Ransomware is one of the most destructive form of cyberattacks in the contemporary era. It either encrypts users from their computers or encrypts information and requires pay in exchange for the restoration of access. Ransomware has grown from a minor annoyance to a worldwide pandemic in the last ten years. Ransomware spend is anticipated to blast past $265 billion by 2031, Cybersecurity Ventures forecasts.
The two major types of ransomware that rule the roost are locker ransomware and crypto ransomware. Both of them are risky, but they function in fundamentally different ways. Locker ransomware denies access to victims to their entire system, whereas crypto ransomware encrypts valuable files and data. It is essential for businesses, IT staff, and end-users to grasp this difference since it defines how an attack takes place, how recovery can occur, and what measures should be taken for prevention.
In this blog, we’ll dive into the difference between locker and crypto ransomware, explore real-world examples, and discuss which is more dangerous.
What is Locker Ransomware?
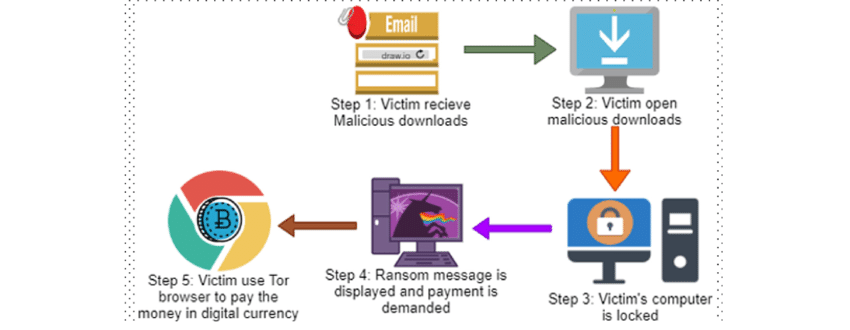
Locker ransomware is made to block access to a device. Rather than encrypting data, it blocks victims from access to a computer or cellphone by locking fundamental features like the operating system, keyboard, or mouse. Victims usually display a full-screen ransom note asking for money to be paid, with no alternate method of accessing the system.
The psychological frustration of locker ransomware is caused by total disruption. A locked computer grinds work to a standstill, and users can’t even try workarounds such as the use of unencrypted files.
How Locker Ransomware Works
- Infection usually starts with malicious downloads, drive-by sites, or phishing attachments.
- Once run, the malware takes over the system and blocks normal interaction.
- The victim receives a ransom note on the locked screen, at times even with a countdown timer to make it more pressing.
- Attackers demand payment in cryptocurrency, and attackers are firm that they would unlock the system once paid.
Examples of Locker Ransomware
One of the most famous was Reveton worm, which first manifested in Europe during approximately 2012. It was labeled as the “Police Trojan,” and it placed false warnings from the authorities, warning users that they were conducting pirating or the viewing of illegal content. Users were threatened with a fine, and in certain versions, the malware activated webcams to simulate the recording of the user. Although technologically primitive by today’s crypto ransomware standards, Reveton illustrated how fear and intimidation were potent weapons of coercion.
What is Crypto Ransomware?
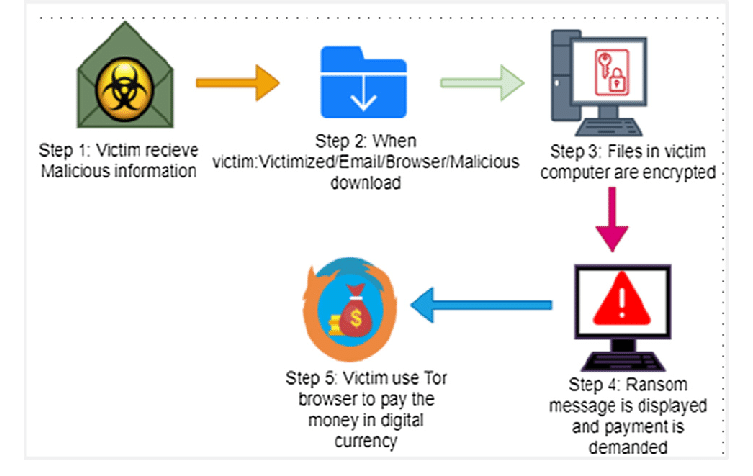
Crypto Ransomware, also referred to simply as file-encrypting ransomware, is the most prevalent and destructive form of ransomware today. Rather than securing the device, it encrypts valuable files and information so that they cannot be opened unless a decryption key is provided. Victims are able to use their devices, but their information files, images, databases, and backups are unavailable to them.
This is particularly devastating to organizations since it targets the core of business continuity information. Even if systems are still up and running, losing access to documents can shut down operations, make services more complicated, and do permanent damage.
How Crypto Ransomware Works
- Attackers gain access via phishing emails, bad files, remote desktop takeovers, or unresolved vulnerabilities.
- The malware quickly encrypts data with robust crypto algorithms like AES or RSA.
- They pay in Bitcoin or cryptocurrency and are presented with a ransom note on how to use that to buy the decryption key.
- The attackers today tend to use encryption in addition to data theft, threatening to release stolen data if not paid. This is double extortion.
Examples of Crypto Ransomware
The 2016–2017 Notpetya/Petya attacks are a case in point. Petya encrypted the Windows system Master File Table (MFT) and thus made all files unavailable. Its subsequent version, NotPetya, appeared in the form of ransomware but proved to be a wiping malware. NotPetya resulted in over $10 billion in damages, affecting such entities as Maersk and Merck and being one of the most expensive cyber attacks in history, Wired reports.
The other significant example is Locky, which was found in 2016. Spread via phishing emails masquerading as bills, Locky spread far and wide and encrypted more than 160 various file types. Cybersecurity experts explained how Locky became the most lucrative ransomware attack at that point by exploiting malicious email attachments.
Related Link: What is Crypto Ransomware? Complete Guide
Locker vs Crypto Ransomware: The Core Difference
Although both are types of ransomware, the difference between them lies in what they lock up. Locker ransomware will shut down the entire system so that the victim cannot even operate the machine. Crypto ransomware does permit the victim to keep using the machine while encrypting the victim’s most important files.
Practically speaking, this amounts to a different kind of effect. A locker attack is pure disruption; the system freezes up until ransom is paid or the machine restored. A crypto attack, on the other hand, can seem less critical at first because the system keeps running, but the eventual effects are always worse. Losing valuable business files, financial records, or research data can damage much more financially and reputationally than occasional downtime.
Which is More Dangerous?
Both locker and crypto ransomware are bad, but crypto ransomware is more commonly viewed by most specialists as a larger threat in the long term.
- Locker ransomware can usually be fixed by re-installing the operating system or re-imaging the machine. Although painful, the damage can be limited if there are backups and systems can be reassembled fairly quickly.
- Crypto ransomware usually leads to irretrievable data loss if decryption keys are not accessed. Even if payment is made, there is no assurance that the attackers will publish an effective key. Additionally, the double extortion trend implies that sensitive information may also be leaked or sold, which presents legal and reputational threats.
For organizations with intense use of proprietary information, the financial cost of a crypto ransomware attack can be catastrophic. NotPetya proved that losses can rise into the billions, reaching international supply chains and industries.
How to Prevent Ransomware Attacks
The most encouraging news is that locker and crypto ransomware both can be prevented through proactive security controls. Cybersecurity stewards like CISA recommend a layered approach to defense:
1. Keep Systems Patches Up to Date
Ransomware tends to attack older software vulnerabilities. Keep patches and updates for operating systems, programs, and firmware up-to-date to address security weaknesses.
2. Increase Authentication
Utilize unique, robust passwords for all accounts and implement MFA. Most ransomware gangs abuse weak or stolen credentials, especially remote desktop scenarios.
3. Train Users against Phishing
The majority of ransomware came via phishing emails. Educate staff to identify dodgy links and attachments. Phishing simulation campaigns are an effective means of reminding awareness.
4. Back Up Data Securely
Backups are still the greatest protection against crypto ransomware. Keep backups offline and in the cloud, and regularly test recovery procedures. It’s common for attackers to go after network-connected backups, so offline or air-gapped replicas are essential.
5. Install Advanced Security Tools
Use endpoint detection and response (EDR) solutions that can detect unusual behavior such as mass file encryption. Firewall, intrusion prevention systems, and antivirus software should all be part of a layered defense.
6. Segment Networks
Separate critical systems from less sensitive ones to prevent ransomware from spreading laterally. Implement the principle of least privilege so that compromised accounts cannot access everything.
What to Do if You’re Infected
If your organization or device has been attacked by ransomware, the following actions need to be done as soon as possible:
- Remove the device from the network to stop further spreading.
- Preserve evidence for forensic recovery and law enforcement.
- Check for decryptors on No More Ransom and other reputable sources. There are free solutions offered for most legacy ransomware versions.
- Recover from backups only after ensuring the system is clean.
- Do not pay ransom whenever possible. Law enforcement agencies, including Europol and the FBI, advise against paying because it funds more criminal activity and offers no guarantee of recovery.
Related Link: What is a Ransomware Attack? (2025 Guide)
Final Thoughts
Ransomware is not something of the future, it is one of the biggest cybersecurity threats of today. Locker ransomware and crypto ransomware both extort victims, but they do it in various ways and with varying repercussions.
- Locker ransomware denies access to the whole system, with the instant disruption.
- Crypto ransomware encrypts valuable files, with permanent loss of data and threats of extortion.
Of the two, crypto ransomware is worse due to its possibility of permanent data loss and data breaches.
The strongest defense is active defense patch machines, implement strong authentication, train personnel, and have good, offline backups. When these are supplemented by excellent detection and response, they can severely mitigate the risk of being struck by either variety of ransomware.
To explore more insights like this, visit our Cyber-security Page.
If you’re passionate about tech, networks, and digital infrastructure, Write for Us and share your voice with our audience.