In the hyper-connected era, cyber-threats only grow more advanced and among these, botnets are an unparalleled and ubiquitous cyber-criminal weapon. A botnet is in some senses jargon, but its impact is far from theoretical from hijacking individuals’ own devices to launching massive attacks on global infrastructure. In this article, we’ll unpack exactly what a botnet is, how it works, what it’s employed for, and most crucially, how you can defend yourself.
The term botnet is derived from robot + network. A botnet is actually a collection of compromised devices, usually computers, cell phones or IoT (Internet of Things) devices that have been compromised (unaware to the owner) and remotely controlled by an attacker (also called a bot herder). The compromised devices are bots or zombies.
The reasons botnets are particularly frightening are that they are scalable and silent. A single attacker can utilize hundreds, thousands or even millions of infected machines to carry out automated assaults that would be impossible (or prohibitively expensive) for a single machine to accomplish. They can steal data, hijack systems, launch denial of service attacks, spread malware, or sell access to other malicious users.
How a Botnet Works
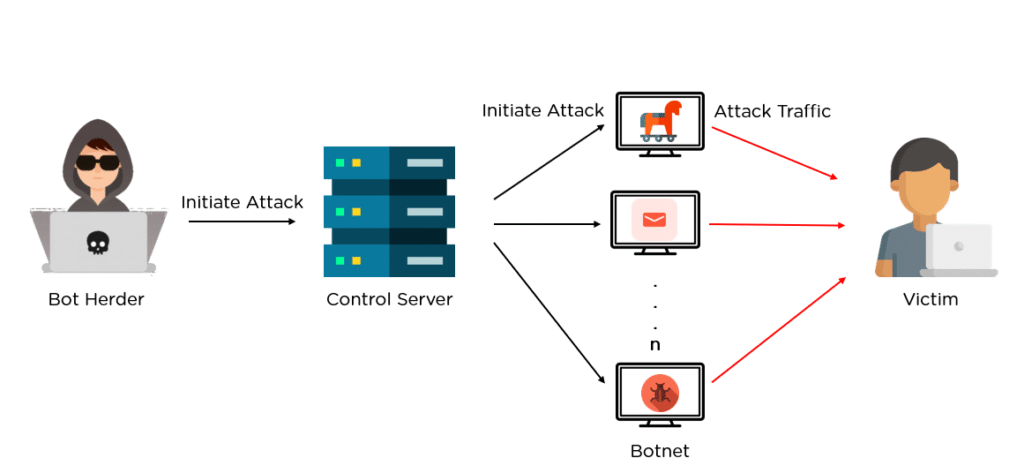
To understand the effect of a botnet, it is useful to walk through the overall process of how one is created and operated:
Stage 1: Exposure & Infiltration
The attacker finds vulnerabilities: outdated software, weak passwords, insecure IoT, phishing email, drive-by downloads, etc. For example, a user may click on a malicious file, browse an infected website, or install an inexpensive smart-device with no security patches.
Stage 2: Infection
Once the vulnerability is exploited, malware is transferred onto the target device. This malware allows the attacker to take over the device and turn it into a “bot” connected to the botnet waiting for instructions.
Stage 3: Activation & Command
The bot herder consolidates the bots into a network and issues instructions via a command-and-control (C & C) scheme. The bots execute tasks spamming, attacking, mining crypto, scanning for other exposed devices, etc.
This scheme allows one attacker to expand exponentially; from one machine to thousands, turning innocent residential routers, smart cameras or phones into a node of an global attack network.
Common Devices Targeted by Botnet
Almost every internet connected device is a potential bot. The attack surface has now spread well beyond traditional desktops and laptops:
- Windows, MacOS, and Linux desktops and laptops remain venerable targets because of their universality and data on them.
- Mobile devices (smartphones and tablets) become increasingly targeted as mobile use spreads around the world.
- Network appliances such as routers, modems and servers can be hijacked and converted into bots or proxies.
- Smart home devices (cameras, speakers, thermostats), wearables, car infotainment systems, and IoT devices are especially vulnerable because many ship with poor default passwords, poor update regimes and minimal security by design.
Low-cost, low-security IoT devices make up the bulk of the purchases made, which means bot herders now have an ever-growing reservoir of potential bots at cheap costs.
How Hackers Control a Botnet
Command and control (C & C) infrastructure lies at the heart of botnet activity. The bot herder uses it to instruct bots and coordinate activities. There are two common architectures:
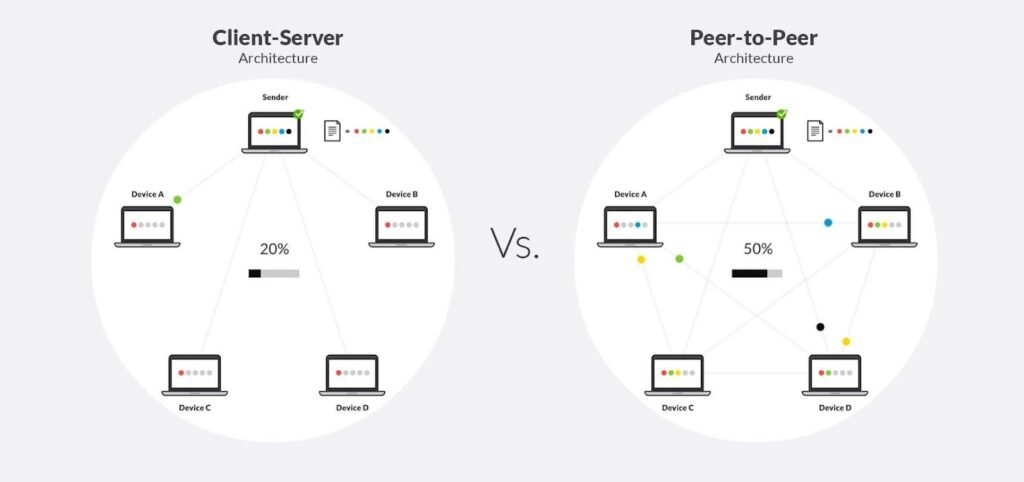
- Centralized (client-server): A master server (or smallest number of servers) instructs all bots. Easy to implement, but likewise one point of failure.
- Decentralized (peer-to-peer, P2P): All the bots can communicate with each other; commands get propagated through the network without a central server. This topology is extremely resilient and harder to track.
Botnets today typically employ P2P or hybrid topologies, as well as encryption, proxy networks and evasion mechanisms to remain undetected and untaken.
What Are Botnets Used For?
Botnets are an instrument of adaptability for cyber-thieves and they’re used in many different malicious activities. Some of the most common applications are:
- Distributed Denial-of-Service (DDoS) attacks: Overwhelm a site or service with massive traffic spikes, knock out servers or make services unavailable. As an example, in Q1 2025 overall DDoS attacks rose by 110% compared to Q1 2024.
- Spam and phishing attacks: Spammers send unsolicited bulk emails, typically containing malware or links to credential harvesting.
- Data theft/credential harvesting: Bots steal a user’s information, login credentials, or scan for weaknesses in other PCs owned by the victim.
- Cryptomining / cryptojacking: Compromised devices are employed to mine cryptocurrency without the permission of the user.
- Leasing botnet access: Bot herders lease or sell access to the botnets to other malicious actors, enabling “botnet-as-a-service.”
- Click fraud / ad fraud: Bots fake false clicks in order to sell ad revenue, generate spurious views or profit scammers.
- Malware delivery: Botnets can distribute additional malware, plant backdoors, or create platforms for follow-up campaigns.
Types of Botnet Attacks
Whereas “botnet” refers to the network, it is the attacks launched via botnets that hit the headlines. Some common types of attacks:
- DDoS (Layer 3/4 and Layer 7): Raw volumetric or app-layer, targeted attacks. Cloudflare stopped 7.3 million DDoS attacks in Q2 2025, already 130 % of all attacks in the whole 2024.
- Phishing/spam: Bots make email or social-media messaging convincing in scale, imposing the guise of trusted sources to steal logins or install malware.
- Brute-force / credential stuffing: Breached machines are used to spam services with login attempts using stolen credentials.
- Malware/ransomware spread: A significant botnet can be used to spread ransomware far and wide, causing enormous financial loss.
- Click/Ad fraud: Bots mimic human users, click on ads, make fake accounts and produce illicit revenue.
- Cryptojacking: Hijacking idle CPU/GPU resources of bots for mining cryptocurrencies, typically not detected.
- IoT-based botnets: Like Q1 2025 witnessed the biggest DDoS botnet discovered to consist of 1.33 million devices (compared to some 227,000 in the biggest 2024 botnet).
The magnitude and scope of these attacks make smaller organisations and individual users possible targets or incidental damage.
Botnet Threat Landscape
Here are some current numbers to illustrate just how serious of a botnet threat there is:
- Based on F5 Labs’ “2025 Advanced Persistent Bots” report, analyzing more than 200 billion web/API transactions revealed bot/automation attacks to be ongoing and continually changing.
- Simple, high-volume bot attacks rose to 45% of all bot attacks in 2024, from 40% in 2023 powered in part by easily accessible AI-automation tools.
- The global botnet detection market totaled USD 730 million in 2024 and is anticipated to grow at a rate of 30 % throughout the period from 2024 to 2031, with projected growing demand for botnet defense.
- On the malware front, in Q1 2025 about 6.46% of user computers across the globe were affected by one or more web-based malware attacks.
These numbers tell us two things, botnet attacks are increasing in number, complexity and scale; and the defenders must keep escalating their capabilities in response.
How to Stay Protected from Botnets
Because botnets rely on compromised machines, defense starts with making your machines hard to hijack. Below are helpful tips:
- Use strong, unique passwords on all devices, routers, smart devices and IP cameras. Use anything but defaults like “admin/admin”.
- Update firmware and software on all devices. Most botnets exploit known vulnerabilities in unpatched devices.
- Buy devices only from experienced vendors with a track record of security patches. Cheap or no-brand IoT devices do not typically have fundamental protections in place.
- Change default admin settings and passwords on any device that is network-connected smart home equipment, cars, wearables.
- Don’t open email attachments, links and downloads. The majority of botnet infections initiate via phishing or drive-by downloads.
- Install proper antivirus/antimalware software that covers all your endpoints (PC, phone, tablets) and has real-time scanning turned on.
- Segment the network; use a guest network to isolate IoT devices from each other and your main devices.
- Monitor for unusual device activity; high network traffic, strange slowdowns, mysterious processes or suspicious log-in attempts can signal botnet behavior.
- Disable remote admin access where feasible. If remote access to a device is necessary, lock it down via VPN, multi-factor authentication (MFA) and robust credentials.
- Educate users in your organization or at home; human behavior tends to be the weakest link. Make sure people are aware of phishing threats, suspicious links and the reason why devices should stay updated.
Defense is preferable to cure once a device has been breached with a botnet, remediation is far more time-consuming and may need re-installation or even replacement.
Final Thoughts
In a world where devices are connected everywhere even in our own homes, our vehicles and our shared home appliances the reach and potential of botnets have grown multiple millions of times. What began as arrays of compromised desktops has grown to be massive global armies of stolen devices driving DDoS attacks, spreading ransomware, mining cryptocurrencies and more.
But the fact is, you can reduce your risk. By understanding how botnets work, being cognizant of the danger, and exercising defensive hygiene on every device that you own or manage, you become a less appealing target. You also stop evil players from having the raw materials (your device) they need to build their botnet armies.
Be vigilant, be aware and make sure your devices are allies, not part of another’s cyber army.
To explore more insights like this, visit our Cyber-security Page.
If you’re passionate about tech, networks, and digital infrastructure, Write for Us and share your voice with our audience.
Related Link:
- Cyber-Security: Types, Threats & How to Stay Safe
- What is a Botnet Attack in Cyber Security?
- What Is a Denial of Service Attack? Complete Guide
- What is a Ransomware Attack?
FAQs
How do I know if my device is a part of a botnet?
Signs of botnet infection may include usually slow performance, heavy network usage when you’re not on, repeated system crash, strange processes running in background, unusual log-in or connection attempts, or devices behaving in a strange manner (e.g. overheating, blinking lights). If you experience one or more of these, run a full malware scan and review attached devices.
Can antivirus software stop Botnet infections?
Yes, reputable antivirus software is valuable in detecting and stopping malware trying to turn your device into a bot. But antivirus is not enough since the majority of botnet infections are aimed at unpatched vulnerabilities, weak credentials or insecure IoT devices. A layered defence of updates, safe passwords, network segregation and user education are required for total protection.