The OWASP (Open Web Application Security Project) Top 10 is a list of the most critical security risks that affect web applications. This list is updated every few years to help developers and security professionals understand the biggest threats and how to avoid them.
The latest OWASP Top 10 list is for 2024. It focuses on keeping websites and apps safe from hackers and other security problems.
In this guide, we will explain what the OWASP Top 10 2024 is and break down each security risk in simple terms. By the end, you’ll have a good idea of the common dangers that web applications face and how to protect your own website or application from them.
What is OWASP?
OWASP is a non-profit organization that provides free resources for web security. Their goal is to help people understand the risks of web applications and how to build safer ones. One of their most popular projects is the OWASP Top 10 list. It has become a standard for web developers and security experts all around the world.
The OWASP Top 10 doesn’t just list the security risks; it also gives advice on how to fix them. If you’re a developer or work with web applications, it’s important to know these risks so you can protect your users’ data.
Why is OWASP Top 10 Important?
The OWASP Top 10 is important because it shows what kinds of attacks are happening the most and where apps are weak. Hackers often look for these common weaknesses to steal data, take control of websites, or cause other problems.
By knowing about these risks, developers can write code that is more secure. It’s like having a checklist to help you avoid making common mistakes.
Now, let’s look at the top 10 risks for 2024.
The OWASP Top 10 Risks for 2024
1. Broken Access Control
Broken Access Control happens when users are able to do things they shouldn’t. For example, a regular user might be able to access admin features because the website doesn’t properly control what each user is allowed to do. This can let attackers change settings, steal data, or take control of the site.
To avoid this, developers need to check permissions carefully and make sure users only have access to what they should.
2. Cryptographic Failures
Cryptographic failures happen when sensitive data isn’t protected properly. This can happen if encryption methods are weak or if sensitive information is not encrypted at all. Without good encryption, attackers can easily steal or change important data.
To fix this, use strong encryption methods to protect all sensitive data like passwords, credit card numbers, and personal information.
3. Injection Attacks
Injection attacks happen when hackers send bad data into a system, tricking it into running harmful code. SQL Injection is a well-known example of this. If a website doesn’t check inputs carefully, hackers can add code that can steal data or even destroy the database.
To stop injection attacks, always validate user inputs and use safe coding practices.
4. Insecure Design
Insecure Design is when a website or application is built in a way that leaves it open to attacks. This happens when security isn’t considered during the design phase. Developers may rush to build a website without thinking about how to protect it, leading to weaknesses that hackers can exploit.
To avoid this, security needs to be part of the design process from the start. Developers should think about possible risks and build in protections as they create the application.
5. Security Misconfiguration
Security Misconfiguration happens when the settings of a website or application are not secure. This could be something as simple as using default passwords or leaving important settings turned off. These misconfigurations give attackers an easy way to get in.
To prevent this, always check your settings and configurations. Make sure they follow best practices for security.
6. Vulnerable and Outdated Components
Using outdated software or components is like leaving the door wide open for hackers. Old versions of software often have known weaknesses that attackers can exploit. If you don’t update your software, you leave your website or application at risk.
To avoid this, keep all your software up to date and make sure you’re using components that are supported and secure.
7. Identification and Authentication Failures
Identification and Authentication Failures happen when websites or apps don’t properly verify users’ identities. This could mean weak passwords, no two-factor authentication, or poor session management. If an attacker can break through the login process, they can pretend to be someone else and cause harm.
To fix this, use strong passwords, enable two-factor authentication, and manage user sessions carefully.
8. Software and Data Integrity Failures
Software and Data Integrity Failures occur when an application’s code or data is changed without proper checks. This can happen if a hacker tampers with the software updates or data used by the application. If no checks are in place, the application can run harmful code or produce wrong results.
To prevent this, always use secure methods to verify software updates and data integrity.
9. Security Logging and Monitoring Failures
Logging and Monitoring Failures occur when security events are not properly recorded or monitored. If there are no logs or no one checks them, attacks can go unnoticed. For example, if someone tries to hack your website and you don’t have good logs, you may not know until it’s too late.
To avoid this, set up proper logging and monitoring systems to track suspicious activity and respond quickly.
10. Server-Side Request Forgery (SSRF)
Server-Side Request Forgery (SSRF) happens when an attacker tricks a server into making requests to an unintended location. This can lead to the server sharing sensitive information or performing actions it shouldn’t. SSRF attacks usually happen when user inputs are not properly validated.
To fix this, always validate and sanitize inputs that deal with URLs and external requests.
Read also: How to Protect Your Website from Subdomain Takeovers?
How to Protect Against OWASP Top 10 Risks
Now that we’ve looked at the top 10 risks, here are a few simple tips to protect against them:
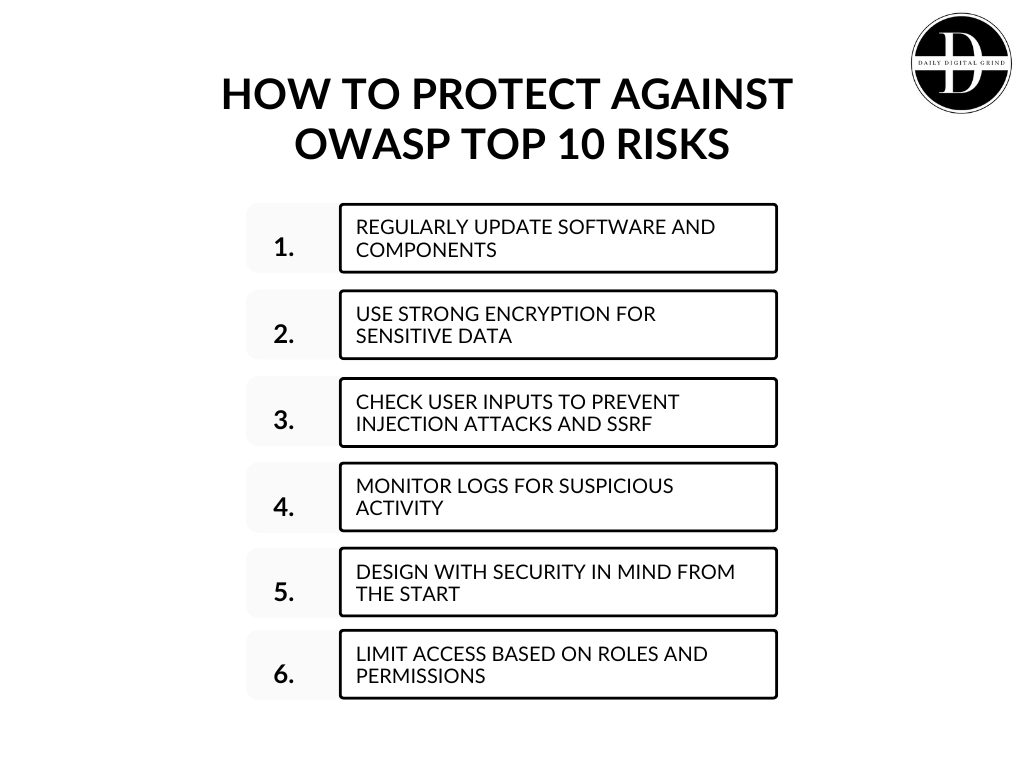
- Regularly update software and components to fix known security issues.
- Use strong encryption for sensitive data.
- Check user inputs to prevent injection attacks and SSRF.
- Monitor logs for suspicious activity.
- Design with security in mind from the start.
- Limit access based on roles and permissions.
Conclusion
The OWASP Top 10 is a great guide for keeping your web applications safe. By understanding the most common risks and how to fix them, you can build stronger, more secure websites and apps. Whether you’re a developer or just someone interested in web security, knowing about the OWASP Top 10 is a big step in protecting yourself and your users.
If you want to learn more about cybersecurity and how to keep your web applications safe, check out Daily Digital Grind. It’s a great resource for staying up-to-date on the latest security tips and tricks. You’ll find everything from beginner-friendly guides to expert advice on how to protect your digital life. Stay secure!
FAQs
What is the OWASP Top 10?
The OWASP Top 10 is a list of the most critical security risks that affect web applications. It’s created by the Open Web Application Security Project (OWASP) to help developers and security experts understand the biggest threats to web apps and how to protect against them.
Why should developers care about the OWASP Top 10?
Developers should care about the OWASP Top 10 because it highlights the most common security risks found in web applications. By understanding these risks, developers can write safer code, protect user data, and prevent attacks like hacking, data theft, or account takeover.
How can I protect my website from OWASP Top 10 security risks?
To protect your website, you should regularly update your software, use strong encryption, validate user inputs, set up proper access controls, and monitor security logs for suspicious activity. Following best practices for web security can reduce the risk of attacks.