security, and digital marketing insights, visit Daily Digital Grind. If you’re interested in contributing, check out our Write for Us page to submit your guest posts!