In today’s hyperconnected world, information flows constantly between devices, individuals, and cloud services. Network security is the essential set of techniques, technologies, and policies that protect these communications from interception, misuse, or disruption. According to IBM’s 2025 Cost of a Data Breach Report, the global average cost of a data breach has reached USD 4.44 million, highlighting why strong network security is no longer optional but critical.
- Why Network Security Is Important
- How Does Network Security Work?
- Key Network Components & Control in Network Security
- 1. Firewalls
- 2. Intrusion Detection and Prevention Systems (IDS/IPS)
- 3. Anti-Malware & Antivirus
- 4. Access Control & Network Access Control (NAC)
- 5. Virtual Private Networks (VPNs) & Encrypted Tunnels
- 6. Email Security & Anti-Phishing
- 7. Web & URL Filtering / Web Security
- 8. Application Security
- 9. Cloud / Hybrid Security
- 10. Wireless / Wi-Fi Security
- 11. BYOD & MDM Controls
- 12. Network Segmentation & Microsegmentation
- 13. Sandboxing & Threat Emulation
- 14. Honeypots / Honeynets
- Advantages of Network Security
- Network Security Future Trends & Challenges (2025+)
- Best Practices for Building a Strong Network Security Posture
- Real-World Attack Examples & Lessons
- Final Thoughts
Network security admits only legitimate users and devices to access networked resources, keeps data private and uncorrupted, and enables systems to be accessed when necessary. In reality, network security comprises three main objectives, referred to as a whole as the CIA Triad:
- Confidentiality: The prevention of the unauthorized revelation of confidential data.
- Integrity: The prevention of data from being processed or altered through error.
- Availability: Getting systems and services ready so that they are available to users who have been authorized to use them.
Network security is a specialized area within the overall discipline of cyber-security but addresses protecting the network infrastructure itself and information flowing over it.
Why Network Security Is Important
Growing cyber attacks, As cyber attackers become more advanced in their tactics like multi-step attacks, AI-based malware, supply chain atacks, and cloud attacks networks are their number-one target.
- Breach expenses & reputation loss: One breach can cost tens of millions of dollars in fines, attorney fees, and lost customer confidence.
- Business continuity & availability: Downtime like DDoS or network intrusion can bring operations to a halt.
- Regulatory compliance: Various companies fall under the jurisdiction of regulations such as GDPR, HIPAA, PCI-DSS, etc., where network protection is needed in most instances.
- Cloud adoption and remote work: With cloud apps and remote workers, trust boundaries evaporate leaving tight network security policies mandatory.
How Does Network Security Work?
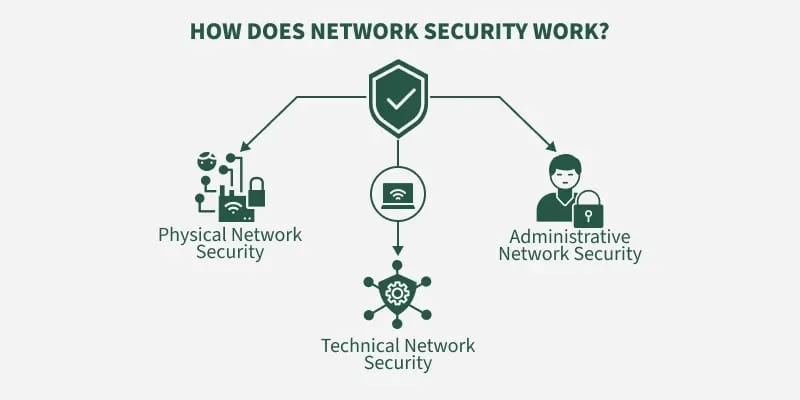
Network security is not a product, but a layered defense strategy employing people, processes, and technologies to implement numerous layers of protection against attack. Each layer examines, filters, and monitors traffic per policy, and they all collaborate to reduce risk.
There are some professional models:
- Defense-in-Depth: Having a greater than one layer of defense mechanisms that overlap so even if one becomes breached, others remain to protect the system.
- Zero Trust: Enforce a “never trust, always verify” policy to trust no user, device, or request until verified.
- Adaptive / Dynamic Security: New systems learn dynamically, often with machine learning to recognize suspicious activity (e.g. adaptive firewalls).
Traffic is analyzed at multiple points:
- Edge / Perimeter: firewall, gateways, VPN concentrators
- Internal Segments: VLANs, microsegmentation, internal network segments
- Host / Device: Devices and apps, encryption
By deploying controls on every layer, network security limits the attack surface area and makes it such that even if one layer is evaded, following layers can catch or delay threats.
Key Network Components & Control in Network Security
Below are the critical elements you ought to have or be aware of when you start with network security:
1. Firewalls
Firewalls are gatekeepers, screening incoming and outgoing traffic according to rules predefined in advance (e.g. allow/deny based on IP address, port, protocol). Firewalls may be:
- Network-based (between network segments)
- Host-based (Individual-by-Individual)
Next-generation firewalls further add application awareness, intrusion prevention, and user identity integration.
Read More: What is a Firewall?
2. Intrusion Detection and Prevention Systems (IDS/IPS)
- IDS only monitors network traffic and alerts when abnormal patterns are observed.
- IPS is more active in the sense that it blocks or reduces the attacks actively.
They are anomaly-based, signature-based, or hybrid detection mechanisms-driven.
3. Anti-Malware & Antivirus
Although a primary endpoint security, antivirus software also assists at the network level (e.g., attachment scanning or file transfers) to avoid the spread of viruses, Trojans, worms, and other malware.
4. Access Control & Network Access Control (NAC)
Access control restricts network access to legitimate, authenticated, and authorized users or devices. NAC deployments enforce identity-based, device posture-based, and geographically based policies. Noncompliant or untrusted devices are quarantined or blocked.
5. Virtual Private Networks (VPNs) & Encrypted Tunnels
VPNs utilize IPsec or SSL/TLS protocols to create secure, encrypted tunnels across untrusted media (e.g., the Internet), particularly applicable for remote access.
6. Email Security & Anti-Phishing
Email is the main attack vector for social engineering, phishing, and malware. Email security software blocks spam, blocks malicious attachments or links, and blocks DMARC/DKIM/SPF policy violations.
7. Web & URL Filtering / Web Security
Web security software blocks malicious web sites, blocks malicious web content, and monitors web traffic. It does both of those at on-premises gateways and within cloud architectures.
8. Application Security
Secure web applications, APIs, and backend applications prevent intrusion via software vulnerabilities (SQL injection, cross-site scripting, buffer overflows, etc.). Secure coding integration, vulnerability scanning, runtime application protection is essential.
9. Cloud / Hybrid Security
With workloads and data stored in the cloud by organizations (IaaS, PaaS, SaaS), they need to be secured where there are network connections. Cloud firewalls, microsegmentation in the cloud, workload-level security, hybrid environment visibility are some controls.
10. Wireless / Wi-Fi Security
Wireless networks are simpler to tap into and access illegally. Employ robust encryption (WPA3), SSID concealment, MAC filtering, and persistent monitoring.
11. BYOD & MDM Controls
Personal and mobile devices are bringing ever more connections into enterprise networks. Regulating which devices can connect, enforcing security policies, and quarantining high-risk devices is needed.
12. Network Segmentation & Microsegmentation
Segmenting a network into sub-zones constrains attackers’ lateral movement. Microsegmentation between data centers or between cloud workloads introduces an additional layer of controls.
13. Sandboxing & Threat Emulation
Suspect code or files are run in isolated environments (sandboxes) to identify and ascertain malicious activity before entry to live systems.
14. Honeypots / Honeynets
Impostor systems or networks created to lure attackers. Attacker behavior analysis provides insight into how threats can be redirected away from actual assets.
Advantages of Network Security
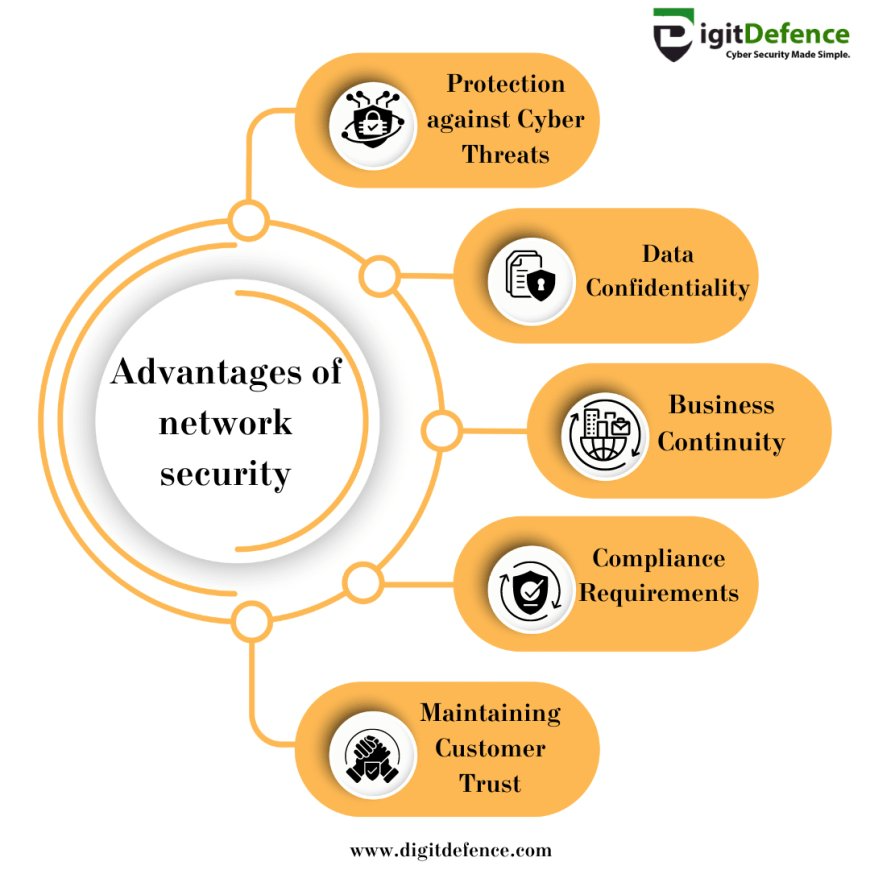
- Preservation of data privacy & protection of sensitive data.
- Minimized economic and legal risk by compliance & violation avoidance.
- Safeguards against disruption of operations & repels attacks.
- Building corporate brand & customer trust.
- Enabling secure adoption of future technologies (cloud, IoT, remote work)
Network Security Future Trends & Challenges (2025+)
Get ahead with the knowledge about future threats and new technologies. A few of the most important trends that define network security today and in the near future are:
- AI & Machine Learning for Threat Detection & Response: Increasing numbers of security products employ AI/ML to identify threats as anomalies in network traffic, to automate response, and to forecast emerging vectors of attack.
- Multivector & Multistage Attacks: Rather than a single exploit, threats are employing concurrent or sequential attacks on multiple vectors (phishing + endpoint exploit + lateral movement) as a means of going around defenses.
- Zero Trust Becoming the New Norm: Zero Trust implementations (no trust internally or externally) are normal today, particularly for multi-cloud and hybrid environments.
- Quantum-Safe / Post-Quantum Cryptography: Quantum computing looked to the future, and classical cryptography was made obsolete. Organizations now deploy quantum-resistant cryptosystems.
- Shadow AI & Generative AI Threats: Unauthorized or unapproved AI models (referred to as “shadow AI”) controlled by attackers or users can expose information and introduce new attack surfaces. Generative AI is employed to create phishing or impersonation attacks that look more authentic.
- Supply Chain & Third-Party Risks: Attackers take advantage of vendors, dependencies, or software supply chains to access otherwise secured networks.
- Rapid Credential Theft & Account Compromise: Credential theft is growing and attackers increasingly use stolen credentials to establish legitimate access.
- Adaptive / Real-Time Firewalls & Protection: Dynamic retrainable firewalls learn from actual traffic patterns to prevent new threats, new research says.
Best Practices for Building a Strong Network Security Posture
- Asset Inventory & Network Mapping: Know all devices, apps, and connections on your network.
- Solid Authentication & Identity Management: Implement multi-factor authentication (MFA), least-privilege access, role-based access control (RBAC).
- Regular Updates, Patches & Vulnerability Management: Breach is the most prevalent vector of vulnerability.
- Security Awareness & Training: Humans are most often the weakest link train personnel on phishing, secure use, and policy.
- Least Privilege & Microsegmentation: Lock down access so that users/devices only get to look at what they require.
- Continuous Monitoring & Threat Hunting: Utilize tools (SIEM, EDR, NDR) to identify anomalies and actively hunt for threats.
- Incident Response & Disaster Recovery Planning: Avoid playbooks, backups, and procedures in writing to be in short supply when disaster strikes.
- Encrypt Data in Transit & At Rest: Use TLS, IPsec, VPNs, and secure key management.
- Redundancy & Failover Mechanisms: Cause networks to become immune to outages or attacks.
- Vendor Security & Third-Party Auditing: Make third-party software, services, or vendors adhere to robust security standards.
Real-World Attack Examples & Lessons
- Ransomware attacks: They come in on phishing or insecure services, encrypt data, and request payment.
Read More: What is a Ransomware Attack?
- DDoS attacks: Extremely high network traffic overpowers servers and denies service to legitimate users.
- Data exfiltration: They tunnel data out as encrypted traffic disguised as ordinary traffic.
- Cloud misconfigurations: Storage buckets or access policy misconfigured leak data.
- Credential-based attacks: Hackers use weak or stolen credentials to pivot laterally throughout networks.
From these examples, a few lessons are learned: layered defenses, least privilege, active monitoring, and rapid response are crucial.
Final Thoughts
Network security is a key column in the cybersecurity plan of any enterprise. It protects the pipe’s information transmitted via them, keeps systems on an even keel, and keeps the attackers at bay from breaching infrastructure. With threats developing to become sophisticated AI, multistage attacks, supply chain attacks, and quantum computing around the bend in the future network security must grow and change as well.
By having layered defenses, identity-first practices, vigilance, and safe design, organizations can keep ahead of the attackers and remain trustworthy to customers, compliance regulators, and stakeholders.
Would you have me create a visually focused version with infographics or divide this up into a tidy finished draft for publication? I can do that next if you prefer.
To explore more insights like this, visit our Cyber-security Page.
If you’re passionate about tech, networks, and digital infrastructure, Write for Us and share your voice with our audience.